
- May 26, 2020
Minor release, major step!

Cybersecurity for SAP©
Our SecurityBridge platform is a holistic cybersecurity suite for Netweaver, fully integrated with SAP. Based on the NIST Framework, SecurityBridge enables SAP customers to Identify, Detect and Respond to cyber threats. Don’t wait until your company becomes the victim of a cyber attack, protect yourself now.
Summary Vers. 4.73
The following new features were released on Friday 22nd May 2020. This version is a minor release update after the recent 4.7 major release that contained the Security & Compliance Monitor.
- A brand new HyperLogging module has been released, which enables you to log all events of a particular user across your SAP landscape.
- New incident management API’s have been released
- Java Audit Log support
- Detection pattern updates for SAP Patch Day - May'20
- Confirm the end of system maintenance
- Improved user-experience with smart navigation to related checks
- Predefined event filters
Highlight
HyperLogging
Event Monitor
HyperLogging enables SecurityBridge to track all actions of a particular account, across all systems of your landscape. HyperLogging (Blog) can be activated automatically as a response to a security-critical event. E.g. when SecurityBridge finds a SAP_ALL assignment it will start recording all actions of the account in focus, during, and after the critical authorization assignment. This enables you to have full and audit compliant insight into all actions executed. In an upcoming major release, a dedicated HyperLogging Fiori app will become available.
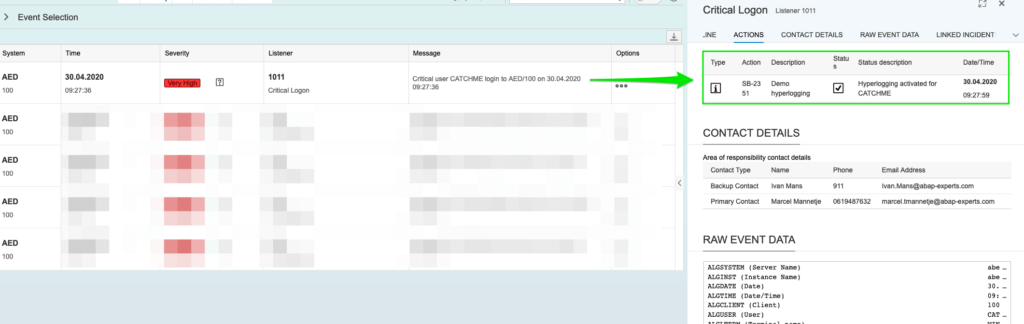
Highlight
Saved Searches
Event Monitor
The SecurityBridge Event Monitor now allows end-users to store selection filters for personal or global use. It is possible create a set of saved searches.
Highlight
Announce System Maintenance
Threat Detection
At times an SAP instance goes for regular maintenance a series of admin actions are conducted that trigger security events. These are valid but they shall not trigger investigation actions within the Security Operation Center. SecurityBridge now allows to announce a maintenance period so events can be suppressed during this timeframe. Security relevant actions remain documented without generating alert fatigue.
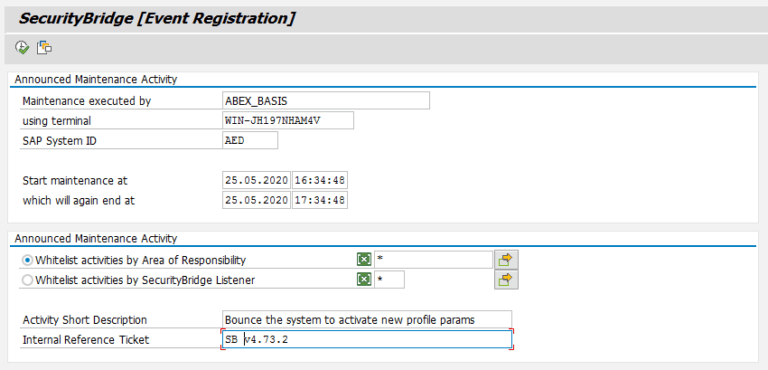
... and more
Detection Pattern updates
after SAP Patchday May 2020
Identification patterns for vulnerabilities published by SAP Patchday in May are already included within our latest SecurityBridge release. A good number of potential exploits can be identified, which will help prioritizing the implementation of patches.
Connectivity API
Incident Management
A set of API services have been released for integrating ITSM Solutions with the SecurityBridge Incident Management application. For details please do check the online knowledge base.
JAVA Audit Log
Threat Detection for SAP©
The Audit Log for JAVA agents now has a dedicated event listener. SAP NetWeaver JAVA instances can therefore easily be connected with your Security Operation Center. JAVA events have the exact same capabilities as events originating from an ABAP based system, offering full integration with the action framework.
Learn more about SecurityBridge here…


Sales & Partner Manager – APAC Market (Singapore)

Pre-Sales Consultant – APAC Singapore

SAP Security Patch Day – April 2024

The ‘Rapid Reset Attack’ – an SAP perspective





