
- May 22, 2020
SAP Identity Theft

Here are some simple suggestions to preserve your account from SAP identity theft:
Safeguard your information, both online and offline
Do not reuse passwords. Using strong and unique passwords for each account is the easiest and most effective way to avoid becoming a victim of identity theft. Mix upper and lowercase letters, use symbols, and create sufficiently long passwords for each of your accounts.
Log out when you are finished
Never leave an unlocked terminal unattended. If you do not log yourself out, you may be automatically logged out by the SAP instance after a period of inactivity. Attackers only need seconds to perform an unauthorized action in your name.
Keep your computer protected
Keep your computer and mobile devices protected by virus scanners, anti-malware, etc.
Be constantly vigilant
Report suspicious activity immediately. If you spot anything out of the ordinary – any unauthorized account activity – report it right away. You are less likely to be seriously impacted by identity theft if you discover and report the incident shortly after the security breach.
What is the impact of a stolen identity?
As with stolen credit or ID cards, the attacker may use the authorizations of the stolen identity for fraud, data extraction or manipulation. If the IT Security Department detects anomalies in SAP, all evidence points to the owner of the identity. The attacker stays anonymous. To measure the size and impact of an identity theft case, two questions will need to be answered:
- How much time did the attacker have to use the stolen identity?
- Did the attacker access an SAP account having super rights?
These questions can easily be answered when an intrusion detection system is guarding your SAP systems.
How to identify a stolen identity?
The SAP SecurityBridge platform is equipped with an IdentityProtection feature. Once installed, the SAP instance of your choice becomes the verifier for identities. IdentityProtection automatically detects new identities, informs the identity owner and allows reporting of identity theft.
When the rightful account owner reports potential malicious activity, the SecurityBridge intrusion detection system raises a security alert which can again be linked to automated actions.
The verifier, which is a nominated system in your SAP landscape (e.g. SAP GRC, SolMan, …) evaluates all logons and interlinked meta-data to decide whether the logon matches an existing and already trusted identity. This entire process happens in real-time and seamlessly without a noticeable impact on system performance.
Whenever an SAP account is used on a terminal (or IP) not previously used the verified account owner receives an instant information email.
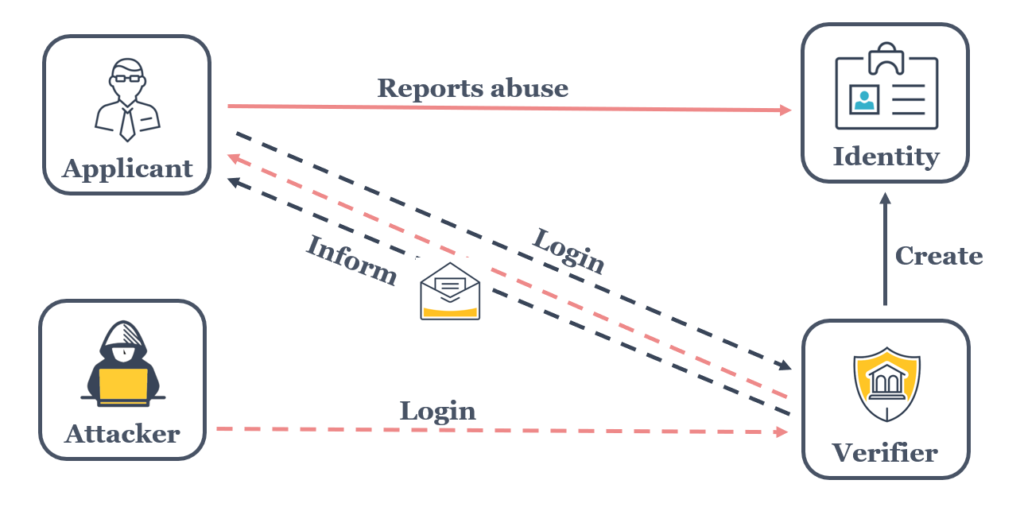
If the true owner of the identity does not recognize the login activity, a potentially malicious logon can be reported.
A practical example of an SAP identity theft
When logging on to an SAP account from a new terminal SecurityBridge identifies the new login and IdentityProtection issues an email to an earlier confirmed email address.
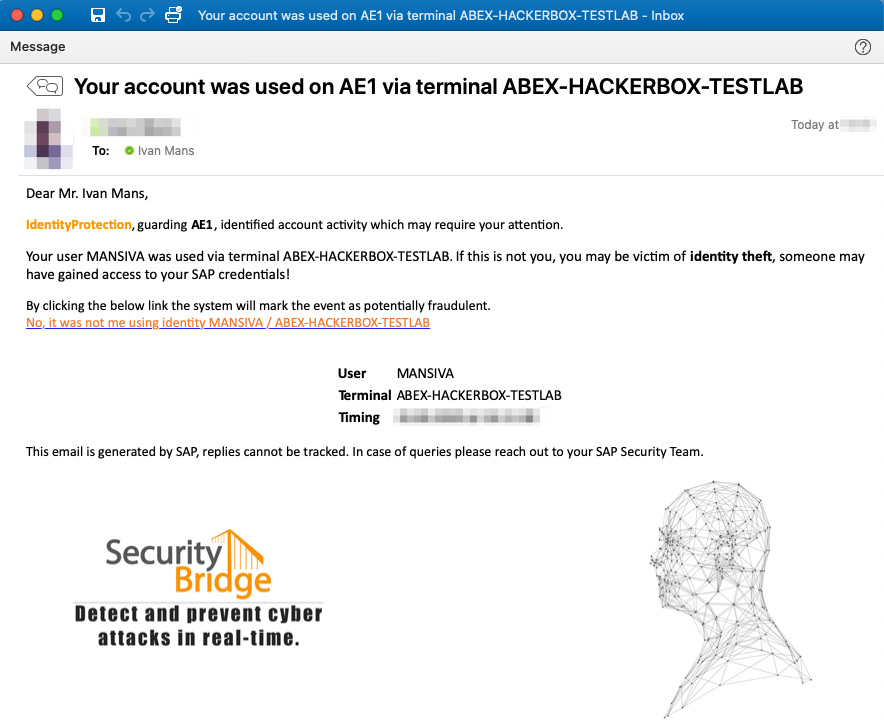
An active identity confirmation system is a great addition to any SAP system, as it pro-actively involves the user community in securing their SAP credentials. Also, two-factor authentication mechanisms are possible and recommended. Unfortunately, such solutions are typically tricky to implement.
Learn more about SecurityBridge!

Download the Product Comparison Report and understand that holistic security for SAP can be delivered by a single solution.


5 Steps for Kick-starting Holistic SAP Security in 1 Day

SAP Vulnerability Management vs SAP Patch Management

Sales & Partner Manager – APAC Market (Singapore)

Pre-Sales Consultant – APAC Singapore





