- February 28, 2022
What DevSecOps can look like for SAP

For the past years organizations see a constant increase of cyber-attacks. Those attacks are getting more sophisticated and target the crown jewelry of an enterprise. Threat actors are not retaining from attacking the enterprise critical applications, especially because those are particularly lucrative to sell or trade.
Organizations running SAP software struggle with the situation since SAP systems are complex and hard to patch – and even worse, SAP systems are hardly understood by the information security department team members. While it does not surprise that traditional security reveals some shortcomings, DevSecOps for SAP could introduce a new approach with a more promising efficiency.
What is DevSecOps?
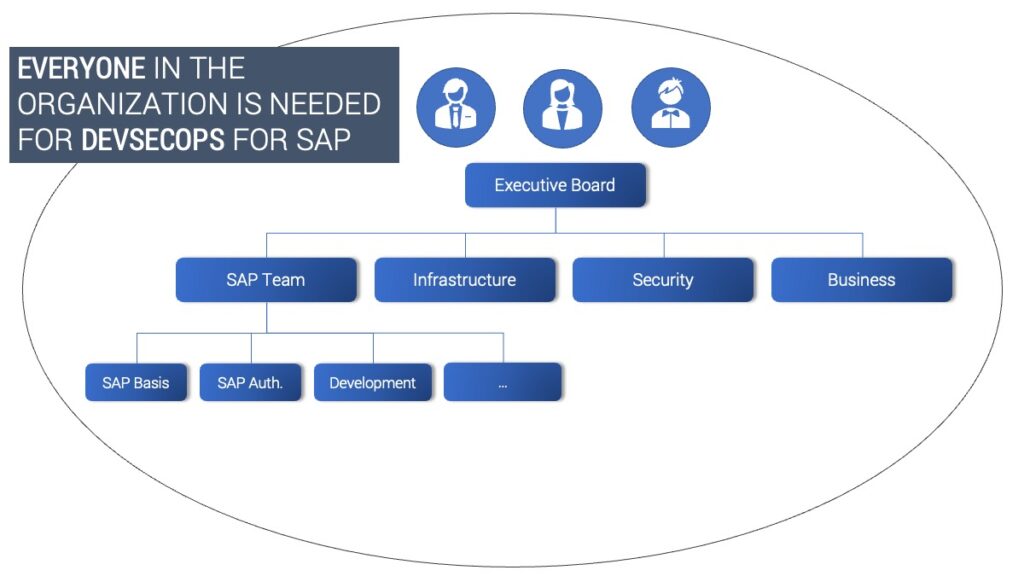
DevSecOps introduces a new mindset that makes everyone in the organization responsible for security. While traditional security often introduces a roadblock for the business targets this leads to by-passing important security measures. Ignorance is not an option, but it is simple and remains effortless.
DevSecOps includes all departments of an organization and embeds “security thinking” into the entire change process, from the executive board down to the individual teams. This approach requires high level management support from the board of directors down to the individual department leads with a common understanding throughout all team leaders and the individual experts. Business operators need tools and processes that support…
- Continuous Monitoring
- Scanning for Security Defects
- Attack detection
- Change Management and Governance
- Regular assessments
Why is DevSecOps for SAP changing the game?
In the past security was often neglected while implementing projects or new feature releases, under the assumption security defects can be resolved later in an existing system by the information security team. This introduces additional complexity to identify and remove the contained security flaws. It furthermore demands a commitment of budget and skilled resources, which not many organizations are willing to provide especially because updates and changes may cause business disruption.
If security considerations are introduced in an early phase of a project, security defects can be identified a lot earlier in the game. This alone makes it a far more efficient and easier to resolve a potential exploitable vulnerability. With good tools in place this becomes very efficient and allows organizations to even identify and resolve vulnerabilities that have been introduced in earlier iterations of their change processes.
The biggest benefit however resides from the fact that any process or feature has been implemented with security by design, leading to a resilient environment for cyber-attacks.
DevSecOps for SAP
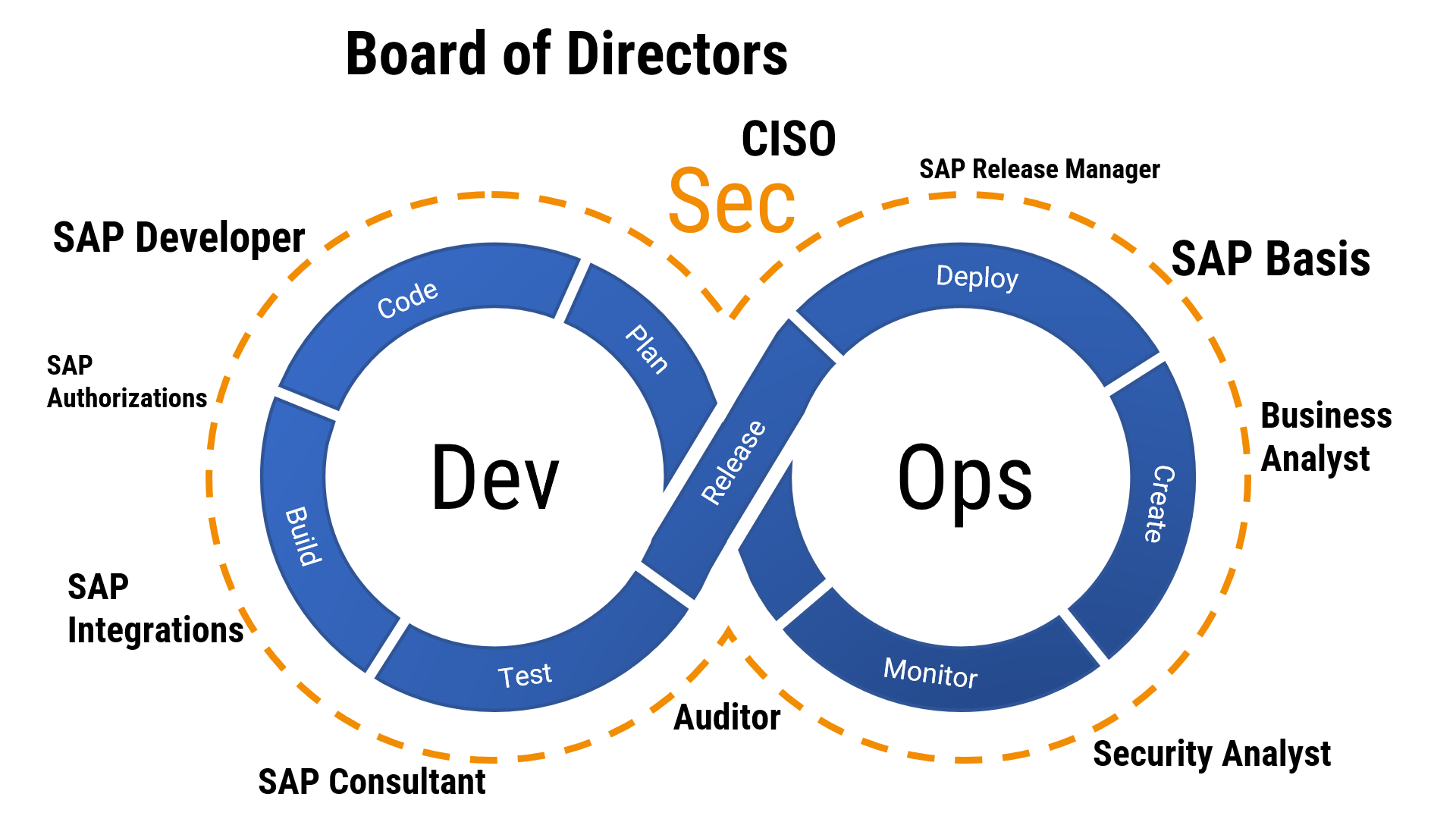
A new business projects is started with the intent to change SAP applications or processes to introduce new functionality. Like for any project time, budget, and available resources are key elements. For DevSecOps to work this cannot lead to neglecting important security considerations to be made at an early phase off the project. In reality, every single project is a security project. This means that business requirements and targets must not eliminate security concerns. Processes and tools are needed to enable the teams to work together to answer important questions. Will the project introduce a security impact to contained data and established processes? Similarly, is there a need for additional software and security architecture, or is a specific skillset required that needs to be onboarded to the project?
In an agile environment, once all epics and user stories have been written the design phase can start. With a security mindset embedded into the project, this will automatically lead to a solution that is secure-by-design.
The challenge: SAP standard does not provide the tools needed to validate source code for security flaws. For this reason, the SecurityBridge code vulnerability analyzer complements SAP standard by integrating within the SAP standard development IDE using SAP Code Inspector and the ABAP Test Cockpit.
As a result, new business functions are deployed without significant security defects into the test environment. Quality gates enabled in the SAP transport management system, can be very helpful to avoid that source code is moved, without proper security validation.
Functional issued discovered in the user acceptance test (UAT) phase trigger a restart of the validation cycle. Only once all security and functional requirements are met, the production deployment can be initiated. The SAP transport management system is vulnerable for Software Supply Chain attacks unless the following (lnk) Security Patch has been installed. The go-live does not end the DevSecOps process, it only defines the handover to the so called “Keep-System-Running” (KSR) teams.
In this phase of the lifecycle the DevSecOps for SAP focusses on monitoring to enable attack detection, regular (or better continuous) vulnerability assessments and accurate security patching.
Which tools are needed to introduce DevSecOps for SAP?
While many organizations already make use of Change Management and IT Service Management solutions, they do not yet have all tools needed to embark on a DevSecOps journey with SAP.
The SecurityBridge Platform provides all that is needed. It comes with an open API that allows integrating within already established sap secuolutions and provides the missing link between Change Management and Security Incident. With a one-stop-shop SAP cybersecurity solution it also reduces the TCO compared to individual siloed tools for Code Scanning and Vulnerability Management.
Reach out if you want to learn more about SecurityBridge Platform for SAP.
Posted by
Looking into securing your SAP landscape? This white-paper tells you the “Top Mistakes to Avoid in SAP Security“. Download it now.
Join our 4th #CrossTheBridge Cycling Event!