SAP BTP Security: A Top Priority for 2024

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
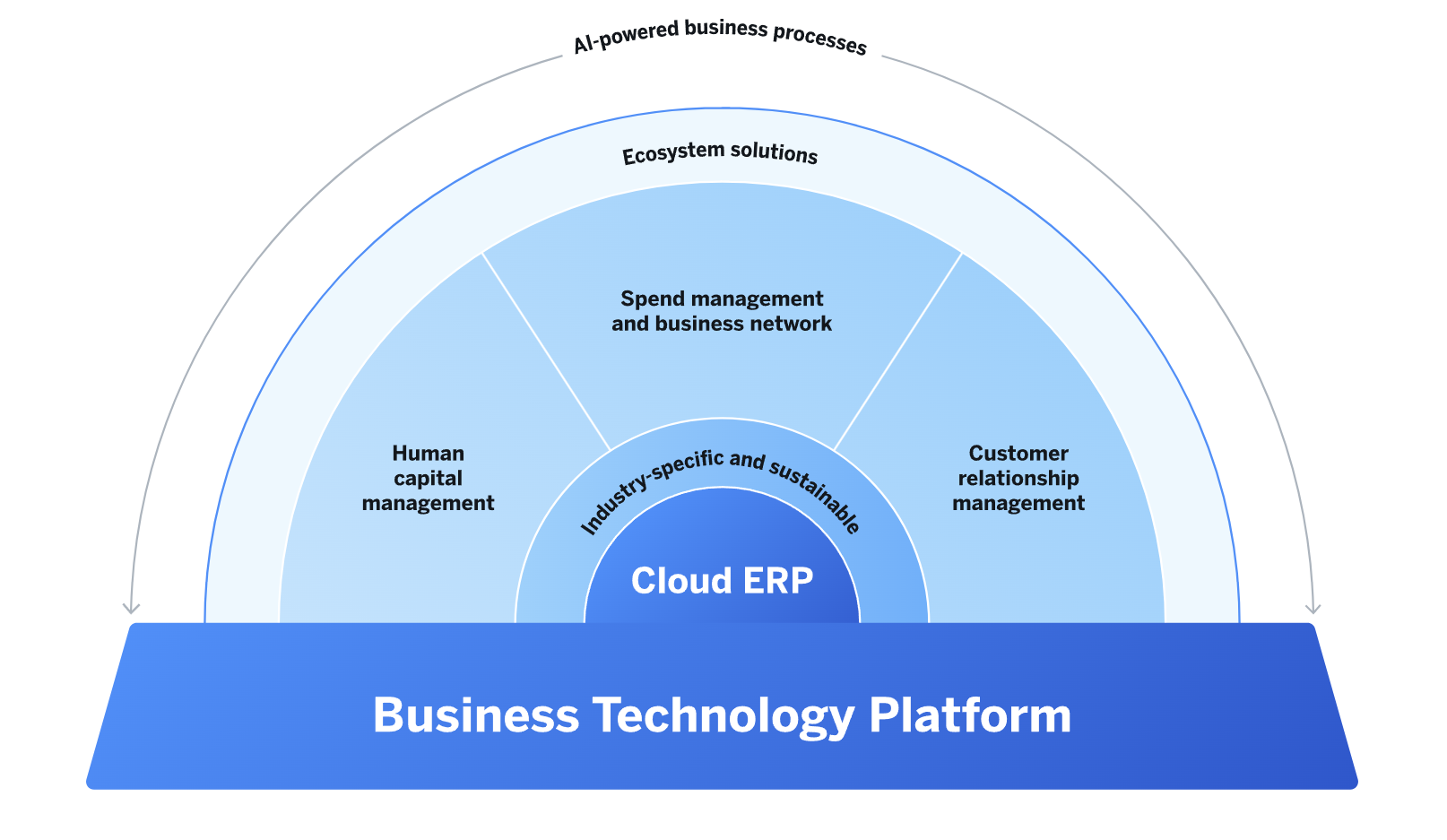
What is SAP Business Technology Platform (BTP) Security?
SAP Business Technology Platform (SAP BTP) is a cloud-based platform offered by SAP that provides a range of services and tools for building, extending, and integrating applications in the cloud. SAP Business Technology Platform Security refers to the measures and practices implemented to protect the data, applications, and infrastructure within the SAP BTP environment. These measures encompass various cloud security practices to ensure comprehensive protection.
Why is SAP BTP Security so crucial?
Ensuring security within SAP BTP, part of the broader SAP Cloud Platform, is critical to protecting sensitive business information and maintaining the integrity of applications and services. The realm of security and compliance demands a comprehensive reevaluation. New organizational processes and responsibilities must be meticulously crafted, implemented, and monitored to prevent potential chaos.
In addition to the critical security aspects and the coverage by the SecurityBridge Platform discussed later in this article, organizations that adopt SAP BTP must also diligently address the following critical tasks. These include defining a staging concept, establishing development guidelines, and taking measures to prevent the creation of uncontrolled BTP subaccounts that might compromise the established staging concepts.
What are the key aspects of SAP BTP Security?
While SAP BTP is a new field, we can already highlight some aspects of your security considerations that are vital for every organization that plans to adopt the SAP Business Technology Platform for productive use cases.
Identity and Access Management (IAM): SAP BTP provides IAM capabilities that allow organizations to manage user identities and control access to resources. It includes features such as single sign-on (SSO), multi-factor authentication (MFA), and role-based access control (RBAC) to ensure that only authorized users can access the platform’s services.
Data Encryption: Data at rest and in transit is typically encrypted to protect it from unauthorized access. SAP BTP uses encryption protocols to secure data both within the platform and while data is transferred between the platform and external systems.
Security Monitoring: Continuous monitoring of the SAP BTP environment is crucial to detect and respond to security threats. Security monitoring tools and practices identify suspicious activities and potential vulnerabilities. Audit logs are essential for this purpose, and they can be managed and retrieved using the Audit Log Retrieval API and the Audit Log Viewer.
Compliance and Governance: Organizations often must adhere to specific compliance requirements when using SAP BTP (such as GDPR, HIPAA, or industry-specific regulations). Compliance and governance features help ensure that the platform meets these requirements.
Application Security: Developers and administrators should follow best practices for securing the applications and services deployed on SAP BTP. This includes vulnerability assessments, code reviews, and regular updates to address security vulnerabilities. The Cloud Foundry and Cloud Foundry environment integrate various security components like audit logging, credential management, and malware scanning to enhance security and operational efficiency.
Network Security: Proper network segmentation, firewalls, and security measures are essential to protect against unauthorized access and network-based attacks.
Incident Response: In the event of a security breach or incident, a well-defined incident response plan should be in place to contain the threat, investigate the incident, and take appropriate action to mitigate the impact.
Security Training and Awareness: It is vital to ensure that all personnel interacting with SAP BTP are aware of security best practices and potential threats. Training programs and awareness campaigns can help reduce the risk of human error.
Third-Party Integrations: When integrating third-party applications or services with SAP BTP, it’s fundamental to assess and ensure the security of these integrations to prevent vulnerabilities from being introduced.
Cloud Connector: The cloud connector plays a crucial role in ensuring proper firewall configuration and facilitating secure data exchange in cloud environments.
To support the above security aspects, SAP provides the following security features to protect the BTP applications – encryption, default identity provider for enabling Single sign-on and authentication, audit logging, credential store, malware scanning, etc.
Identity and Access Management
Identity and Access Management (IAM) is a cornerstone of security in the SAP Business Technology Platform (SAP BTP). It ensures that only authorized users can access SAP BTP resources and applications, safeguarding sensitive business information. SAP BTP offers various identity providers, including the default identity provider, SAP Cloud Identity Services, and custom identity providers. These identity providers manage user identities and authentication processes for SAP BTP applications.
One of SAP BTP’s standout features is its support for single sign-on (SSO). With SSO, users can access multiple SAP BTP applications using a single set of credentials, streamlining the user experience and enhancing security. Additionally, SAP BTP’s access management capabilities, which include robust authentication and authorization mechanisms, ensure that users have access only to the resources and applications they need, minimizing the risk of unauthorized access.
Authentication and Authorization
Authentication and authorization are pivotal components of SAP BTP security. Authentication is the process of verifying users’ identities, while authorization determines the actions users are permitted to perform on SAP BTP resources and applications.
SAP BTP supports several authentication methods, including basic authentication, OAuth, and SAML. While basic authentication is straightforward, it is not recommended for production environments due to its inherent security vulnerabilities. OAuth and SAML, on the other hand, offer more secure authentication options, providing enhanced protection for SAP BTP resources and applications.
Authorization within SAP BTP is role-based. Users are assigned specific roles that define their permissions and the actions they can perform on SAP BTP resources and applications. This role-based access control ensures that users have the appropriate level of access, reducing the risk of unauthorized actions and potential security breaches.
Security Considerations and Recommendations
To ensure the security of SAP BTP resources and applications, SAP provides a range of security features and best practice recommendations. Key considerations include:
Secure Communication Protocols: Utilize HTTPS and TLS to protect data in transit, ensuring that sensitive information is encrypted and secure.
Access Controls: Implement robust authentication and authorization mechanisms to ensure only authorized users can access SAP BTP resources and applications.
Regular Updates and Patching: Keep SAP BTP components up to date with the latest patches and updates to address known security vulnerabilities.
Security Monitoring: Continuously monitor SAP BTP resources and applications for security incidents and vulnerabilities, enabling prompt detection and response.
Backup and Recovery Strategy: Develop and implement a comprehensive backup and recovery strategy to ensure business continuity during a security incident.
How does SecurityBridge cover SAP BTP Security Monitoring?
It’s possible to connect the SecurityBridge Platform with SAP BTP to enhance the security of your cloud-based SAP solutions. Here’s how the SecurityBridge Platform can work in conjunction with SAP BTP:
Vulnerability Scanning in SAP BTP:
If you have SAP applications or services running on SAP BTP, you can use SecurityBridge to conduct vulnerability scanning and assessments on these cloud-based SAP instances.
This allows you to identify and address security weaknesses such as too many admin users, excessive rights granted to external users, invalid users, and configuration issues.
Continuous Monitoring:
SecurityBridge continuously monitors on-premises and cloud-based SAP systems, including SAP BTP applications.
This ensures you have visibility into security events such as admin rights assignment to users in real time.
Integration with SAP BTP Services:
The SecurityBridge platform can be integrated with SAP BTP subaccounts and global accounts.
Integration involves leveraging APIs, command line interfaces, and connectors to collect security data from cloud-based SAP instances and feed it into the SecurityBridge platform for analysis.
Real-time Alerts and Notifications:
SecurityBridge Threat Detection can generate real-time alerts and notifications for security incidents and vulnerabilities detected in SAP BTP environments.
These alerts are to be sent to security teams for immediate response.
Incident Response in SAP BTP
In the event of a security incident or vulnerability discovery, SecurityBridge can guide incident response and remediation steps specific to SAP BTP environments.
Compliance and Reporting
The SecurityBridge platform can help ensure that your cloud-based SAP solutions on SAP BTP comply with security and regulatory requirements.
It can generate compliance reports and evidence to demonstrate adherence to security standards.
Threat Intelligence Integration:
The SecurityBridge platform can integrate with threat intelligence sources to provide up-to-date information on threats and vulnerabilities that may impact SAP BTP deployments.
In conclusion, the SecurityBridge platform helps organizations proactively identify and respond to security threats and vulnerabilities in their SAP landscapes, ensuring the integrity and availability of critical SAP systems and data. It is a comprehensive solution for SAP security that combines scanning, monitoring, and incident response into a single platform.
Conclusion
SAP Business Technology Platform (SAP BTP) offers a robust security framework for managing identity lifecycle and access control. With support for various identity providers, including the default identity provider, SAP Cloud Identity Services, and custom identity providers, SAP BTP ensures secure and efficient identity management. The platform’s access management features, encompassing authentication and authorization, further enhance security by ensuring users access resources and applications appropriately.
By following best practices and security recommendations, SAP BTP customers can protect their sensitive business information and maintain the integrity of their SAP BTP resources and applications. This includes using secure communication protocols, implementing stringent access controls, regularly updating and patching components, monitoring security incidents, and having a robust backup and recovery strategy.
Prioritizing security within SAP BTP is essential for safeguarding business operations and ensuring the continued success of your organization in the digital age.