Critical SAP Zero-Day Vulnerability: CVE-2025-31324

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
Updated May 14th, 9am CET
All SecurityBridge customers can already use the solution to scout for the vulnerable Visual Composer component.
SecurityBridge offers EMERGENCY INSTALLATION for SAP customers who need to check if they are exposed. Please contact us and let us know it’s regarding CVE-2025-31324
On April 24, 2025, SAP released a Hotnews (and on SAP Patch Tuesday of May another one) about a severe vulnerability within SAP Java systems, which has also been recorded in the NIST database known as CVE-2025-31324 and linked to China-based Nation State actors. This risk is related to a known component that allows unrestricted uploads and can lead to a full compromise of your SAP systems.
To illustrate the seriousness of this vulnerability, CISA has added it to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
We strongly advise customers to review their landscape and proceed where needed to mitigate the risk by either implementing the workaround or applying the correction. Note that the workaround is not a permanent solution. It is only supposed to be used as a quick fix.
What’s the Risk?
Depending on how the system was installed, the affected component may or may not be present. For example, if the Java system were only installed as a plain Java stack or the default installation that was part of Solution Manager, then the component would not be there.
To line out what the above means for customers, the following points give some idea about the risk of your system(s) for CVE-2025-31324. Do note that the risk level varies (for example based on if your SAP Java system is exposed to the internet).
You are vulnerable if:
- Your SAP landscape includes Java systems
- You installed the Visual Composer add-on (Software Component: VCFRAMEWORK)
- You have the component installed/active but do not use it.
- The VISUAL COMPOSER FRAMEWORK component version is lower than the versions listed here: 3594142 and 3604119.
- You use an outdated version of this add-on that is lower than 7.5.
- The risk adds up if your version is 7.0 and SP is lower than 16, because this was already reported in 2021 as high risk, which has a CVSS score of 9.9. See: 3084487, CVE-2021-38163.
The above points and the initial analysis suggest that only a small subset of customers meet all these criteria in general, as the component is solely used for developing applications and transaction model changes.
No public data has been shared regarding the frequency, origin, or methods of exploitation, which makes it difficult to assess the threat’s scale. However, since VCFRAMEWORK may have been separately deployed after installing your SAP Java system, reviewing your system(s) is strongly advised.
If your environment includes this component, it is advised to review whether it is in use. A full system compromise is possible because the component allows potentially dangerous file types to be uploaded. Depending on what kind of executable is uploaded, the targeted system’s confidentiality, integrity, and availability may be affected.
Resolution Steps
Refer to SAP Note 3594142 and 3604119 for technical details.
If you use VCFRAMEWORK:
- Review 3084487
- Upgrade to the latest version applicable for your system
If you use VCFRAMEWORK but the version is lower than 7.5, e.g., 7.0:
- Immediate action is advised by reviewing all the notes applicable to your version
- Upgrade to the latest version applicable for your system
If You Don’t Use It:
- The application can be disabled with various options as a workaround:
- SAP Note 3593336 – Unfamiliar files found in SAP NetWeaver Java file system
- Or uninstall it:
- Either via SAP SUM or telnet, see
- SAP Note 3416257 – How to undeploy VC70RUNTIME.SCA via Telnet
- This note is about version VC 70, but the same procedure can be used.
Note that even if you decide to uninstall it, instead of just applying the temporary workaround. It is advised to still apply the workaround after uninstalling if the system gets the component installed back in the future, intentionally or not.
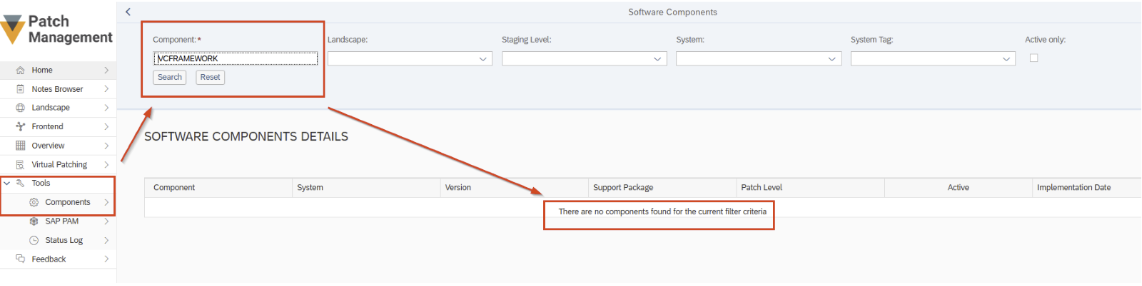
SecurityBridge customers can also search for relevant Software Components with our Patch Management Tool feature and locate the Software Component ‘VCFRAMEWORK’:
For more information on this topic, see these resources:
- SAP Security note: 3594142
- SAP Security note: 3604119
- SAP FAQ for 3596125
- SAP Workaround for Visual Composer: 3593336
- CVE-2025-31324
- SecurityBridge Knowledge Base article (customers only)