SIEM Integration for SAP
-
Complete visibility for the Security Operations Center (SOC): Send all or a subset of security-relevant events to your SIEM to gain complete real-time visibility into what is happening in the vast SAP system landscape.
How it works
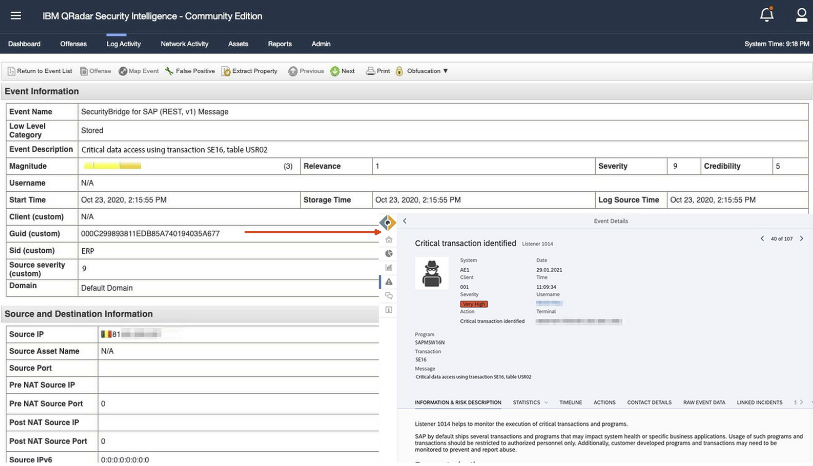
Critical SAP Security Events missing in the SOC
SIEMs are central to threat detection. They collect data from various log sources, operating systems, information from malware defense, and suspicious port scans and should contain event data from business-critical applications like SAP.
However, SAP log sources are often turned off because they generate too much data, and the results are difficult to understand and correlate for the security operations center. Unfortunately, this means that critical SAP security events are missing in the security overview.
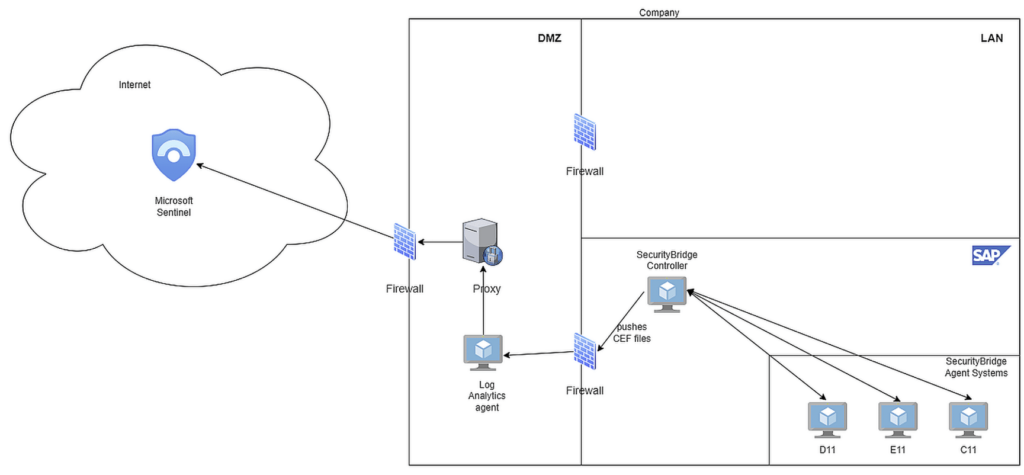
Bridge the Gap
SecurityBridge solves this problem by scanning all SAP security logs based on hundreds of use cases, capturing security-relevant information and malicious actions. SecurityBridge leverages built-in SAP security expertise to send only relevant events to the SIEM.
Security teams are provided with instantly actionable intelligence that is easy to understand even if they have limited SAP security knowledge.
SecurityBridge doesn’t just take events from various SAP data sources but also uses the data source as a trigger. Once triggered, the platform scans for the security context (context correlation is key to avoid false positives) to assign a reliable event severity and a speaking alert text.
Supported SIEMs and SOARs
SAP landscapes are crucial yet often a blind spot within the cybersecurity organization. SecurityBridge offers a ready-to-use SIEM integration that bridges IT and SAP security, enabling SOC teams to understand and manage SAP incidents easily. With built-in, customizable monitoring rules and enriched incidents that are actionable and understandable for non-SAP employees, it integrates seamlessly with other SIEM events for complete threat context. Additionally, SecurityBridge APIs support workflow integration for sharing Indicators of Compromise and automating security controls.






SecurityBridge can integrate with any SIEM provider. If your SIEM provider is not listed here, please contact us.
Integrations to power deep automation and complete visibility
Integrate SecurityBridge with your tech stack to monitor SAP data wherever suits you best
and automate workflows to limit manual workload.









Solve it with SecurityBridge
Endpoint Monitoring
Endpoint Forensics
Enable your security teams to use the comprehensive forensic toolkit of SecurityBridge.
Smart Data Transfer
Translation
Real-Time
Incident & Response
Empower security teams to collaborate and to become efficient in responding to SAP-specific incidents.
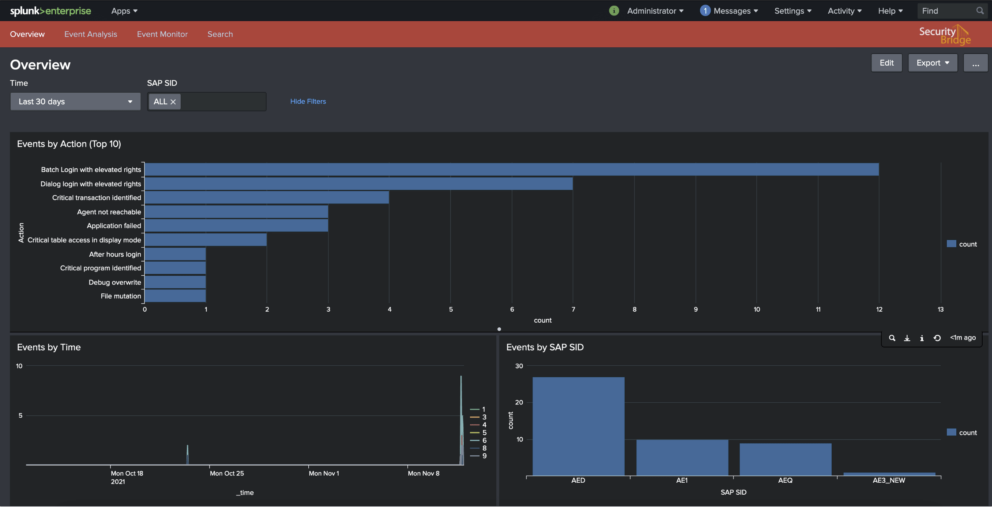
Certified for Splunk
Real-time intrusion detection scanning for SAP is visible directly in Splunk. SecurityBridge eliminates the gap between SAP security monitoring and Splunk.
Splunk is used to search, monitor, visualize, and analyze machine data generated from various machines in real-time. It is generally used to identify data patterns and metrics, detect and diagnose security problems, and provide the intelligence required for business operations. Splunk is also used for log management and analysis.
With the help of SecurityBridge, SAP logs are easily and intelligently transferred to Splunk. Instead of transferring the SAP logs 1:1, only security-relevant events with decision-enabling messages are transferred to Splunk’s SIEM.
Find us on Splunkbase
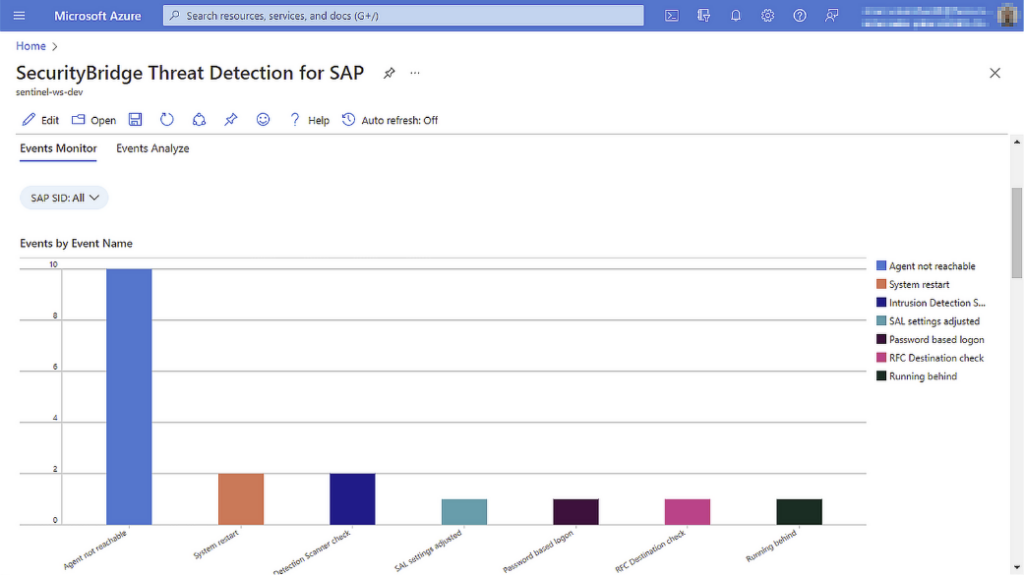
Integration with Microsoft Sentinel
SecurityBridge integrates directly with Microsoft Sentinel, allowing threat detection events from your on-premise and cloud-based SAP systems to be sent directly into your organization’s security monitoring.
Use the Microsoft Sentinel integration to receive normalized and speaking security events, pre-built dashboards, and out-of-the-box templates for your SAP security monitoring.
Find us on the Azure Marketplace
Trusted by hundreds of SAP Teams






The latest resources