Additional layer for SAP Data Security

Chapters
Share Article
For many years, it’s been said that data is the new oil. This means that data rich companies could well be more successful than their competitors. Data and information are like fuel for companies since both are needed for ongoing business transactions and innovation. Companies can only win the race against their competitors if they are not losing this fuel, meaning they must keep data secure at all times and anywhere.
Protecting the company’s IT perimeter against cyber-attacks by leveraging firewalls and intrusion detection systems, as well as promptly implementing security patches are today’s best practices for IT security. The SecurityBridge Platform provides SAP customers with a holistic solution to detect vulnerabilities, identify missing security patches, and create alerts when a nefarious but anonymous user is posing a threat. Even the examination of our customers’ own developments is covered. All of which leads to an increase in the SAP data security posture.
Adding another ingredient to SAP Data Security
All IT security experts know, however, that there’s still a risk that a cyber-attack could successfully enter the IT perimeter. Some of them might remain hidden for quite a while, like successful Log4J intrusions, until they’re used as “backdoor” for data leakage. So, wouldn’t it be great to have an additional and independent layer for SAP data security which prevents the unauthorized use and distribution of the captured data?
The key success factor for this is, to always work with encrypted data. While encryption for data at rest and data in transit are already widely used techniques, encryption of data in use is leveraging solutions that have reached maturity in the last couple of years. That’s why companies must adopt a Digital Rights Management platform and integrate it with all their egress points used in their enterprise applications and platforms.
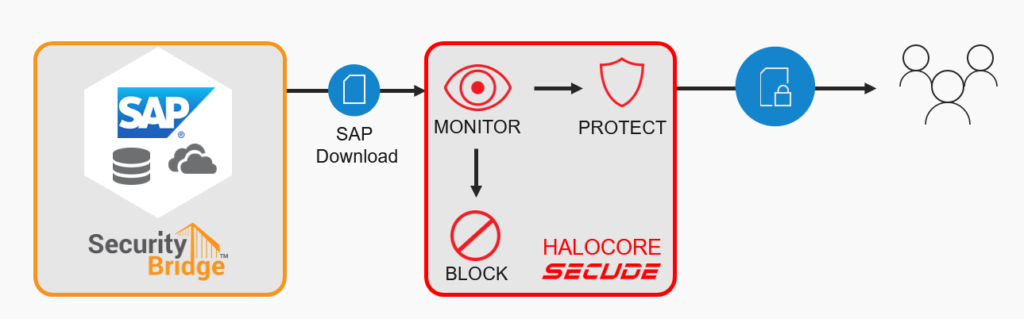
SAP is the most important enterprise business application, and provides several data export functions, so SAP users can download data e.g., directly into an Excel spreadsheet. However, while the data is protected in SAP, that protection is lost when on downloading. While the monitoring of the SecurityBridge platform is equipped with special sensors that inform about data exfiltration and even reports anomalies e.g., extraordinarily large data extraction, SAP data can leave the secure system area through uncontrolled application features, like data downloads and similar egress points.
How to protect SAP data, outside of SAP?
We asked our customers how they can continue to protect their SAP data once it’s left their SAP system. Is there a way to map the SAP security profile to any data downloaded from SAP and used e.g., in various Microsoft Office applications? SECUDE provides an answer specifically to this question.
Microsoft Information Protection (MIP), as the most visible Digital Rights Management platform on the market, that can help protect this exported data and files from SAP. However, the existing efficient user workflows are only preserved with a deep SAP integration and an automated approach for mapping the SAP security profile of the corresponding data to the appropriate MIP protection template.
SECUDE HALOCORE provides this automated integration of MIP into SAP environments. The solution is triggered by SAP functions that expose data beyond the system boundaries and retrieves all relevant SAP business metadata for an attribute-based classification on-the-fly. Once the data classification is determined, the corresponding MIP protection template is applied, and the file is seamlessly sent to the SAP frontend or web UI.
With this approach the SAP user experience is fully preserved and in addition the SAP data security profile is now enforced in Microsoft Office or Adobe Acrobat Reader. For special engineering and supply chain use cases, SECUDE provides dedicated MIP-clients for CAD applications which allow users to work with native MIP-protected CAD files.
This blog article was written jointly by Holger Hügel from Secude and Christoph Nagy from SecurityBridge.