Boost SAP Security: Enhancing SAP Enterprise Threat Detection with SecurityBridge

Chapters
Share Article
This article was a collaboration between:
– Arndt Lingscheid, Global Solution Owner – Cybersecurity and Data Protection at SAP SE, and
– Christoph Nagy, CEO at SecurityBridge
New Integration Unveiled at Rotterdam’s SAP Security Event
On July 19, 2024, our co-hosted SAP Security Customer Event at the iconic Euromast featured an exciting announcement about a brand-new integration. The event was filled with engaging sessions tailored for SAP security experts and managers focused on the security posture of their critical enterprise applications. For a detailed recap, check out our Summary Article. If you’re interested in similar events, don’t miss our upcoming opportunities.
Enhancing SAP Security through SAP ETD and SecurityBridge Integration
The SAP Enterprise Threat Detection (SAP ETD) application offers essential security information and event management (SIEM) capabilities. Using real-time intelligence, SAP Enterprise Threat Detection helps enforce data governance and detect both internal and external cybersecurity threats. Utilizing SAP HANA technology, SAP Enterprise Threat Detection processes various applications, databases, and operating system logs, enabling the detection of security threats in an extensive SAP landscape. Given that SAP logs cover a broad range of business transactions, they require a more complex treatment and data model compared to other existing SIEM applications.
The cornerstone of the SAP Enterprise Threat Detection analysis is its semantic understanding of SAP application logs and the underlying data model. Having these elements is key as it allows the system to conduct a detailed analysis by transforming raw logs into meaningful business events. Unlike traditional SIEM solutions, this function facilitates enhanced detection of complex threats at the application level while simultaneously reducing false positives. Enterprise Threat Detection can be tailored to individual business processes. By correlating events across various SAP applications, the system helps successfully identify complex attack patterns.
This article explores the rationale, benefits, and timing of integrating SAP Enterprise Threat Detection with SecurityBridge. Enhancing the cyber security practice is a vital element for all organizations to stay protected and competitive but also to comply with continuously evolving compliance and audit standards.
Why the Integration is Essential
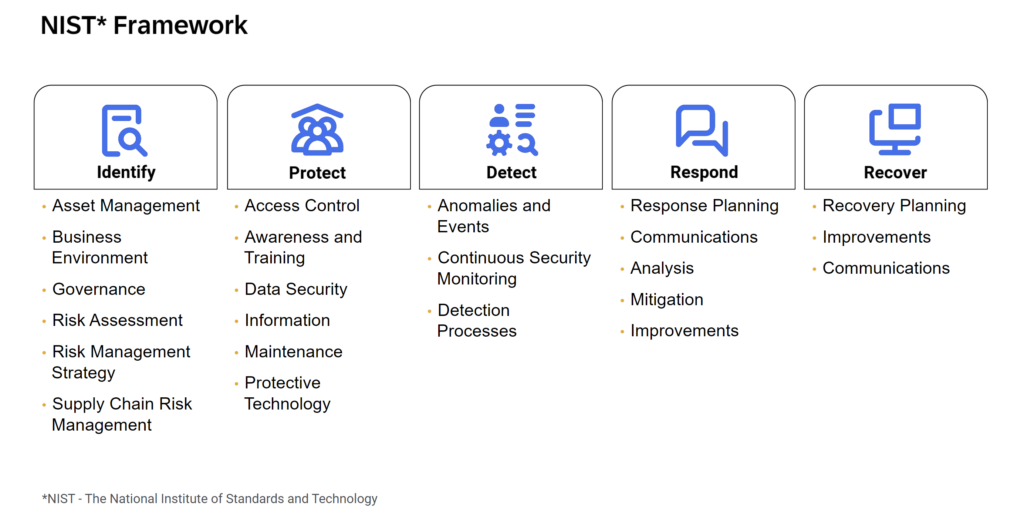
The rationale for integrating SecurityBridge with SAP Enterprise Threat Detection can be explained using the NIST Cybersecurity Framework (CSF). While SAP ETD is characterized by the reactive aspects of security – DETECT and REACT – SecurityBridge can also improve the proactive aspects – IDENTIFY and PROTECT.
SAP Enterprise Threat Detection has a proven record of identifying cyber incidents in SAP environments. Yet, SAP S/4HANA, the leading ERP solution, produces vast transactional logs fragmenting critical security information. Pinpointing specific vulnerabilities and weak system configurations remains challenging without ongoing pattern development in SAP ETD’s forensic lab. Based on the insight shared from SecurityBridge Security & Compliance it will be possible to zoom in on relevant areas that need customer attention. Imagine directing a surveillance camera precisely to vulnerable areas of your enterprise application.
Thus, the benefits are:
- Enhances threat detection by focusing on specific vulnerabilities within SAP environments.
- Facilitates efficient cybersecurity by unifying fragmented security information from voluminous transactional logs.
- Optimizes system configuration through ongoing development and improved focus on critical areas using SecurityBridge Security & Compliance insights.
What the Integration Offers
A stunning $6 trillion annually is drained from the global economy through cybercrime. While this is an immense burden for impacted organizations, only 38% of them can detect cyber incidents before it is too late to act on them. SecurityBridge and SAP Enterprise Threat Detection can change this alarming situation.
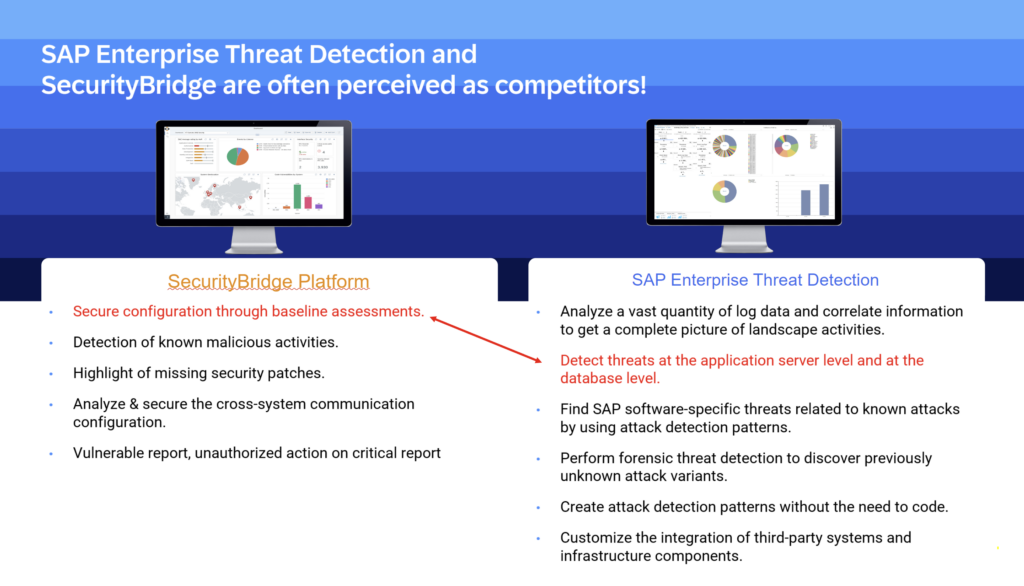
SAP Enterprise Threat Detection includes an open API that facilitates data sharing with solutions like SecurityBridge. SecurityBridge’s continuous security approach evaluates security configurations and applies necessary patches to mitigate vulnerabilities. By baselining the SAP security posture, SecurityBridge can feed all detected vulnerabilities directly into SAP Enterprise Threat Detection, enhancing the monitoring process.
Pre-defined detection patterns in SAP Enterprise Threat Detection will now surveil the vulnerable areas and raise an alert in real time to the client’s attention.
When the Integration Makes Sense
Let’s explore the situations when and reasons why this powerful integration is beneficial, so you can identify the best occasions to implement it for optimal outcomes.
1. Critical Infrastructure Customers
– Integrated Risk Management: Leverage both platforms to implement comprehensive risk and vulnerability management, enhancing threat detection and response.
– Regulatory Compliance: Ensure adherence to regulations with a security strategy that includes proactive risk management and real-time threat detection.
2. SAP Environments Processing “SECRET” Data
– Protection of Sensitive Data: Secure high-value data assets from breaches, minimizing risks to reputation, competitive edge, and operations.
– Enhanced Data Security: Maintain confidentiality, integrity, and availability of critical data, ensuring top-tier protection for sensitive information.
3. SAP Enterprise Threat Detection Customers Seeking Enhanced Security
– Improved Threat Visibility: Use SecurityBridge’s detection capabilities for deeper threat insights, complementing SAP Enterprise Threat Detection’s strengths.
– Proactive Security Measures: Implement robust preventative actions with real-time monitoring and alerts from SecurityBridge.
4. Customers of SecurityBridge also benefit from Robust Forensic and Threat-hunting Features that offer Comprehensive User Behavior Analysis along with a Complete Audit Trail
– Detailed Forensic Analysis: Utilize SAP Enterprise Threat Detection’s forensic tools for comprehensive incident investigation.
– Comprehensive Incident Response: Achieve a holistic view of security events by combining both platforms, enhancing incident resolution speed and effectiveness.
Conclusion
Winning the fight against organized cybercrime, industrial espionage, and insider threats hinges on collaboration within the cybersecurity industry and across organizations. The integration of SAP ETD with SecurityBridge represents a significant step forward in SAP security, offering a combined solution that addresses both proactive and reactive security needs. Embrace this integration to fortify your enterprise’s security posture and stay ahead of emerging threats.