Critical SAP S/4HANA code injection vulnerability (CVE-2025-42957) exploited in the wild - patch immediately
Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
Reported first by SecurityBridge.
The exploit was discovered by the SecurityBridge Threat Research Labs, which has also verified that the exploit is being used in the wild. Immediate patching is imperative.
CVE-2025-42957 is a critical ABAP code injection vulnerability in SAP S/4HANA (CVSS 9.9) that allows a low-privileged user to take complete control of your SAP system. See a deep technical walkthrough.
Executive summary
Here is what you need to know:
- SAP provided a patch for CVE-2025-42957 (CVSS 9.9) on August 11th – apply it immediately
- Exploitation requires access only to a low-privileged user to fully compromise an SAP system.
- It affects all S/4 HANA releases (Private Cloud and On-Premise)
- Successful exploitation gives access to the operating system and complete access to all data in the SAP system
- This includes, but is not limited to:
- Deleting and inserting data directly in the SAP Database
- Creating SAP users with SAP_ALL
- Downloading of password hashes
- Modifications to business processes
In short: A complete system compromise with minimal effort required, where successful exploitation can easily lead to fraud, data theft, espionage, or the installation of ransomware.
To demonstrate the potential impact of this vulnerability, we have created the attached Demo based on our own research and tooling:
Confirmed exploitation
While widespread exploitation has not yet been reported, SecurityBridge has verified actual abuse of this vulnerability. That means attackers already know how to use it – leaving unpatched SAP systems exposed. Additionally, reverse engineering the patch to create an exploit is relatively easy for SAP ABAP, since the ABAP code is open to see for everyone.
Recommended mitigation steps
- Patch immediately: If not already done, apply SAP’s August 2025 security updates (Notes 3627998 and 3633838)
- Check exposure: Consider implementing SAP UCON to restrict RFC usage and review and restrict access to authorization object S_DMIS activity 02
- Monitor logs: watch for suspicious RFC calls, new admin users, or unexpected ABAP code changes
- Harden defenses: Ensure segmentation, backups, and SAP-specific monitoring are in place
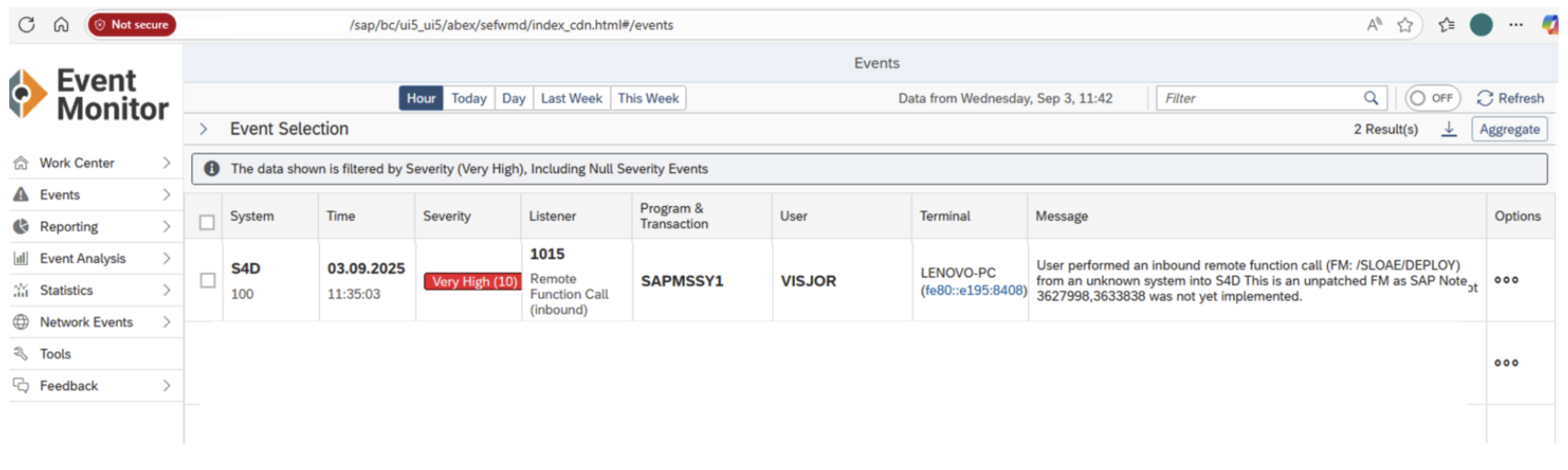
The SecurityBridge platform already detects exploitation attempts of CVE-2025-42957, giving customers visibility into potential attacks:
What makes CVE-2025-42957 especially dangerous
The attacker needs only low-level credentials on the SAP system (any valid user account with permissions to call the vulnerable RFC module and the specific S_DMIS authorization with activity 02), and no user interaction is required.
The attack complexity is low and can be performed over the network, which is why the CVSS score is so high (9.9). In summary, a malicious insider or a threat actor who has gained basic user access (through phishing, for example) could leverage this flaw to escalate into full control of the SAP environment.
Business impact: potential full system compromise
The consequences of an exploit are severe – essentially a full system compromise of the SAP application and potentially the underlying operating system. Successful exploitation gives the attacker the ability to act with administrative privileges in the SAP system. In practice, this means an attacker could do anything a legitimate SAP administrator could do, and more.
For example, SecurityBridge’s team demonstrated in a lab environment how an attacker could create a new SAP superuser account (with SAP_ALL privileges) and directly manipulate critical business data.
To illustrate the risk concretely, here are some of the malicious actions an attacker could perform:
Direct data theft or tampering: Read, modify, or delete data in the SAP database by injecting code that bypasses all application-level controls. This undermines the confidentiality and integrity of critical business information (e.g. financial records, customer data) and could facilitate fraud or sabotage (for instance, altering transaction values or wiping audit logs).
Privilege escalation and backdoor accounts: Elevate their access by granting themselves additional authorizations or creating new hidden admin users in the system. For example, an attacker could quietly add a user with SAP_ALL privileges, establishing a persistent backdoor account to use at any time.
Credential theft: Extract sensitive security information, such as password hash values for SAP user accounts.
Operational disruption: With complete control of the application and access to the host OS, attackers could deploy malware or ransomware on the SAP servers. They might encrypt vital business data or disrupt SAP services, leading to costly downtime.
Discovery, disclosure, and verification by SecurityBridge Threat Research Labs
This vulnerability was discovered and responsibly disclosed by SecurityBridge Research Labs as part of our ongoing mission to keep SAP customers secure by staying ahead of emerging threats.
SecurityBridge researchers identified the code injection vulnerability during our regular SAP security research activities and immediately initiated a responsible disclosure to SAP on June 27, 2025. SAP acknowledged the report and worked closely with us to analyze and fix the issue. The patch was provided in the August 2025 Patch Day release (roughly six weeks after reporting), reflecting a swift response by SAP’s security team.
The SecurityBridge Threat Research Labs initiative, led by our Director of Research, Joris van de Vis, exists to uncover critical vulnerabilities like this before malicious actors do so proactively. Our team is driven by the mission to “outrun” attackers and ensure the SAP community is secured through timely discovery and automated patching of SAP vulnerabilities.
Containing and patching CVE-2025-42957 with SecurityBridge
SecurityBridge includes detection patterns for CVE-2025-42957 within our SAP security platform. This means SecurityBridge customers are alerted to any exploitation attempt targeting this vulnerability in their SAP environment to enable automated incident response. For example, anomalous RFC calls or the creation of unexpected ABAP programs via this exploit are flagged by our threat monitoring. Additionally, SecurityBridge customers were already alerted before a patch was released by SAP through our virtual patching and zero-day protection.
This detection capability provides a “safety net” – especially useful for the window between a vulnerability’s disclosure and the full deployment of patches enterprise-wide.
However, we must emphasize that detection is no substitute for remediation. The primary recommendation is still to apply SAP’s patch immediately; monitoring is a complementary measure in case an attacker attempts to exploit before your patch is applied.

