No Doubt You Need SAP Security, But Are You Ready Yet?

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
SAP systems power some of the world’s largest enterprises, managing critical business operations from finance to supply chain management. Yet, SAP security has long lagged behind other areas of cybersecurity, such as network and endpoint security. The risks of SAP outages, data breaches, unauthorized access, and compliance failures have grown significantly in the past few years, making it clear: robust SAP security is no longer optional—it’s a necessity.
Despite this, many organizations are still playing catch-up. The gap between traditional cybersecurity measures and SAP security is only now starting to close, thanks to platforms like SecurityBridge, which bring enterprise-grade threat detection, compliance automation, and security monitoring to SAP landscapes.
But the question remains: Is your organization truly prepared for the evolving cybersecurity landscape?
The Hidden Security Risks in SAP Systems
Note: This section explains the complexity of ERP and that management needs to be aware of their responsibility but also that SAP systems are not secure by default.
SAP environments hold the most sensitive business data, from financial records to intellectual property, making them an attractive target for cybercriminals. Yet, many CIOs, CISOs, and CFOs continue to believe that SAP’s built-in security controls are active by default and would be enough to protect these critical ERP systems.
That’s far from reality.
Unlike traditional IT infrastructures that receive constant cybersecurity investments, SAP security is often an afterthought—leaving gaps exploitable for attackers.
Here’s why:
- SAP systems are highly customizable, making manual security adjustments necessary for every unique deployment.
- SAP security requires specialized expertise, which many organizations lack internally.
- Many SAP environments still rely on outdated security models, increasing their exposure to threats.
Economic Pressures Are Changing the Way We Approach SAP Security
Note: This section emphasizes that in integrated platform should be preferred over the silo security approach due to lack of integration, holistic 360° view, and most important due to commercial disadvantages. Mapping to the ration of Cybersecurity “Good is good enough”, a best of breed approach is not leading to 100% security either.
With global economic uncertainty and budget constraints, CFOs are demanding more ROI from cybersecurity investments. This has put pressure on security leaders to prioritize solutions that deliver measurable impact while optimizing costs.
CFOs can’t accept the financial risk of a breach either. The average cost of an SAP security breach in large enterprises exceeds \$4 million. This includes:
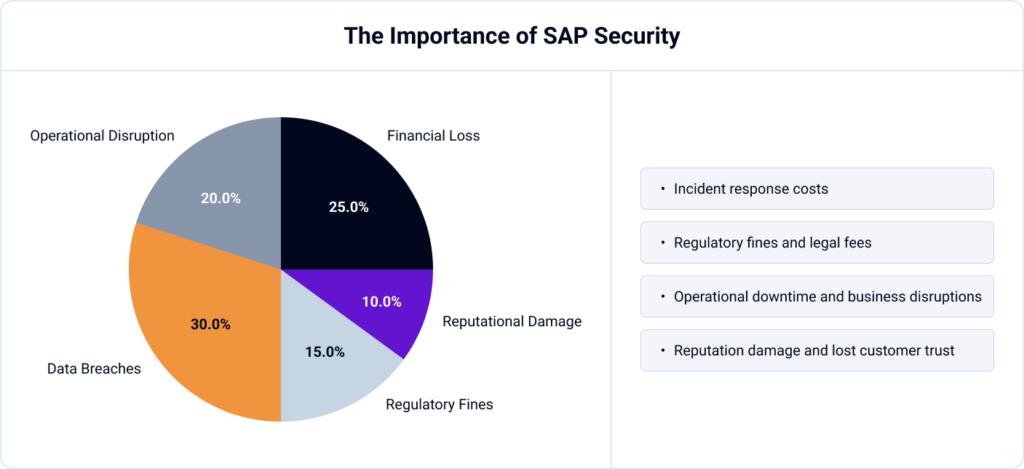
The reality? No enterprise can afford to ignore SAP security anymore. The question is how to secure SAP effectively without overspending or wasting resources.
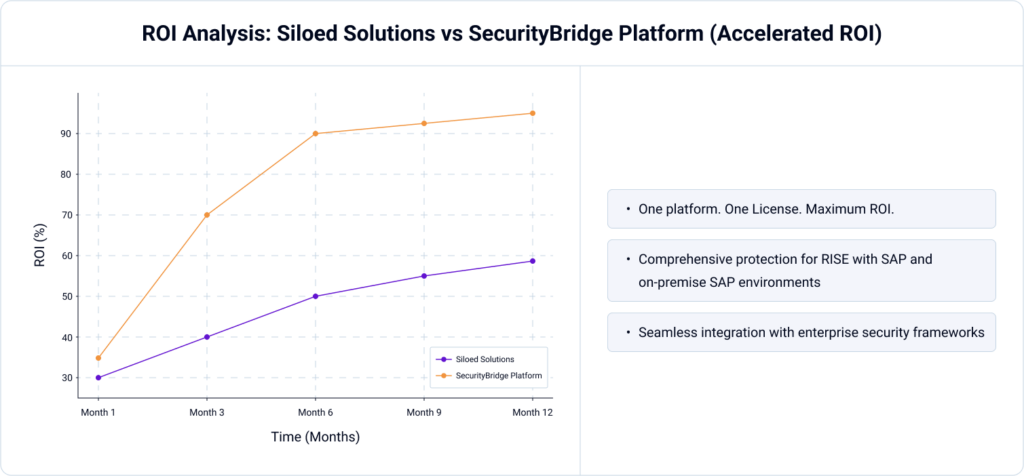
A Smarter Approach: Why SecurityBridge is the De Facto Standard for SAP Security
Note: This section I try to position as The Standard without too much detail. Due to focus of integration I believe this content is mainly relevant for CIOs.
The days of relying on multiple siloed security tools—each requiring separate licenses, integrations, and maintenance—are over. The smarter, more cost-effective solution? A unified SAP security platform like SecurityBridge.
Unlike fragmented solutions, SecurityBridge offers a fully integrated SAP security platform, ensuring:
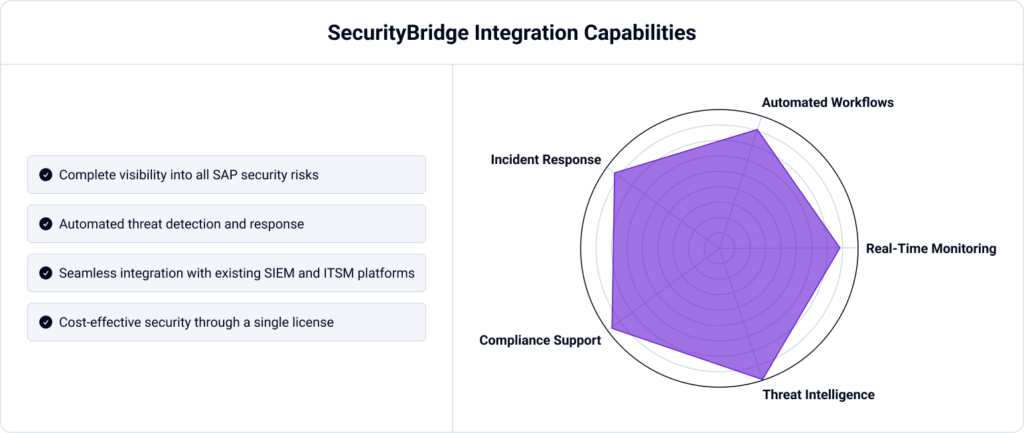
By consolidating SAP security under one comprehensive platform, SecurityBridge eliminates inefficiencies, optimizes security investments, and accelerates risk reduction.
The Future of SAP Security: 2025 and Beyond
We are entering an era where application security including SAP security will no longer be an afterthought—it will be a core component of enterprise cybersecurity.
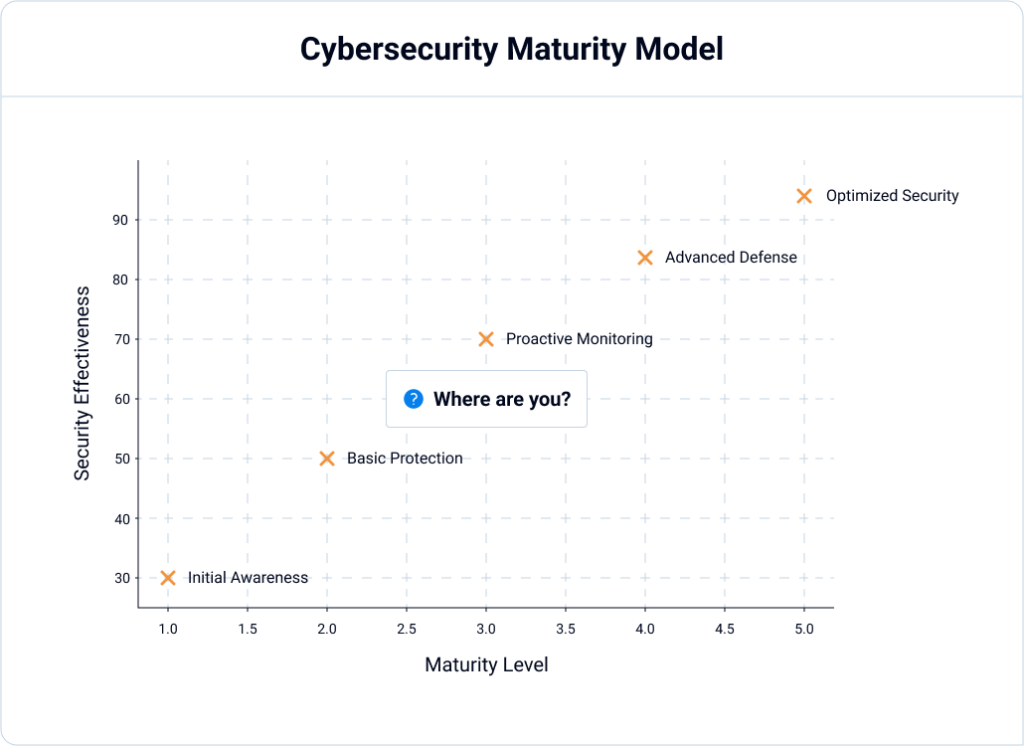
Where SAP Customers are Today:
🔴 Traditional cybersecurity (network, endpoint, cloud) is still ahead of SAP security.
🔴 SAP Customers are still reactive in SAP security, rather than proactive.
Where SAP Customers Will Be by 2025 with SecurityBridge:
✅ SAP security will reach near parity with traditional cybersecurity disciplines.
✅ Automated threat detection and compliance monitoring will become the standard.
✅ SAP will no longer be the weakest link in enterprise security.
By closing the long-standing security gap, SecurityBridge ensures enterprises are fully prepared for the future of cyber threats.
Conclusion: Don’t Wait Until It’s Too Late
The need for robust, integrated SAP security has never been more urgent. Enterprises that fail to secure SAP environments now will face severe financial, operational, and reputational risks. Also, they will have to carry the burden of violating internal and external regulations such as NIS2, the Cyber Resilience Act, or industry specific regulations like DORA.
SecurityBridge is the proven solution, already adopted by leading enterprises (link to customer references page) and endorsed by consulting firms like Accenture, KPMG, Deloitte, and PWC Germany.
The time to act is now. Is your organization ready for the next generation of SAP security?