
Pen Testing SAP Systems with Open Source Tools: Alternatives

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
What is Pen Testing?
Penetration testing, often referred to pen testing, is a simulated cyberattack designed to evaluate a system’s security by identifying and exploiting vulnerabilities. It helps organizations uncover weak spots in their defenses and provides valuable insights to strengthen security measures and protect sensitive data from potential threats.
Introduction to Pen Testing
SAP systems, which are crucial to many organizations as part of enterprise resource planning (ERP) solutions, manage critical operations and store sensitive data. With this importance comes increased risk, as SAP systems are often connected to the internet and frequently targeted by cyber attackers. While we advocate for a holistic approach to SAP Security that involves Threat Detection, Vulnerability Management, Patch Management, and Secure Coding analysis, there can be added value to SAP pen testing in specific cases. Although there are good commercial tools available for SAP vulnerability assessments, we’d like to share some alternative open-source tools that provide a cost-effective and flexible approach to SAP penetration testing. In this blog, we’ll explore the use of various open-source tools for SAP pen testing, including Nmap, RFC GW scripts, #10KBlaze exploit, Metasploit SAP URL scanner, Hashcat, SSLScan, and pysap. Considering the wide range of methods and different scenarios of SAP pen testing, we’re not aiming to cover every detail but to provide options for those seeking alternatives to, or replacements for, commercial tooling.
1. Using Nmap with an Adapted Services File for SAP
Nmap is a popular tool for network discovery (port scanning) and vulnerability scanning. It can be configured for SAP-specific service detection by replacing the ’services’ file. This allows Nmap to recognize SAP-specific services such as SAP GUI, RFC Gateway, SAPRouter, and many more.
Steps:
- Replace the ‘services’ file (e.g., ‘/usr/share/nmap/’ on Linux) with this.
- 2. Run Nmap to scan for SAP services:
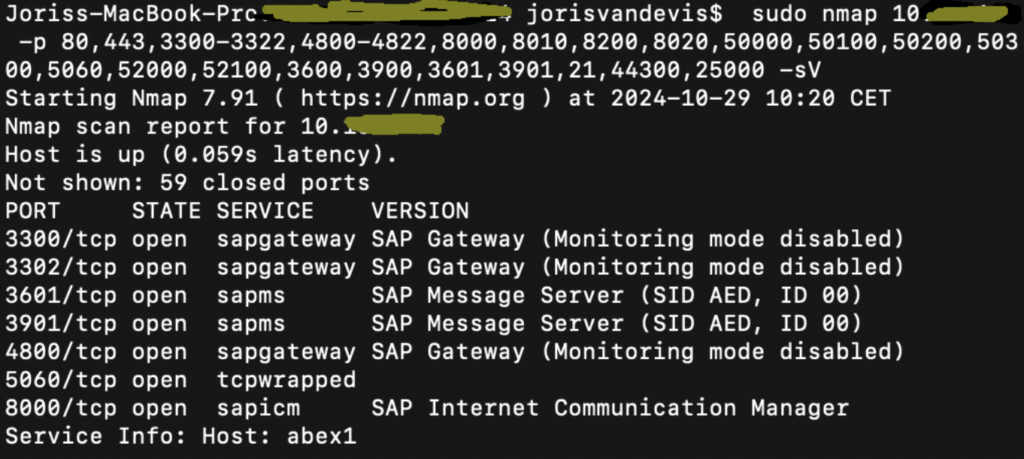
This configuration allows you to quickly identify open SAP-related ports and access the specific SAP services they serve.
2. SAP GUI and RFC Gateway Scripts
The SAP GUI provides a client interface for interacting with SAP systems, while the RFC Gateway allows remote procedure calls. Testing these components involves using scripts, such as PyRFC, to communicate with them. This allows you to detect exposed services, identify misconfigurations, and. Interact with or test SAP Gui screens.
An example of SAP RFC GW Scripts can be found on GitHub. These scripts aim to exploit misconfigured ACL files in the RFC Gateway, which for a long time were shipped by SAP in an insecure default state, allowing for Remote Code Execution:
➜python SAPanonGWv1.py -t 172.16.30.28 -p 3300 -c whoami
[*] sending cmd:whoami
n45adm
3. Exploiting #10KBlaze Vulnerability
The #10KBlaze vulnerability is a critical exploit affecting SAP systems. It takes advantage of misconfigured SAP Gateway and Message Server settings and exposed internal message server ports. This potentially allows remote attackers to register themselves as an SAP application server and execute operating system commands, gaining system control.
There are open-source scripts available that simulate an attack to check if your SAP systems are vulnerable to #10KBlaze. This provides a realistic view of the vulnerability’s impact and enables mitigation.
Example:
4. Metasploit SAP URL Scanner with Custom Wordlist
For many years, the Metasploit framework has offered different modules for SAP pen testing. One frequently used module is the SAP URL scanning, which can be extended with custom wordlists of SAP-specific URLs to enumerate potential entry points that might reveal misconfigurations.
Steps
Load Metasploit and select the SAP URL scanner module:
use auxiliary/scanner/http/sap_url_scanner
set RHOSTS <target_IP>
set WORDLIST <path_to_wordlist>
run
This enables the identification of exposed URLs or paths that might contain sensitive information or security misconfigurations.
5. Hashcat for SAP Password Cracking
If SAP password hashes are retrieved through vulnerabilities, misconfigurations, or overly extensive SAP authorizations, Hashcat can be used to attempt cracking these hashes, especially if they are weakly secured.
A resource with some examples can be found here.
6. SSLScan for Analyzing SAP SSL/TLS Configurations
Though not specific to SAP systems, the use of TLS is increasing rapidly with customers. To make sure a proper TLS setup is in place, you can use SSLScan or a similar tool. SSLScan is a useful tool for testing the SSL/TLS configuration of SAP systems. Ensuring proper SSL/TLS setup prevents man-in-the-middle attacks and provides encrypted communication.
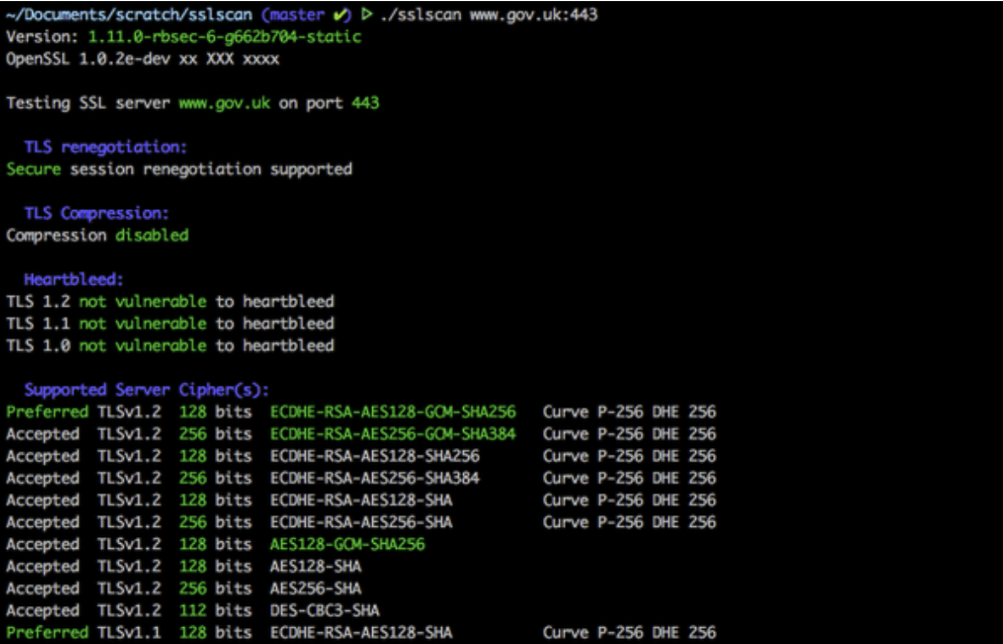
SSLScan will show the supported protocols, ciphers, and overall SSL/TLS configuration, helping to identify weak ciphers or unsupported protocols.
7. pysap – Specialized Library for SAP Security Testing
pysap is an open-source library created by Martin Gallo, specifically designed for SAP (security) testing. It provides modules and scripts for interacting with SAP’s internal protocols, such as SAP Router Protocol, Message Server, and Gateway Server. You can use it to automate complex SAP pen testing tasks and comes with many features such as:
- Dissection and crafting of the following network protocols:
- SAP Network Interface (NI)
- SAP Diag
- SAP Enqueue
- SAP Router
- SAP Message Server (MS)
- SAP Secure Network Connection (SNC)
- SAP Internet Graphic Server (IGS)
- SAP Remote Function Call (RFC)
- SAP HANA SQL Command Network (HDB)
- Client interfaces for handling the following file formats:
- SAP SAR archive files
- SAP Personal Security Environment (PSE) files
- SAP SSO Credential (Credv2) files
- Library implementing SAP’s LZH and LZC compression algorithms.
- Automatic compression/decompression of payloads with SAP’s algorithms.
- Client, proxy, and server classes are implemented for some of the protocols.
- Example scripts to illustrate the use of the different modules and protocols.
Using pysap, you can automate advanced SAP vulnerability assessments, especially those that focus on SAP proprietary protocols.
Conclusion
Open-source tools provide a flexible and cost-effective approach for SAP penetration testing, enabling organizations to better secure their SAP systems against potential attackers. These tools help to detect vulnerabilities, allowing organizations to prioritize remediation efforts.
With tools like Nmap, pysap, Metasploit, and Hashcat, security professionals can comprehensively assess their SAP environment. Penetration testing, both manual and automated, plays a crucial role in identifying and mitigating security risks. It’s essential to perform these tests in a controlled, authorized manner, as SAP systems are business-critical, and unauthorized testing can lead to significant disruptions. However, when properly implemented, these tools can provide invaluable insights into potential vulnerabilities, helping to safeguard critical SAP infrastructure.
SAP pen testing can add value in specific scenarios, but it is not a replacement for a holistic approach to SAP Security. SecurityBridge offers a comprehensive range of solutions to enhance security and efficiency across various business functions. With features like Threat Detection, Vulnerability Management, Patch Management, and Custom Code Security, SecurityBridge helps you efficiently improve the security of your SAP systems. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn.

