
Practical Exploitation of SAP Vulnerability CVE-2021-44231
Chapters
Share Article
In this article, we want to talk about the practical exploitation of SAP vulnerability CVE-2021-44231 and provide a solution to address it.
Operating System Command Injection in SAP NetWeaver ABAP
In SAP’s patch round of December 2021, an SAP Security patch was released with a CVSS score of 9.9/10 named “Code Injection vulnerability in SAP ABAP Server & ABAP Platform (Translation Tools)”. This particular type of vulnerability is quite common in SAP systems (we have to date reported more than 30 similar vulnerabilities to SAP) and can easily lead to a full system compromise. Our SAP Security research led to finding this vulnerability and in close cooperation and via responsible disclosure, the SAP Security response team resolved it.
As stated in the SAP note, the vulnerability we discovered was introduced in SAP systems by accidentally releasing internal programs to customers. Also, many SAP systems are vulnerable as the bug is part of the SAP_BASIS software component, a key component in every SAP ABAP system. But what does “vulnerable” mean in this case and how could attackers take advantage of this vulnerability? As stated by SAP, the vulnerability can lead to controlling the behaviour of the application and all its data:
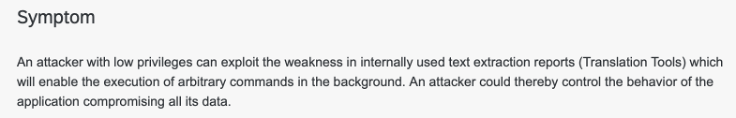
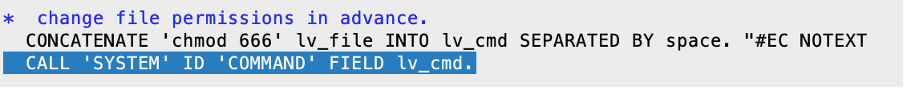
Therefore, these vulnerabilities are powerful in the hands of malicious parties. The only good thing here is that this vulnerability requires some level of authentication and authorisation. Yet, any user with the right to execute ABAP report RS_LXE_EXTRACT_WORK_LIST2CSV can abuse it to escalate privileges and go for the jackpot. The specific issue is in the CALL ‘SYSTEM’ command that does OS command execution and can be altered by input from the selection screen:
Practical exploitation
To exploit this vulnerability, one only has to execute report RS_LXE_EXTRACT_WORK_LIST2CSV via e.g. transaction SE38 in the background and specify any file (which does not have to exist) followed by a “;” sign followed by ANY FREE TO CHOOSE OS COMMAND like in below case the “mkdir” command to create a directory.
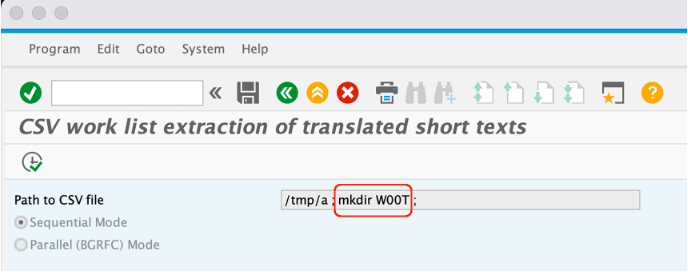
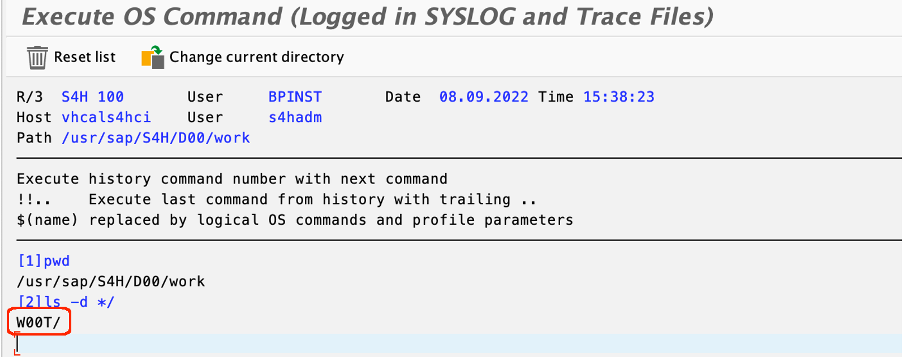
This, in turn, will write some data to the chosen file, but additionally execute that OS command on the SAP system as can be seen here (the directory W00T has been created which means the freely chosen command was executed successfully):
Why is this a bad thing?
If you are allowed to execute any OS command, you could do things on the operating system you are not supposed to do, like stopping an SAP system for example. Which is a bad thing for the availability of the system. But it does not stop there since the OS user (typically named <sid>adm for non-windows systems) has an implicit trust relation with the database. What this means is that via OS commands you can directly speak to the database and read all data or alter it. What makes things worse is that this is NOT being logged from the SAP application layer. If you would for example execute an OS command like below, you could retrieve password hashes for all users and try to bruteforce these offline to gain access to other SAP accounts.
/tmp/a ; hdbsql -U DEFAULT “select PWDSALTEDHASH from USR02”
How to fix this?
Just import the SAP Security note 3119365 via transaction SNOTE. This will introduce proper validation of the input from the selection screen and provide an error message when you try to exploit the vulnerability:
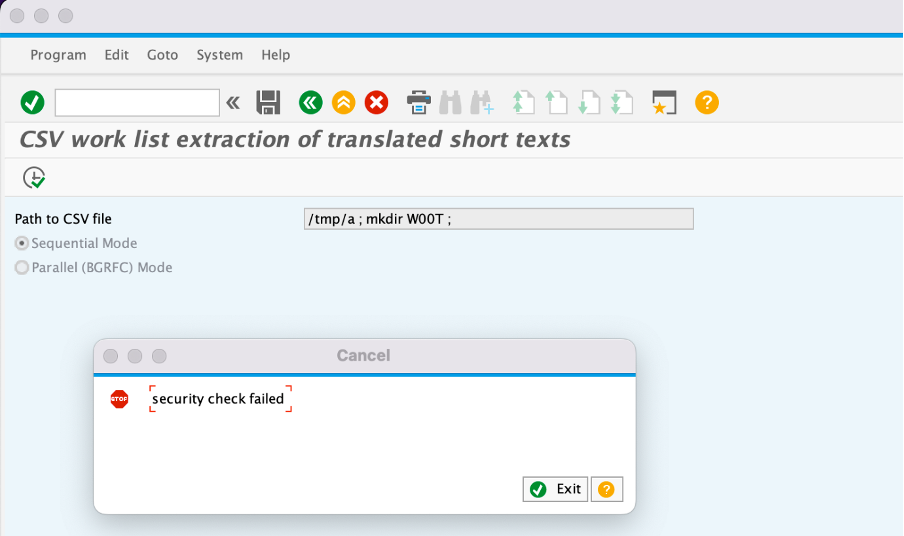
The above vulnerability can be easily patched, having a proper Vulnerability Management process in place helps there. It cannot be stated enough that a Vulnerability Management process should be in place to address and fix these vulnerabilities in a timely, efficient and effective manner for SAP customers to prevent abuse.

