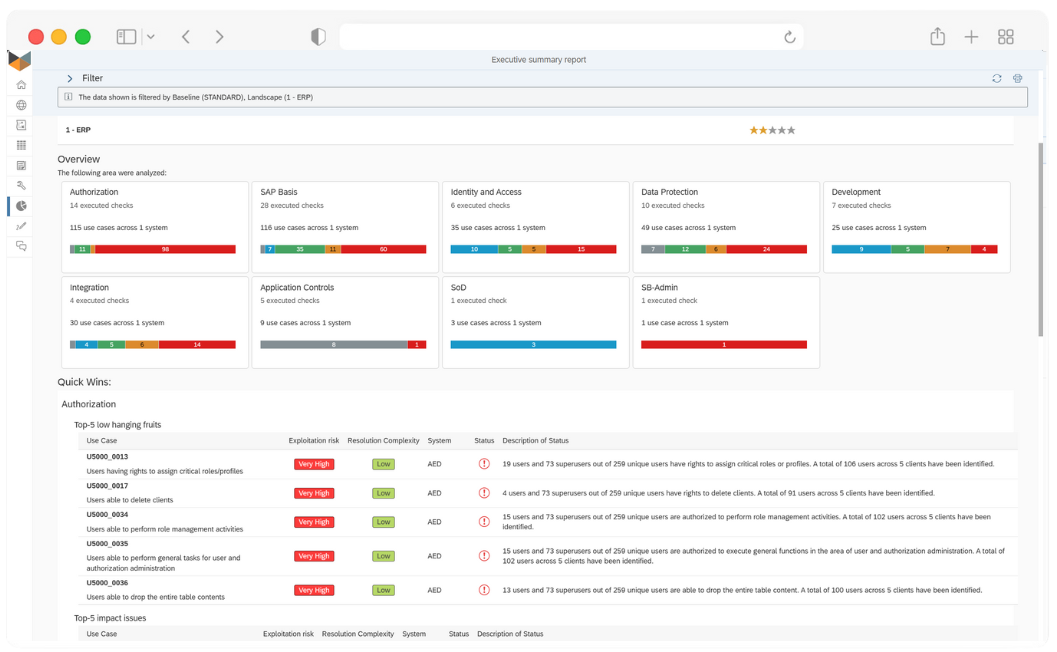
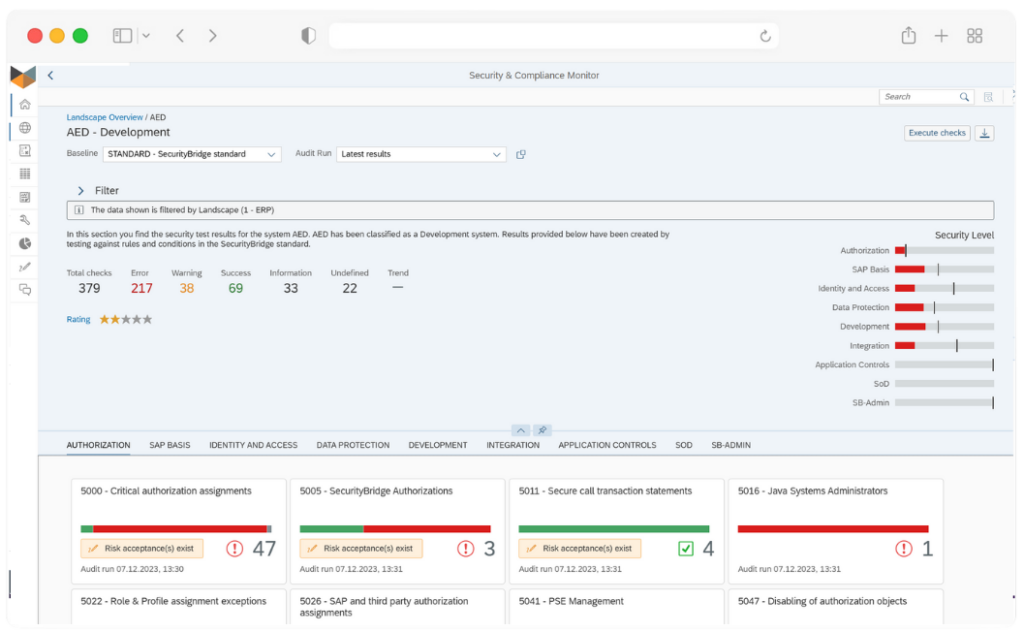
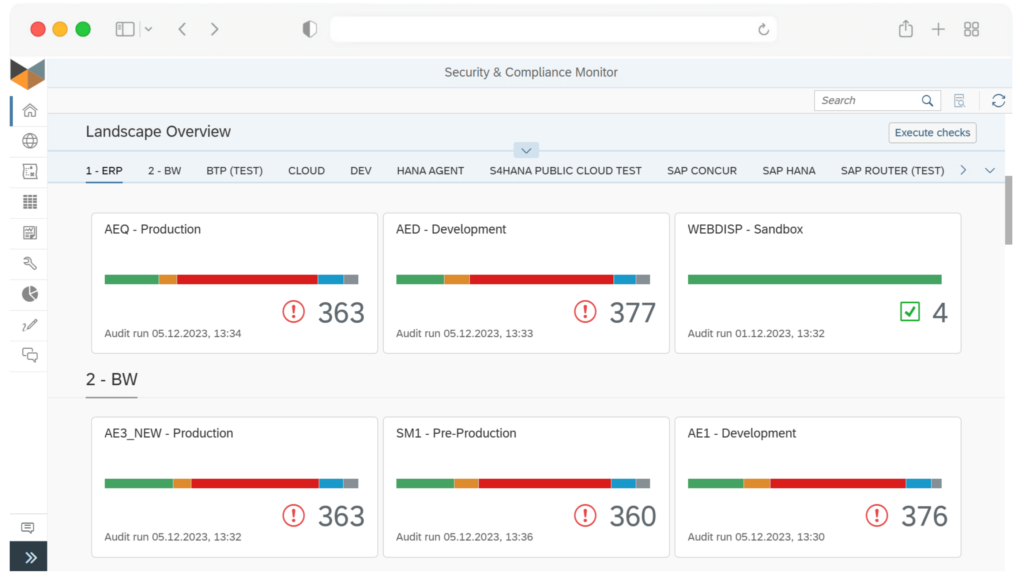
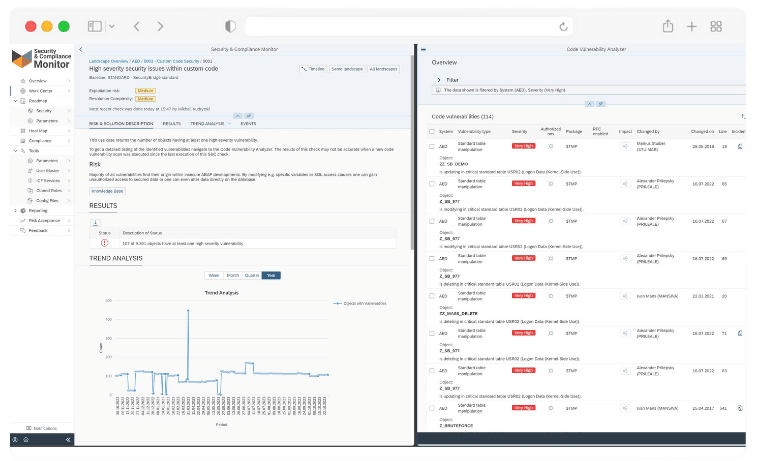
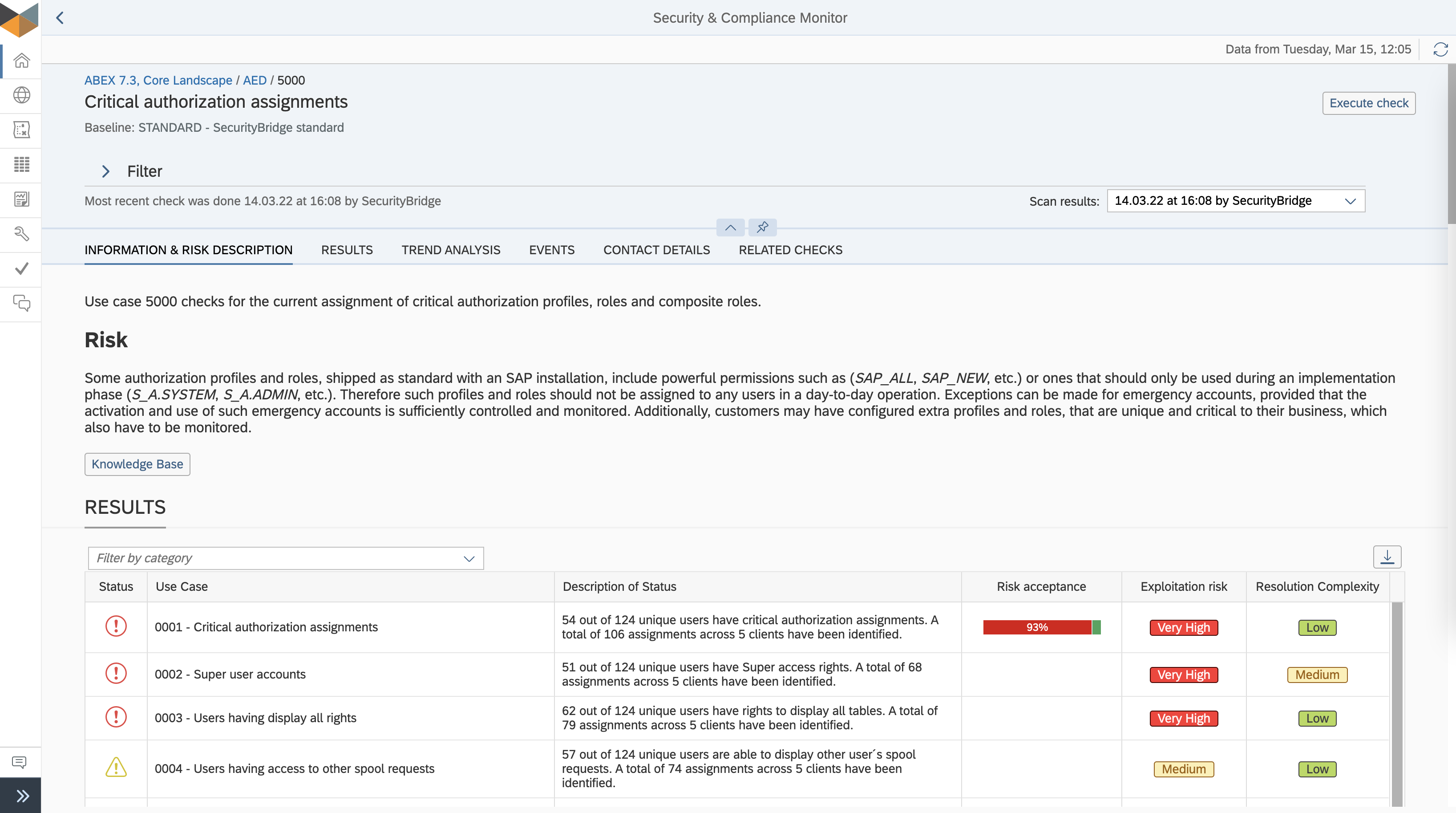
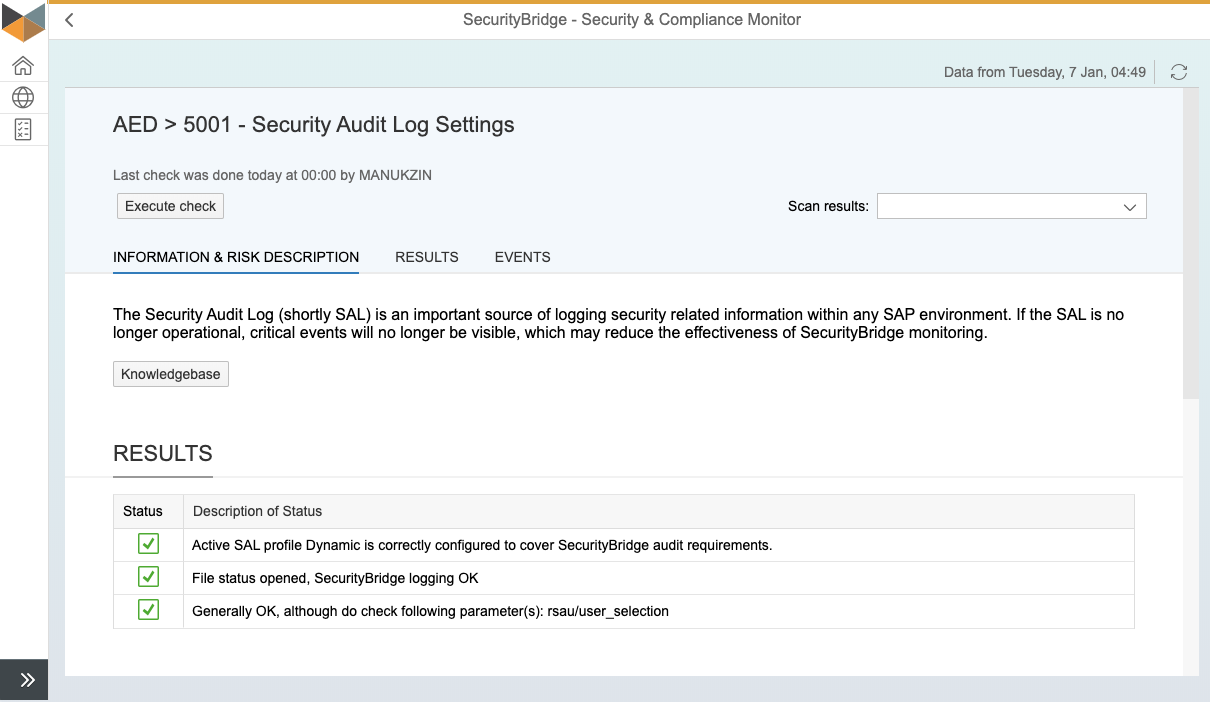
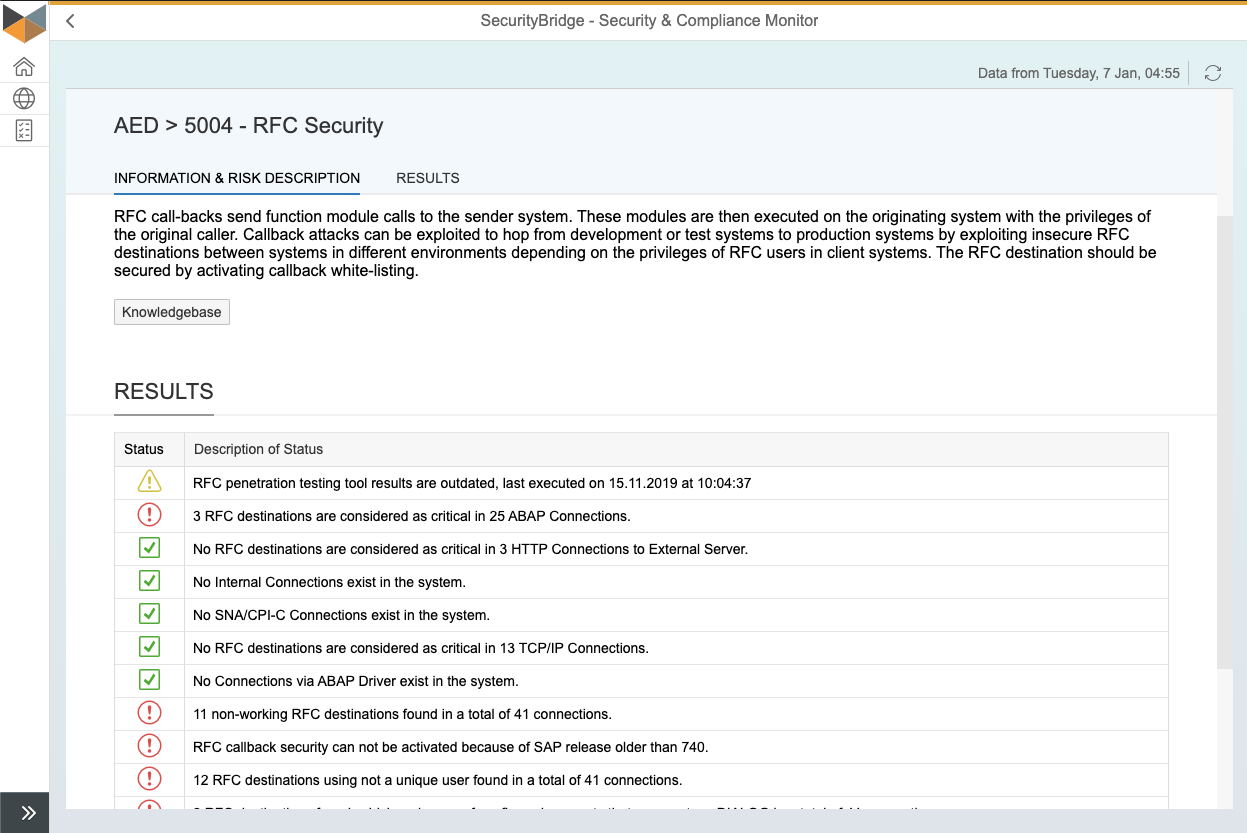
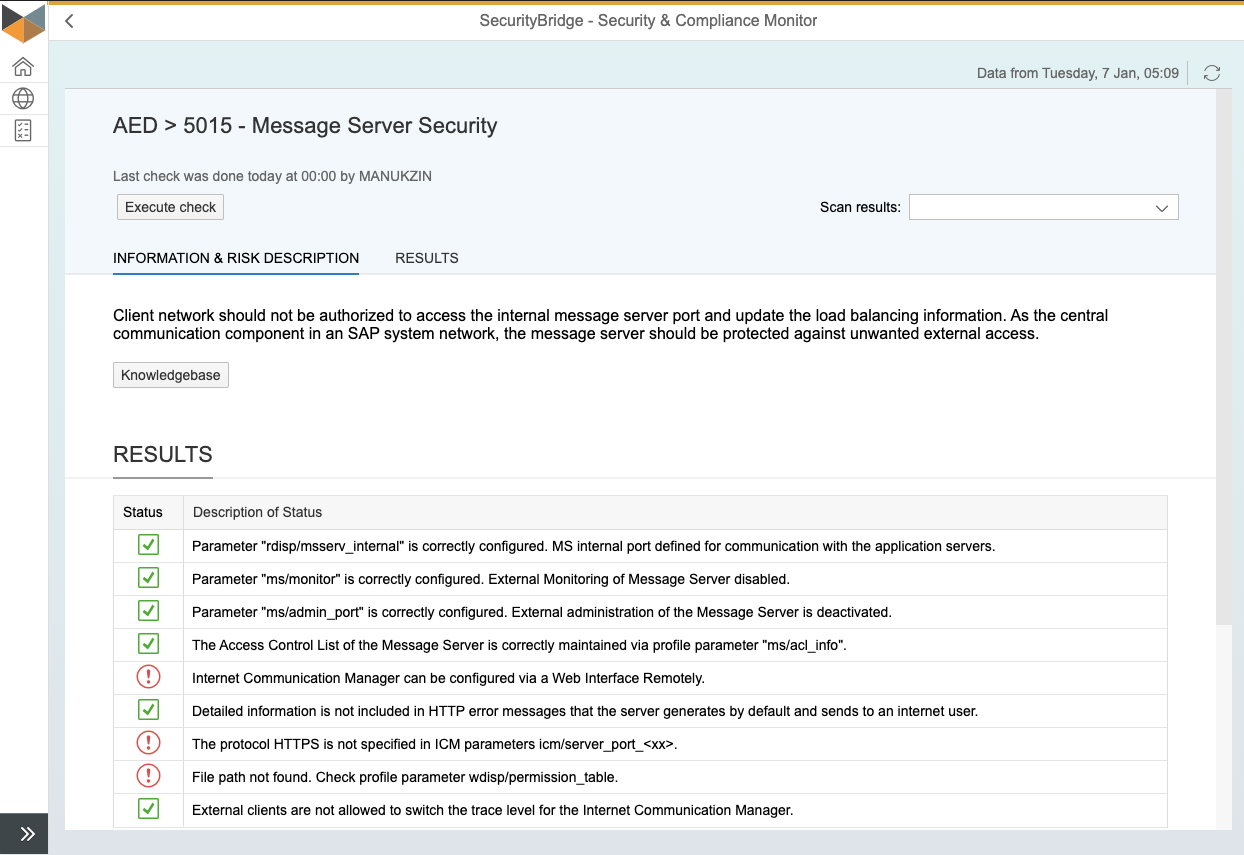
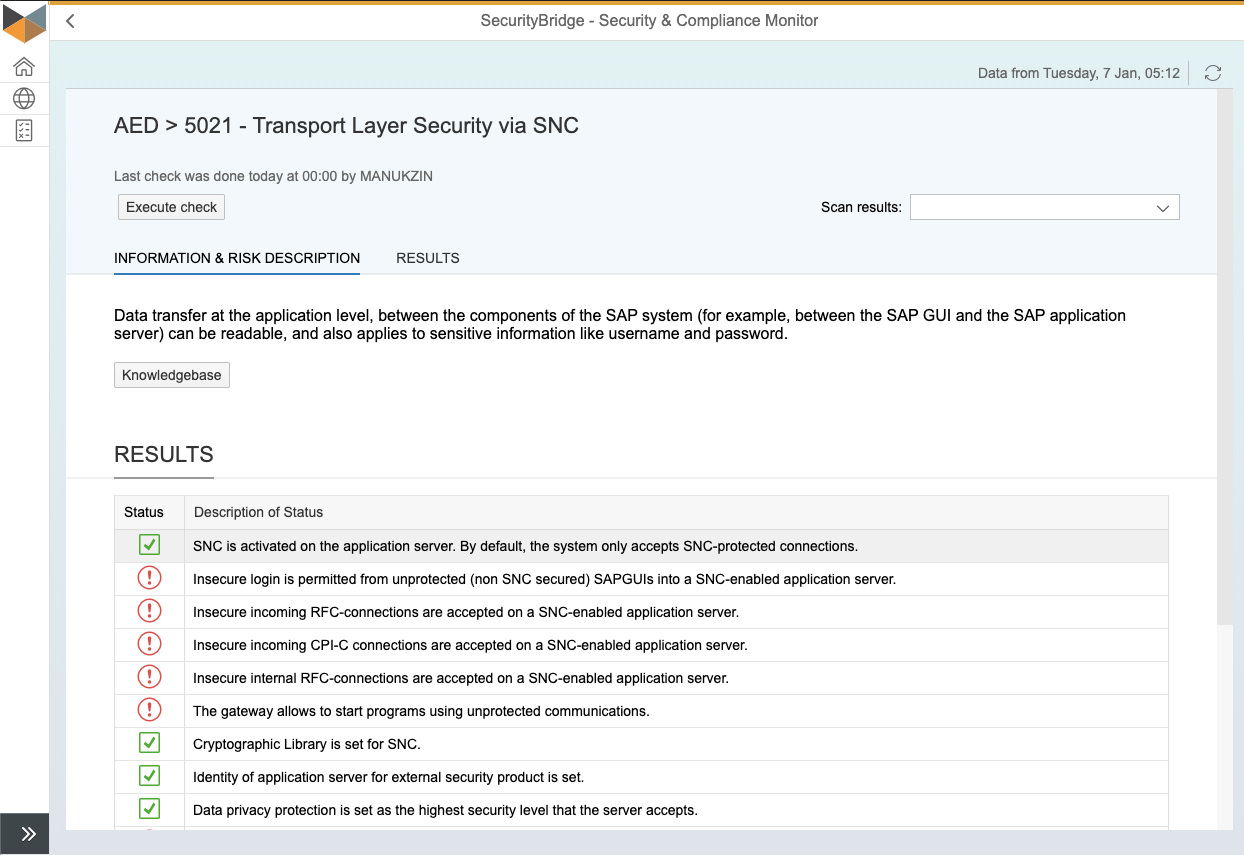
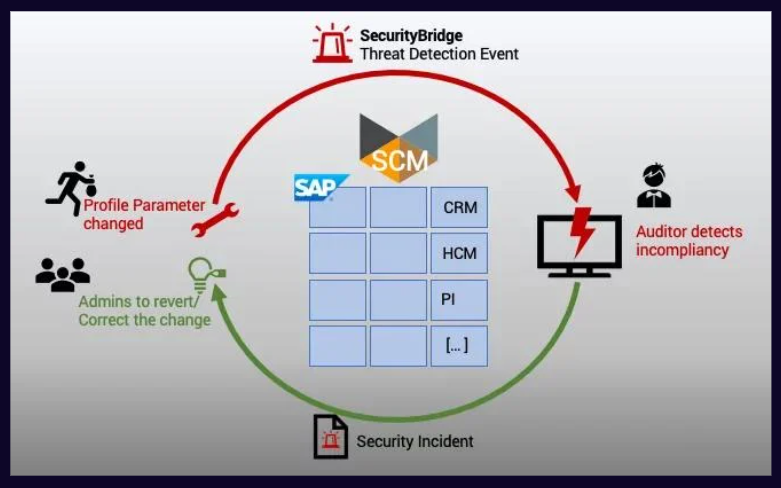
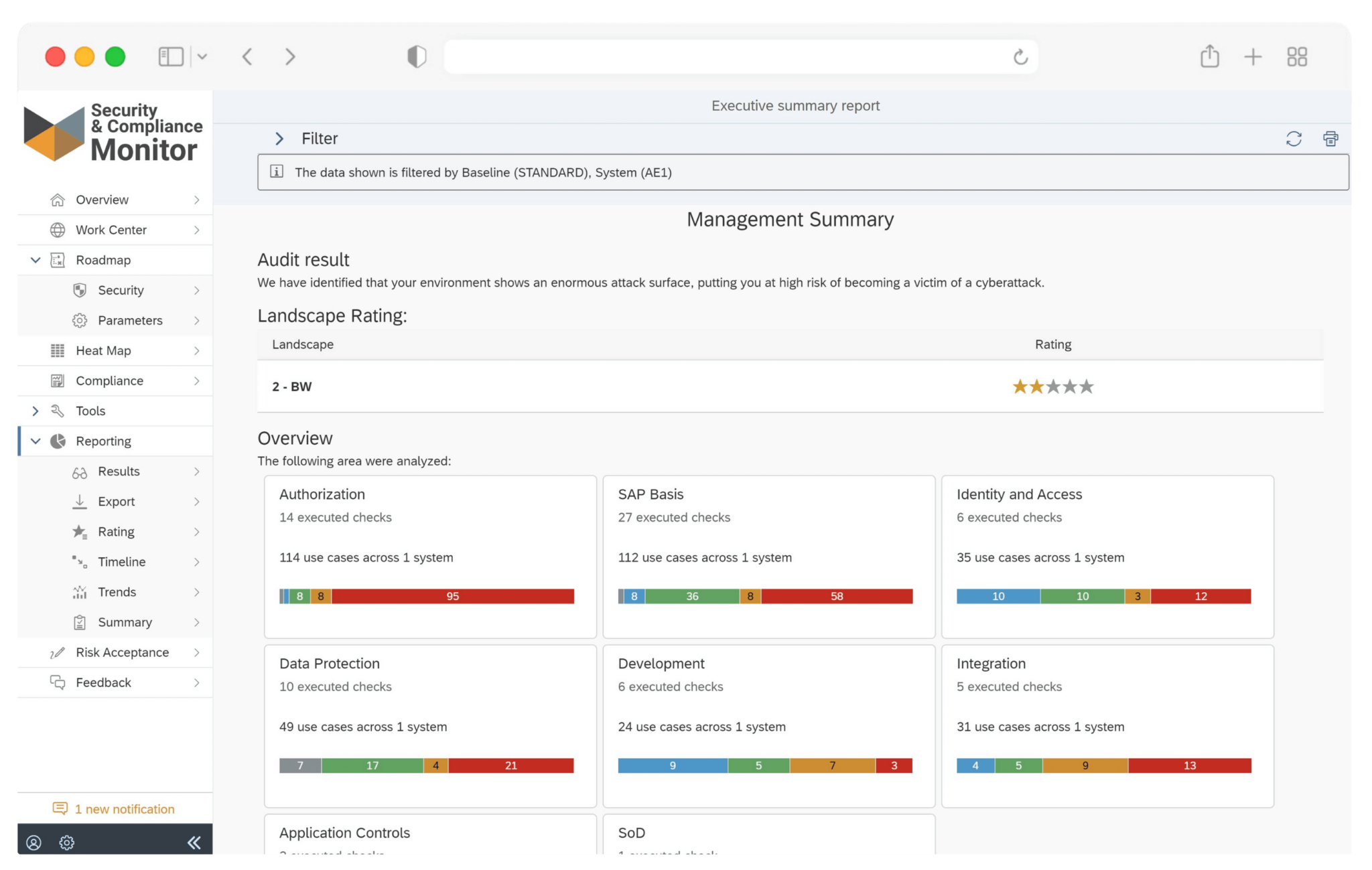
Are you looking for a condensed document providing all the information about SecurityBridge’s SAP Vulnerability Management?
The solution brief combines all the relevant information you need to know about the vulnerability management capabilities of SecurityBridge for SAP.