SAP Patching vs. Detection: Shifting priorities for SAP Security

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
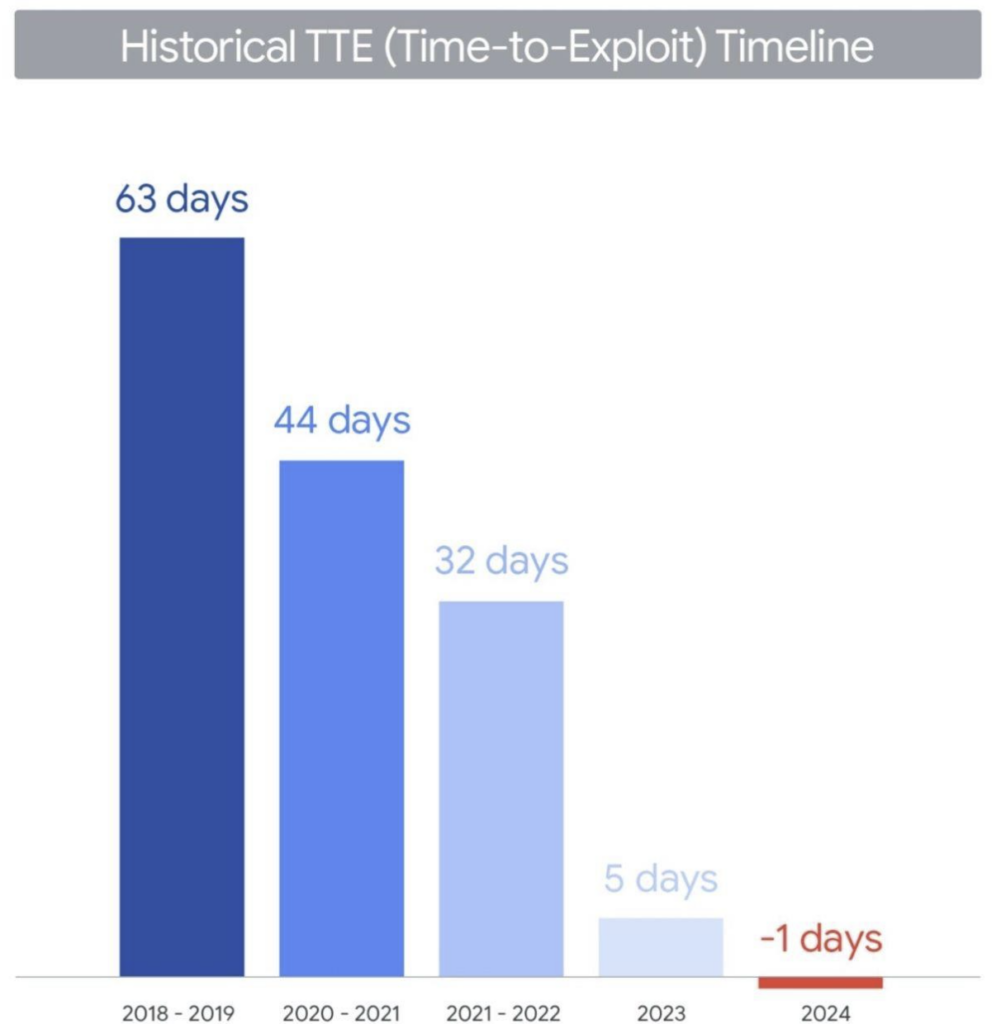
From an unfortunately not public report from Mandiant, The Time-to-Exploit timeline shows how quickly attackers weaponize new vulnerabilities, highlighting the shrinking window for patching.
For years, patching has been the cornerstone of cybersecurity. Applying updates and SAP Security Notes reduces the attack surface and closes known weaknesses before attackers can take advantage. In SAP landscapes, where business-critical processes run, keeping systems patched remains a must.
However, relying on patching alone is no longer enough. The reality is that:
- New vulnerabilities emerge constantly — attackers can exploit them within days.
- Patching often lags — due to testing cycles, downtime constraints, and business priorities.
- SAP environments are highly customized — meaning not every threat always has a straightforward patch.
- Attackers go beyond missing patches — using stolen credentials, privilege abuse, misconfigurations, and “living off the land” techniques that patches can’t prevent.
This is why detection has become just as critical — if not more so — than patching.
Modern SAP security must include continuous monitoring of transactions, user behaviour, and system activity to spot suspicious actions quickly. Detecting anomalies such as unusual background jobs, privilege escalations, or abnormal transaction use allows organizations to respond before damage occurs.
The strongest SAP security posture combines both:
- A disciplined patch management process to close known vulnerabilities.
- Robust detection capabilities to identify the unknown and catch attacks in progress.
In today’s threat landscape, where the window between discovery and exploitation is shrinking, detection is often the deciding factor in preventing a breach.
Yet, Effective Vulnerability Management in SAP goes beyond simply installing the monthly SAP Security Notes. It requires a structured process that evaluates system configurations, timely applies security patches across SAP and third-party components, and addresses vulnerabilities introduced by custom code. For more details, see this earlier blog post.
👉 If SAP is at the core of your business, now is the time to ask: How mature is your detection strategy? Patching will always be essential — but without strong detection, critical risks will remain unseen until it’s too late.
🔗 Original inspiration:

