Elevating SAP Cybersecurity: The Strategic Imperative of an SAP SIEM Integration
Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
In today’s digital landscape, SAP solutions are central to business operations but also prime targets for cyberattacks. While SAP offers internal security features, integrating Security Information and Event Management (SIEM) systems with SAP is essential for comprehensive cybersecurity.
SIEM systems collect, normalize, and analyze security-relevant logs from across IT infrastructures. This integration bridges the gap between SAP-specific monitoring and enterprise-wide security, enabling rapid detection and response to threats. For many organizations, the first challenge in integrating SAP logs with SIEMs is managing the complexity and high volume of logs.
Understanding SIEM Integration for SAP Solutions
SAP SIEM integration is a challenging process that involves connecting SAP systems to a SIEM platform to export and analyze security-relevant logs alongside non-SAP data. This unified approach helps identify complex attack patterns across SAP applications.
Key challenges include the complexity of SAP systems, high log volume, and managing numerous integration points. Effective integration overcomes these obstacles, providing holistic visibility and reducing false positives.
A structured approach to implementing SIEM integrations for SAP environments is essential to ensure a successful deployment and minimal disruption. There is a need for secure SAP system integration and monitoring to meet security and compliance requirements.
Key Features of SAP SIEM Integrations
SAP SIEM solutions are equipped with several key features that significantly enhance cybersecurity across SAP landscapes:
Real-time threat detection, powered by machine learning algorithms, enables organizations to identify and respond to cybersecurity threats as they emerge.
Correlation capabilities provide transparency by connecting events across SAP systems, making it easier to monitor and manage security incidents.
Providing centralized, real-time intelligence and response capabilities to threats.
Support data governance by ensuring that all security events are tracked and managed in compliance with organizational policies.
The combination of these features provides crucial visibility into SAP environments, enabling organizations to detect, analyze, and respond to threats with greater speed and accuracy.
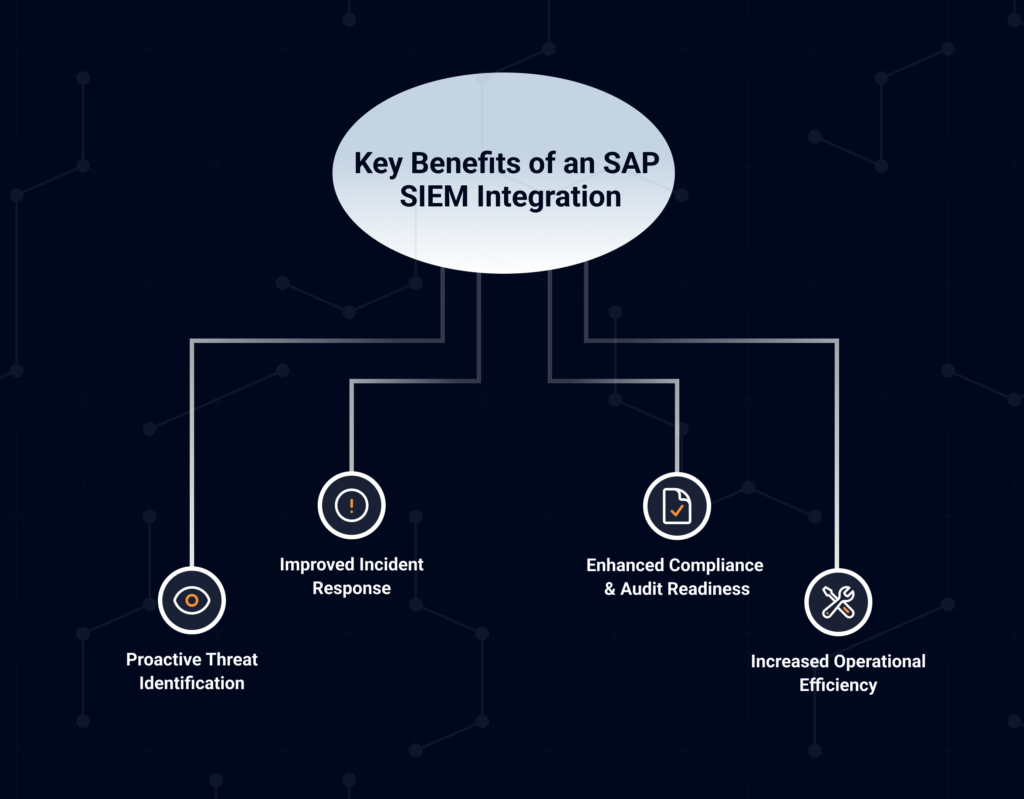
Key Benefits of an SAP SIEM Integration
Proactive Threat Identification
Continuous monitoring of SAP logs enables the early detection of suspicious activities using attack detection patterns and behavioral analytics, which can help Security Operation Centers (SOC) detect critical threats and indicators of compromise, facilitating more effective incident response.
Improved Incident Response
Centralizing SAP logs enables quick investigation and response to SAP-specific incidents, minimizing business impact. Effectively responding to these incidents ensures that SOCs can address threats promptly and reduce potential risks.
Enhanced Compliance and Audit Readiness
Capturing all relevant SAP events supports regulatory compliance and maintains clear audit trails, with user pseudonymization protecting privacy during investigations. These results provide valuable evidence for compliance and audit readiness.
Increased Operational Efficiency
Automated log collection and alerting reduce manual workloads and help SOCs focus on critical threats. This automation enables companies to manage SAP security easily, even if they lack in-depth SAP expertise.
Real-Time Monitoring and Threat Detection
SIEM integrations provide immediate visibility into SAP activities, allowing SOCs to monitor what is happening in real time, enabling detection of unauthorised access, event correlation across systems, and reduced mean time to detect and respond to threats. SIEM solutions help security teams understand SAP activities and security events by presenting complex SAP logs in an easily digestible format. SAP logs can also be integrated directly into SIEM solutions for real-time security monitoring.
Essential Data Sources for SAP
Key log sources include various data sources such as SAP Security Audit Logs, System Logs, Change Documents, Application Logs, Database Logs, Operating System Logs, and Network Logs.
Filtering for security-relevant events is crucial for managing log volume and preventing SIEM platforms from being overwhelmed. Logs generated by SAP systems can be filtered to reduce noise and then searched to identify relevant security events. The ability to search through filtered SAP logs enables security teams to detect and respond to security incidents quickly.
Log Management in a SAP SIEM Integration
Effective log management collects, correlates, and analyses SAP log data to uncover attack patterns, reduce false positives, and support compliance with data protection standards. Logs can grow rapidly over a short period, which impacts storage, analysis, and network bandwidth requirements. Ongoing maintenance is required to ensure effective log management and integration. It might also be necessary to install log collectors or agents on SAP systems to enable log forwarding to SIEM platforms.
Security Event Management and Log Correlation
By analysing log data from various sources – including the SAP Security Audit Log – organisations can create a unified view of activities across their SAP systems. This process is essential for detecting attack patterns and identifying anomalies that may signal security threats.
The ability to correlate information from multiple log sources allows security teams to overcome several challenges, such as managing terabytes of log data and filtering out irrelevant information.
Through comprehensive log correlation, SAP SIEM integrations enhance security monitoring, making it possible to detect and respond to potential threats that might otherwise go unnoticed in complex SAP environments.
Minimising False Positives
Minimising false positives is a crucial goal for any SAP SIEM solution. Excessive false alerts can overwhelm security teams, leading to alert fatigue and the risk of missing genuine threats.
SAP SIEM platforms should address this challenge by leveraging features such as machine learning and advanced log correlation, which help distinguish between routine activity and real security incidents. The SAP SIEM integration should facilitate to only capture security-relevant events to ensure effective security monitoring and avoid excessive SIEM licensing costs.
Practical Approaches to SIEM Integration
Common methods include direct connectors/APIs, syslog forwarding, custom ABAP extractors, third-party solutions that provide filtering, normalisation, and pre-built threat scenarios, and integration approaches tailored for environments like SAP Business Technology Platform.
Key considerations include managing log volume, enriching data context, ensuring secure data transmission, and refining detection rules.
Building a Robust SAP Security Posture
SAP SIEM integration enables proactive threat detection and response, improving collaboration between SAP and cybersecurity teams. It strengthens security posture, ensures continuous compliance, and protects critical business assets from evolving cyber threats.
By adopting best practices and leveraging advanced SIEM capabilities, organisations can achieve comprehensive SAP security monitoring and rapid response, essential for safeguarding large SAP landscapes in a complex threat environment.
To further enhance your SAP security, use SecurityBridge’s SIEM integration for SAP. We support all major SIEMs, including Microsoft and Splunk.


