
Unlocking secure and efficient communications with SAP Unified Connectivity (SAP UCON)

Chapters
Share Article
In today’s complex business environment, the seamless integration of various IT systems is paramount for operational efficiency and data integrity. SAP Unified Connectivity (SAP UCON) addresses these needs by offering a robust framework for secure and streamlined communication between SAP systems and external applications or services. This blog post delves into the essentials of SAP UCON, exploring its components, benefits, and best practices for implementation.
What is SAP Unified Connectivity (SAP UCON)?
SAP UCON is a security framework designed to manage and control remote function calls (RFCs) within the SAP landscape. It is part of the broader SAP technical platform, was introduced in NetWeaver 7.40, and focuses on enhancing security, reducing the attack surface, and ensuring compliance. UCON provides a structured approach to handling RFC communications, making it easier to monitor, authorize, restrict, and secure interactions between different systems.
Modern SAP S/4HANA systems contain around 50.000 Remote-callable Function Modules (RFMs), while only a small fraction of those are used by customers. While authorizations are important to restrict the usage of these RFMs, UCON helps you to completely block unused RFMs and reduce the attack surface drastically.
UCON places an additional layer of security on top of authorizations, using the following approach:
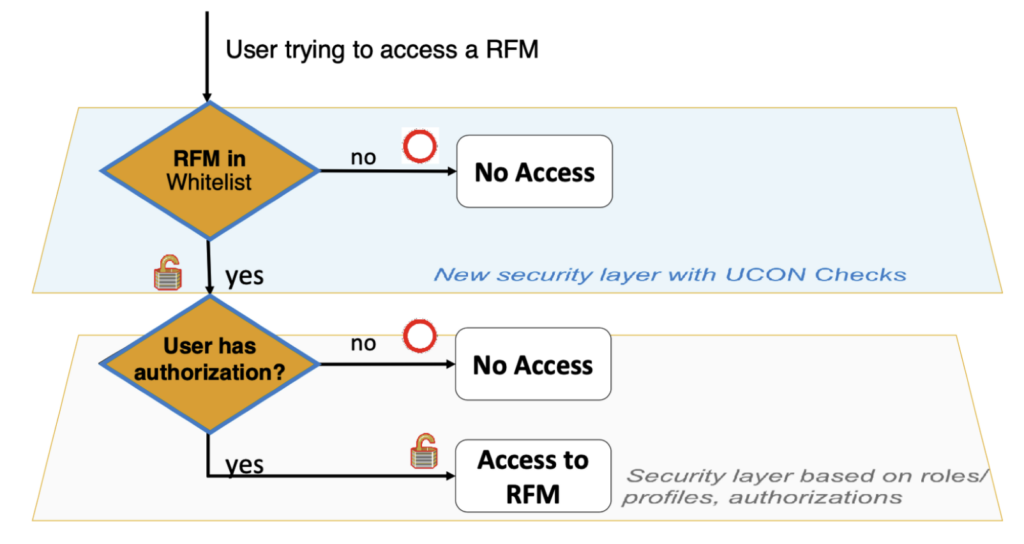
Setting up UCON is often handled by the SAP administrators and involves the initial setup of the UCON allow list, followed by continuous maintenance of this list.
SAP UCON setup and configuration
To activate UCON, follow these steps:
- Set the UCON profile parameter UCON/RFC/ACTIVE to 1 to enable UCON runtime checks for RFMs in the final phase.
- Run the UCON setup to generate a default communication assembly (CA) and other required entities.
- Choose a suitable duration for the logging and evaluation phase.
- Schedule the batch job SAP_UCON_MANAGEMENT that selects and persists the RFC statistic records required by the UCON phase tool on the database.
The next important step is to define which RFMs should be placed on the whitelist (CA). SAP recommends following these steps to define them:
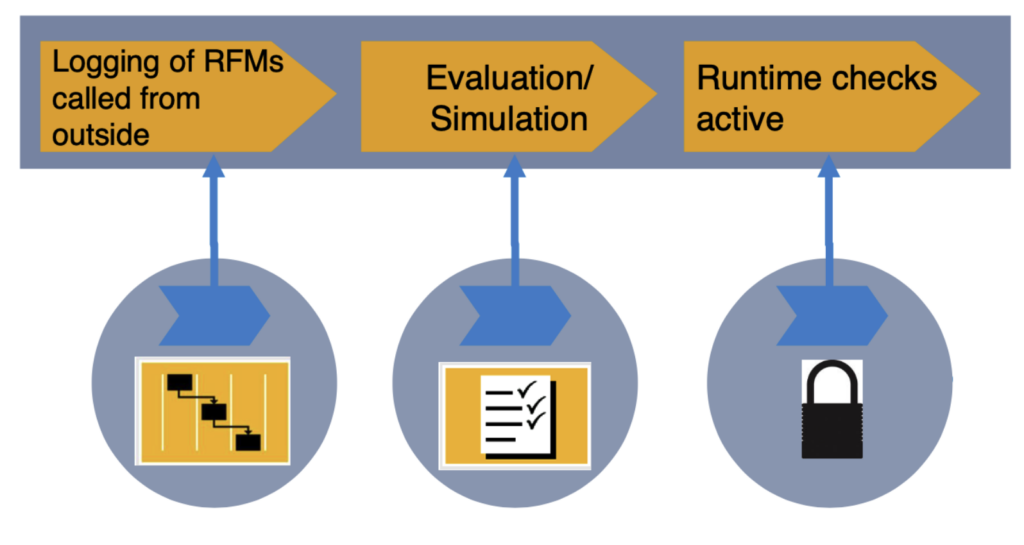
The first phase involves using logging to see which RFMs are called in your SAP landscape over time. This can be within UCON or through the monitoring capabilities of the SecurityBridge platform. Be sure to include key activities, such as a year-end closure or upgrade to ensure no RFMs are missed.
In the second phase, you can already see how well your whitelist works, while still having a fallback in case RFMs are called that are not on the whitelist. During this simulation phase, you can choose not to have them blocked yet to ensure business continuity.
During the third phase, you set the whitelist active and block other RFMs. By doing so, you can block 95% of RFMs on average, leaving only 5% of RFMs, reducing your attack surface significantly.
Based on our experience conducting SAP penetration testing for over a decade, we can confirm that the use of UCON significantly improves security. Although we do not see it active with many customers yet, those who use it are already seeing considerable benefits. A typical pentest scenario in SAP landscapes involves moving laterally via type 3 connections through the landscape after breaching at least one SAP system. However, with the use of the UCON, this lateral movement is much harder as many RFMs typically used in such attacks are blocked.
Conclusion
SAP Unified Connectivity (UCON) is a critical component of the SAP ecosystem, providing a robust framework for secure and restricted efficient RFC communications. By leveraging UCON, organizations can enhance security, ensure compliance, and streamline integration processes. Whether in financial services, healthcare, manufacturing, or other industries, SAP UCON offers the tools and capabilities needed to drastically reduce the attack surface across the SAP landscape. By following best practices for implementation, businesses can maximize the benefits of UCON and ensure a secure and resilient IT environment.
Try SecurityBridge and immediately improve the security of your SAP systems! For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn.

