Chapters
Share Article
Most SAP customers today would probably agree that SAP Security is important. However, it is often considered a necessary evil rather than a means to save time and money. After talking to many of our customers about their experience in the first months of their SAP Security journey, they all confirmed that they achieved significant time savings for their SAP Patch Management process. So, let’s look at the challenges of the monthly patching of SAP systems and how these customers showed a quick ROI via automation, especially by using our Patch Management solution.
SAP Patch Management – a monthly burden
SAP Security teams mark the second Tuesday of the month in their calendars as SAP Patch Day. On this day, SAP releases new security patches, called SAP Security Notes, to address known vulnerabilities in SAP systems and applications. These vulnerabilities have different severities based on their CVSS (Common Vulnerability Scoring System) score and the most critical ones are called “Hot news”. Whenever SAP Security teams see these “Hot news” on “Patch Tuesday”, they know that immediate action needs to be taken as their SAP systems are at high risk.
The run against the clock starts and time is of the essence, as hackers can exploit those vulnerabilities anytime. However, in a complex SAP landscape, it is very challenging for SAP Security teams to figure out for each patch:
- Which are the relevant systems?
- What are the prerequisite (manual) tasks?
- What is the impact of the patch?
- Which systems are more critical than others and might need patches earlier (e.g. internet exposed systems)
- Do we need testing, and if so, how detailed should it be?
As SAP teams are always short on capacity, accomplishing all these tasks manually becomes a real monthly burden. In addition, they need to coordinate the security patching with the other system changes and align with the maintenance windows that are part of a standard SAP Change Management process. However, the bad news doesn’t stop here. In the long term, the SAP team must take care of all patches, not just those labeled “Hot News”. If the team is not capable of implementing all necessary patches within a month, the next Patch Tuesday will increase the backlog, and the burden only becomes bigger.
First aid: Virtual Patching
Even the best SAP Security teams need at least 24 hours to get the “Hot News” implemented. During this period, their SAP environment remains at risk, therefore they should have a risk mitigation plan that helps increase the visibility of potential attacks. The so-called “Virtual Patching” is a methodology that helps in this case.
With Virtual Patching, SAP Security teams gain extra time, and the flexibility needed for their patch implementation schedule. They also avoid extra downtime by installing the patches with other regular SAP changes. This is all possible as Virtual Patching acts like a “vulnerability shield” by adding protection against internal and external threats impacting the SAP systems.
The SecurityBridge Platform also has Virtual Patching built in. It begins with an automated update of our monitoring templates and vulnerability check baselines, enabling customers to leverage the latest threat intelligence continually. Shortly after SAP releases the Security Notes, the customers have their security signatures updated, too.
To learn more, see our threat detection for SAP and vulnerability management offerings.
The Virtual Patching feature connects the information from the SAP Security Notes with the security signatures, allowing customers to see which monitoring listener or vulnerability check will provide that compensating control until the corresponding patch is implemented. When, for example, an SAP Security Note indicates a vulnerability in an ABAP program, the settings for the listener that monitors critical transactions & programs will automatically monitor that affected program until the patch is implemented. SAP Security administrators are then alerted whenever the program is used so that they can double-check that the activity is part of a normal process. The alerting automatically stops once the corresponding patch is installed.
How to streamline & automate SAP Patch Management
While Virtual Patching gives SAP Security teams extra time and flexibility, they still need to work on setting up a mature Patch Management process to keep up with the monthly SAP patch releases. This means that several tasks within the Patch Management process must be streamlined and automated steps should be weaved in wherever possible for the highest process efficiency.
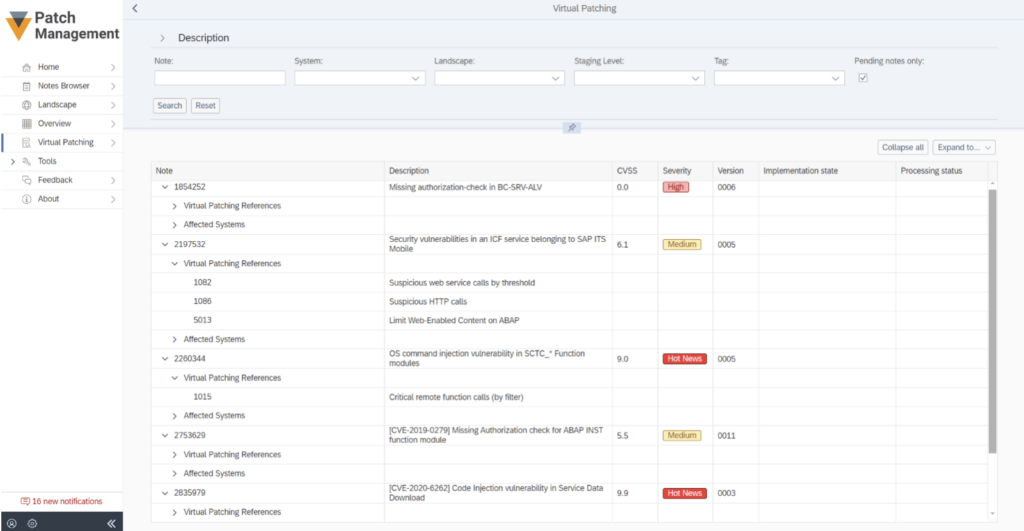
In the beginning, SAP Security teams need a good and detailed overview that highlights:
The SAP Security Notes, sorted by severity
SAP landscape impact for each patch with a focus on the most critical ones
All relevant patches that are missing per SAP system
Implementation process status (incl. prerequisites) for each SAP Security Note per SAP system
The SecurityBridge Platform provides all these views as an interactive user experience, allowing users to prioritize their Patch Management activities and accomplish them with the least effort. Following the principle of a guided approach, SecurityBridge helps customers by providing recommendations for implementing and testing each SAP patch.
These recommendations are based on expert knowledge, an automated impact assessment, and feedback from our community. Also see SAP Security Research for insights into emerging threats.
Streamlining the implementation of patches through process integrations also helps save time. Therefore, SecurityBridge integrates with the SAP SolutionManager and keeps both processing queues in sync.
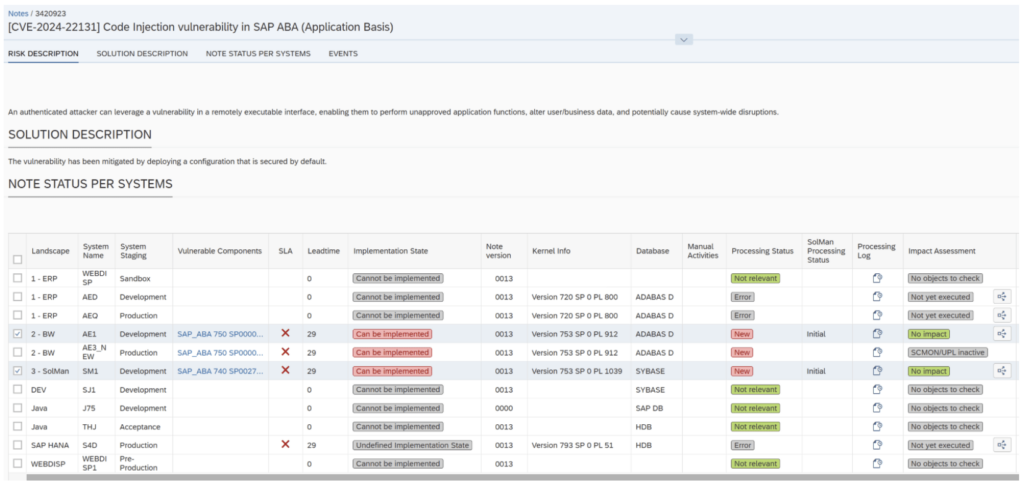
In addition, automating the implementation of SAP Security Notes wherever possible is key for further reducing the time window during which SAP systems are at risk and for increasing the efficiency of the Patch Management process. However, SAP Security experts know how complex and heterogeneous SAP patching is. This makes automation very challenging. The Patch Management in the SecurityBridge Platform provides an automated implementation for the majority of SAP Security Notes (up to 75%). The implementation can be performed either attended (in the foreground) or unattended (in the background). Only those patches that have no manual steps or prerequisite notes and can be safely deployed in the target system are released for this automated procedure. SecurityBridge performs a special internal patch assessment to ensure a safe deployment for the specific patch.
How to reduce SAP Patch Management effort from days to hours?
Patch Management is a critical aspect of maintaining the security and functionality of SAP systems. However, the process is fraught with challenges, particularly because the monthly SAP Patch Day sets the pace. The time-consuming nature of patching SAP systems, coupled with the complexity of these environments, makes it hard for SAP Security teams to get at least the most necessary patches implemented within a month.
SecurityBridge customers benefit from the automated update of SAP Security Notes, monitoring templates, and vulnerability checks. These features put them in pole position in the race against potential exploits. They can immediately leverage the latest threat intelligence after SAP releases the Security Notes, and even before the release if the findings come from the SecurityBridge Research Lab.
By connecting information from SAP Security Notes with security signatures, SecurityBridge allows compensating controls to be applied until the actual patches are implemented. This Virtual Patching provides SAP Security teams with crucial extra time and flexibility by detecting zero-day exploits. It acts as a “vulnerability shield” during the patch implementation process that helps to reduce the risk period.
Streamlining and automating the Patch Management process is essential for efficiency. The interactive user experience of the SecurityBridge Platform helps prioritize and implement SAP patches with minimal effort. Automated implementation of SAP Security Notes, where possible, further reduces the risk window and enhances efficiency. By integrating with the SAP SolutionManager, SecurityBridge keeps processing queues synchronized, saving time through seamless process integration.
Interested in learning how we can help you adopt a mature SAP Patch Management and other best practices for further hardening your SAP landscape? Contact us and we will be happy to tell you more about our guided approach to SAP Security excellence. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!


