
Finding and exploiting CVE-2024-21737

Chapters
Share Article
SecurityBridge believes that engaging in SAP Security research and uncovering weaknesses in SAP systems contributes to making the SAP ecosystem more secure. Not just for our customers who benefit directly, but for all SAP customers worldwide who rely on these business-critical systems. To better understand the risk and impact of an SAP vulnerability, it helps to demonstrate the practical details. This article describes the finding and exploiting of SAP vulnerability CVE-2024-21737, including a solution to resolve it.
Our research into SAP vulnerabilities has previously led to numerous findings. We reported these findings to the SAP Security Response team, which led to fixes that are typically released on Patch Tuesday. In the January 2024 Patch Tuesday release, SAP Security note 3411869 (Function Module /AIF/BRAN_DIR_CREATE OS) was published, reflecting a direct outcome of SecurityBridge’s research activities. We found that the Function Module /AIF/BRAN_DIR_CREATE OS was vulnerable to a security bypass via Operating System command injection.
These types of vulnerabilities are often ranked high on the Common Vulnerability Scoring System (CVSS), with this case receiving a score of 8.4 out of 10. This is a serious vulnerability that necessitates a quick implementation of the SAP Security note within vulnerable customer systems.
How we found it
Our research activities to identify vulnerabilities employ various techniques and methods. One approach involves reviewing the SAP standard code base for vulnerabilities, such as missing authorisation checks or missing input validation around dangerous statements. To enhance efficiency, we utilize tools that automatically index the complete ABAP code base of a specific SAP system, enabling faster and easier searches afterwards. By doing so, we focussed on the code base of SAP ERP and searched for the statement “CALL SYSTEM”. This is a powerful kernel call that allows the execution of Operating System (OS) commands through the SAP Kernel triggered from ABAP code. This command, when not properly protected by authorizations and input validation, might be prone to OS command injection. Thus, a user can execute any OS command directly on the SAP Operating System.
In our review of the ABAP code base for SAP ERP, we found that the Function Module /AIF/BRAN_DIR_CREATE OS contained the “CALL SYSTEM” statement. It seemed that input validation was in place as of 2012, through a regex statement designed to prevent the use of special characters to break out of the context, as shown below:
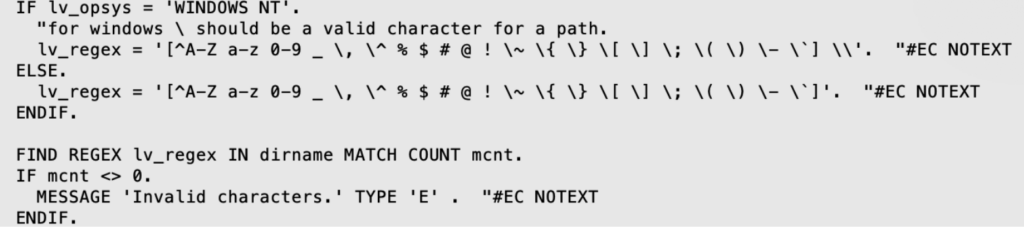
However, this mechanism was not working properly because the lv_regex field, which contains the allowed characters, includes the “;” sign. This sign can act as a shell command separator under some Operating Systems, like Linux, allowing additional commands.
The below code snippet depicts the actual place where the system call is made:
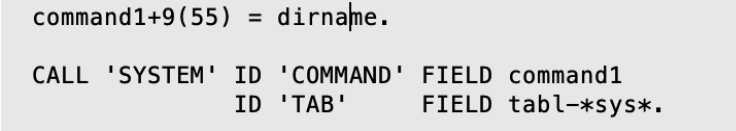
The command1 parameter which contains input coming from the User-Interface can be used to inject your custom OS commands.
How to abuse or exploit it
To exploit this vulnerability, we use the test button in transaction SE37 (a minimum requirement to start and use transaction SE37). To be able to inject your custom commands, for example, you can use the input: “abc ; mkdir YYY”.
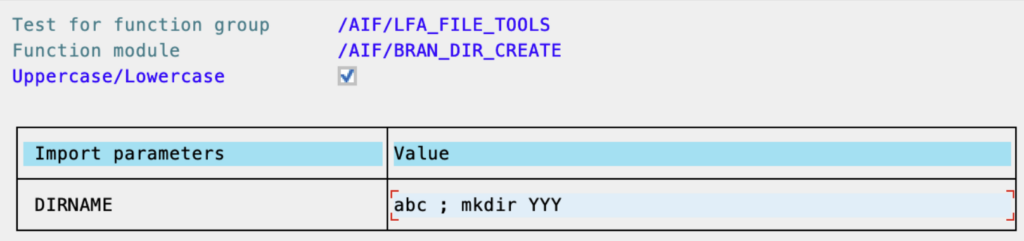
This creates the directory ‘YYY’ on the Operating System. Although this directory creation is not desirable, it is not inherently a disruptive or security-relevant action. However, this situation changes when you pass the following two lines to the report in two runs as shown below:
ABC; echo ‘SELECT * from USR02’ > script.sql
ABC; hdbsql -n vhcalhdbdb -i 00 -U DEFAULT -o output.txt -I script.sql
The two lines above create a file ‘script.sql’ that contains the text, ‘SELECT * from USR02’. This gets executed specifically in the second line for HANA Databases, and the output is written to a new file ‘output.txt’, containing all table entries of the USR02 table in this case. By modifying the above statement, you are virtually able to get data from any table. Other possible scenarios include the creation of SAP users, modification of data in the SAP system, extraction of sensitive data, breaking out of this system and moving towards other SAP systems, disruptive scenarios like wiping all data in the system, encrypting it for ransomware purposes, and more.
How to fix this?
Import the SAP Security 3411869 via transaction SNOTE. This will remove the CALL SYSTEM statement completely.
Implementing the above security patch is important, but it should be incorporated into a wider process encompassing Vulnerability Management and Patch Management. Since SAP releases patches monthly and the number of released fixes can be huge, it is important to have insight into your missing SAP Security notes. SecurityBridge can provide this insight and assist with automating the implementation of patches. For more information or to request a demo, please contact us or follow us on LinkedIn!

