How to detect script-based attacks against SAP?

Chapters
Share Article
In recent years, cyberattacks against SAP systems have become more common, with attackers gaining network access and then exploring critical applications through port scanning and script-based exploration. Two examples of such attacks that use the SAP RFC SDK are the password lock attack and the password spray attack. In this article, we will outline how to detect these script-based attacks against SAP.
Example 1: Password Lock Attack
The password lock attack targets SAP user accounts by creating multiple failed login attempts to lock them out of the system. This attack aims to disrupt business operations by preventing legitimate users from accessing the system. The attack uses the SAP RFC SDK, which allows the attacker to automate the login process and repeatedly enter incorrect passwords until the account is locked.
To detect a password lock attack, you should monitor the failed login attempts on your SAP system. SAP keeps track of the number of failed login attempts for each user, and if the number of failed attempts exceeds a certain threshold, the account is locked. You should set up alerts when a user account gets locked due to failed login attempts. You should also monitor the logs for any unusual login activity, such as many login attempts from a single IP address.
Example 2: Password Spray Attack
The password spray attack is another script-based attack that targets SAP user accounts. In this attack, the attacker tries to guess user passwords or weak initial passwords set by the admin. The attack uses the SAP RFC SDK, which allows the attacker to automate the login process and repeatedly try different passwords until achieving a successful login.
To detect a password spray attack, you should monitor the login activity on your SAP system. Look for patterns of failed login attempts from a single IP address, which may indicate that an attacker is trying to guess passwords. You should also monitor the logs for any unusual login activity, such as multiple login attempts from a single IP address.
Are SAP Interfaces especially vulnerable?
Every SAP Basis admin knows that SAP S/4HANA and SAP NetWeaver provide the profile parameter login/fails_to_user_lock, to allow setting the threshold after how many failed login attempts the account will be locked. This parameter is usually set to “5”, which is also the default configuration following the system installation. It happens to every user during their daily jobs that one key in the wrong password. Each time this appears, the system increases a failed login counter which is then reset at the next successful account login.
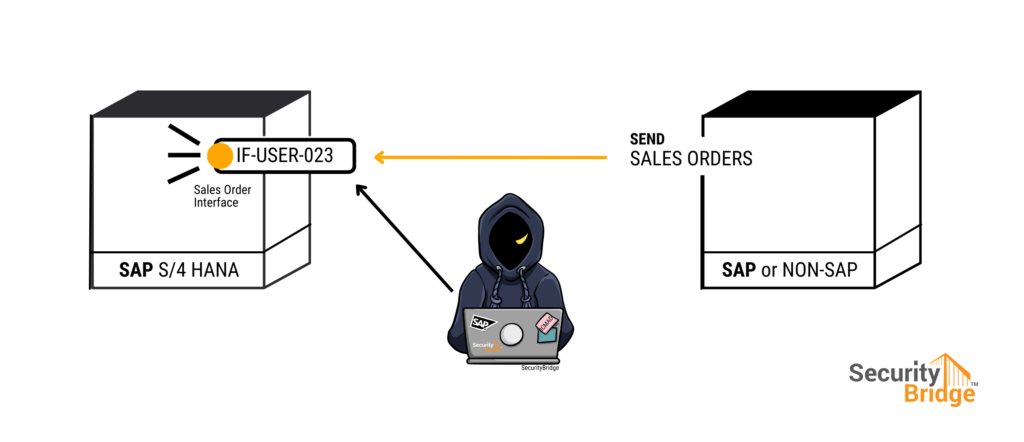
Interface users, however, are used to communicate between SAP systems and other applications. In addition to automated processes, such as sales orders or PO confirmations, these users are also used to send and receive data between systems. These users are particularly vulnerable to script-based attacks because their failed login attempt counter starts with every successful login.
If you want to detect script-based attacks against interface users, you should closely monitor the failed login attempts for these users in the SAP Security Audit Log. You should detect statistical anomalies and receive an alert that notifies you when there have been many failed login attempts for a specific technical user. You should also monitor the logs for any unusual login activity, such as many login attempts from a single IP address.
Conclusion
More sophisticated attack scenarios exist using scripts to enable the threat actor to attack a wide range of assets (i.e., SAP accounts). Our team has detected Script-based attacks against SAP systems in the wild, and it is essential to identify them early to prevent damage to your business operations. By monitoring failed login attempts and login activity on your SAP system, you can detect password lock, password spray attacks, and attacks against interface users. For this article, we have purposefully chosen simple examples that are easy to identify. Many more attack scenarios exist that are more complicated and dangerous, particularly when the SAP system has unpatched vulnerabilities. It is, therefore, crucial to keep your SAP system up to date with the latest security patches and to implement transparent security monitoring, building the foundation to detect and prevent cyber-attacks.
If you need any help with this, we are always available to help you save your business-critical information. Want to contact us? You can contact us here: https://securitybridge.com/contact/