
Chapters
Share Article
The Business Technology Platform is the further development of the former SAP Cloud Platform. Behind the abbreviation, BTP hides the meaningful term Business Technology Platform. On the product page SAP advertises the following: SAP BTP combines data management, analytics, artificial intelligence, application development, automation, and integration in a unified environment.
The new SAP technology allows a lot of flexibility and offers a well-structured BTP audit log in the security domain. As an SAP security solution provider, we took a closer look at it and integrated the BTP audit log into our monitoring portfolio.
What is SAP BTP?
The SAP Business Technology Platform (SAP BTP) is a cloud platform on which companies can use numerous services and functions – both existing services from SAP and other providers, as well as custom developments. Divided into four principal areas: Database and Data Management, Analytics, Application Development, and Integration and Intelligence Tech, it advertises maximum flexibility and easy integration into the existing SAP product portfolio.
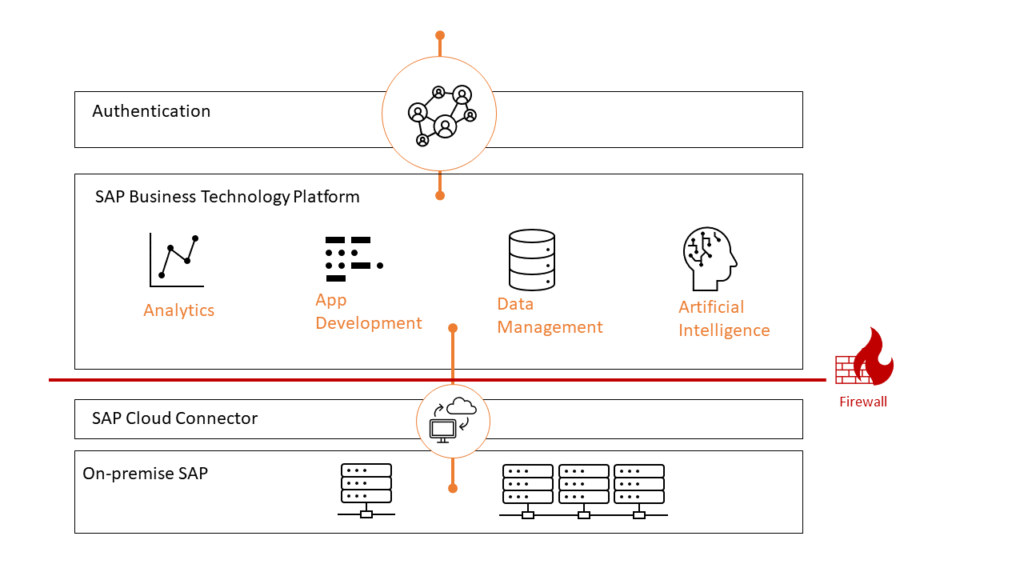
You should start with the concept of “environments” to delve a little deeper into the SAP Business Technology Platform. Environments form the actual Platform-as-a-Service offering of SAP BTP, enabling the development and management of business applications. Environments are anchored in SAP BTP at the subaccount level. The Cloud Foundry, ABAP, Kyma, and the Neo Environments exist. Follow this link to find more details on the subject in the SAP Help Portal.
What is the SAP BTP Audit Log?
Audit logs are a special type of logs. They represent security-relevant chronological records that provide documentary evidence for an event or activity that delivers information about e.g., User login to SAP BTP. The SAP BTP Audit Log Service stores audit logs representing different actions taken over your account and (or) data. There are predefined audit categories for data protection & privacy next to security-relevant events. All entries of the SAP BTP Audit log are grouped into the following areas:
- Identity provider management
- Instance management
- Role collection management
- Role management
- SAML authentication
Further information can be found in Audit Logging in the Cloud Foundry Environment
SAP BTP Audit Log Viewer service
The SAP Audit Log service is a platform service that stores all the audit logs written on your behalf by other platform services that you use. It allows you to retrieve the audit logs for your subaccount via the audit log retrieval API or view them using the SAP Audit Log Viewer Service.
Challenges
The SecurityBridge Platform makes it easy for SAP customers to keep track of security-related activities with its threat detection capabilities. Especially with the new SAP BTP Audit Log, customers are confronted with an entirely new challenge. A new message format and new categorization are waiting, bringing new use cases. Customers now need to think about which of these security use cases needs to be incorporated into active monitoring (e.g., SAP SOC/SIEM). In addition to this practical obstacle, there are several technical questions to be answered:
- How can the data be accessed?
- What needs to be decoded? How can the new format be brought into a uniform message structure?
- What are the error cases? What must be done if the log is no longer readable?
- Which SAP BTP tenants exist in the company at all?
When you read the last point, you may be crying out mentally, but actually, the tenants’ determination creates a challenge for many enterprises. As with many cloud solutions, it is easy to apply for a new tenant with SAP BTP. If there is an active connection to the on-premises SAP application, this is traceable. However, if the SAP BTP tenant exists on its own, things get a bit more complicated.
Where can I find SAP BTP Audit Log information sources?
In conclusion, we would like to point out a few informative references that played a role in the context of this article. Perhaps one or more readers will find the links helpful. If you do not want to miss any helpful posts and want to stay up to date with SAP Cybersecurity, follow our LinkedIn page.


