SAP Clickjacking Vulnerability: Understanding the Risk and Protecting Your System

Chapters
Share Article
As one of the largest enterprise software companies worldwide, SAP delivers multiple solutions that help businesses manage their operations, finances, and customer relationships. However, just like most software vendors, SAP is also vulnerable to security risks that can compromise the integrity and confidentiality of your data.
One such risk is SAP clickjacking, an attack that allows an attacker to hijack a user’s click and execute malicious actions without their knowledge. During SAP Security Patch Days, the SAP Response Team regularly issues SAP Notes that address Clickjacking vulnerabilities in the SAP standard web applications.
What is Clickjacking?
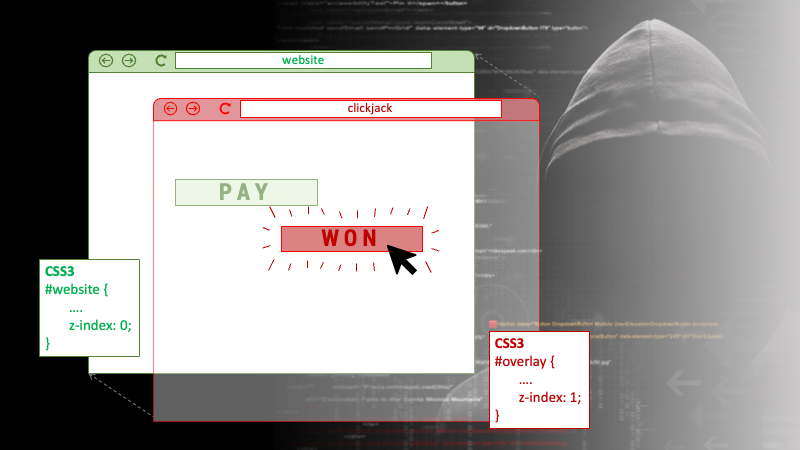
Clickjacking, also known as UI redressing, is a malicious technique used to deceive users into clicking on a button or link that performs an unintended action. The attackers use a method of superimposing an invisible or translucent layer over a legitimate web page or application, which creates an illusion of the user interacting with the authentic interface. The layer can be placed using HTML, CSS, or JavaScript, and it can perform a range of malicious actions, such as stealing user credentials, initiating a fraudulent transaction, or downloading malware onto the user’s device.
What is the SAP Clickjacking Vulnerability?
Unless successfully prevented, SAP is impacted by Clickjacking Vulnerability, particularly in the SAP NetWeaver Application Server Java, Enterprise Portal (EP). The vulnerability stems from inadequate protection measures, such as the absence of whitelisting or an appropriate Content Security Policy (CSP).
If an application is susceptible to clickjacking, an attacker may execute the clickjacking attacks against users of the platform. A clickjacking attack in the SAP framework could make it possible for an attacker to inject malicious code into SAP applications and hijack user clicks. Once an attacker has gained control of a user’s click, they can execute a range of actions, such as transferring funds, changing user settings, or stealing sensitive data.
Find more information on OWASP.org.
What is the Impact of the SAP Clickjacking Vulnerability?
The impact of the SAP Clickjacking Vulnerability can be severe, as it can allow an attacker to gain unauthorized access to sensitive business data and execute fraudulent actions. This can result in financial losses, reputational damage, and legal liabilities for affected organizations. Additionally, successful exploitation is often used to launch further attacks against the SAP system, such as installing malware or initiating a denial-of-service attack.
How Can You Protect Your System from the SAP Clickjacking Vulnerability?
To protect your SAP system from Clickjacking Vulnerability, it is essential to implement the following security measures:
- Keep Your SAP System Updated: Ensure that your SAP system is always up-to-date with the latest security patches and updates. This will help to mitigate any known vulnerabilities in the platform, including Clickjacking.
- Implement Clickjacking Protection: Implement clickjacking protection measures in your SAP applications to prevent attackers from injecting malicious code and hijacking user clicks. You can achieve this by using the X-Frame-Options header, Content Security Policy (CSP), or Frame Busting techniques. SAP also provides an additional help page on the use of SAP’s Clickjacking Protection Framework.
- Conduct Regular Security Audits: Conduct regular security audits of your SAP system to identify and mitigate any potential vulnerabilities. This can include penetration testing, vulnerability scanning, and code reviews.
- Train Your Users: Educate your users on the risks of clickjacking and other security threats, and encourage them to adopt safe browsing habits, such as not clicking on suspicious links or buttons.
Conclusion
The SAP Clickjacking Vulnerability is a serious security threat that can compromise the integrity and confidentiality of your business data. However, you can protect your SAP system from harm and reduce the risk of a clickjacking attack by implementing the appropriate security measures. Those can be: keeping your system updated, implementing clickjacking protection, conducting regular security audits, and training your users.
We know it well: when it comes to cybersecurity, prevention is always better than cure. We therefore warmly suggest you take immediate action, in order to safeguard your business from this and other potential threats.