
SAP Security Baseline 2.5 – Key Points

Chapters
Share Article
On April 8, 2024, SAP released version 2.5 of the SAP Security baseline. In this article, we will delve into the updates and share some key findings.
IT landscapes change rapidly, driven by key events like cloud migration and adaptation to new technologies. Security demands and insights must align with this reality and be therefore equally dynamic. At SecurityBridge, we are well aware of this necessity and follow security developments closely. With our security solution, SAP system landscapes can be validated against several baselines using the Security & Compliance module. The SAP Security baseline is a well-known template within the SAP security community, and we therefore offer this baseline within our solution as well, together with our own – more extensive – SecurityBridge baseline. More about that at the end of the article.
The previous version of the SAP Security baseline already dates to December 2022 (not counting textual updates), so an update was certainly in order. Let’s dive in!
Main changes
According to SAPs own changelog, the baseline is mainly updated with:
(a) new requirements about trusting relations between systems and
(b) new secure default settings in S/4HANA 2023 and BW/4HANA 2023.
But going through these updates, there have been more changes across several security areas. We will check out these below, following the order of the baseline and skipping the very minor adjustments. One note upfront: some changes that are presented as ‘changes’ for version 2.5 of the baseline were already part of the minor update of version 2.4.1.
Information disclosure – HANA
Data should be protected by enabling encryption for data volumes, logs and backups. Further, the corresponding encryption keys must be stored externally in case of a recovery situation.
Information disclosure – Web Dispatcher
Requirements have been adjusted for particular kernel versions (> kernel 7.81) and filtering of certain URL paths /sap/public/icman/* and /sap/public/icf_info/*.
Directory Traversal Protection – ABAP
Requirements for secure file handling from the ABAP stack have been updated by:
- Profile parameter: abap/path_norm_Windows.
- Parameter settings for transaction SFILE: REJECT_EMPTY_PATH and REJECT_EMPTY_PATH
Message Server Security – ABAP and JAVA
General access to the message server should be restricted by making proper use of an Access Control List (ACL). This recommendation has been updated.
No Testing Functionality in Production – ABAP
Requirements have been added for testing authorizations in productions for functions S_DEVELOP FUGR and S_DEVELOP CLASS. As well as deactivation of testing services.
User Control of Action – ABAP
Some minor adjustments for parameter settings have been made.
User types and allowed character sets for usernames
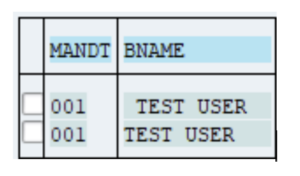
Requirements have been added to make proper distinction in user type for personal and technical users in general. For ABAP systems, restrictions have been added on characters that can be used to create usernames. This prevents usernames that appear the same but are actually different or create confusion. For example: without proper settings, it is possible separate users as shown below (notice the ‘white spaces’ in front and in between the username):
Password Policy – HANA
The requirements for password policy have been enhanced with the following parameters to enforce a tighter security policy:
- maximum_invalid_connect_attempts (Number of Allowed Failed Logon Attempts).
- password_lock_for_system_user (Exempt SYSTEM User from Locking)
- password_lock_time (User Lock Time)
- minimum_password_lifetime (Minimum Password Lifetime)
- password_expire_warning_time (Notification of Password Expiration)
Trusting relations and trusted destinations – ABAP
As stated in the baseline’s changelog, the requirements for trusting and trusted destinations have been added to only configure trusted relations. In summary, the controls entail:
- Removal of any trusting/trusted relationships.
- Migration of old relationships to new security methods.
- Usage of SNC or TLS.
- Control of authorizations with objects S_RFCACL, S_RFC_ADM_TT and S_ICF.
- Configuration of parameters rfc/selftrust and rfc/allowoldticket4tt.
Authorizations for ABAP
Requirements have been added or enhanced for ABAP authorizations:
- Authorization objects S_DBG, S_USER_GRP, S_TABU_DIS.
- Customizing settings on US_ASGM_TRANSPORT and USER_REL_IMPORT
Audit settings – HANA
Requirement has been added to define audit policies according to the SAP best practices.
Secure default settings in S/4 HANA 2023 and BW/4HANA 2023
The new default settings for these products are mentioned. These partly concern settings that are mentioned above (Restricted character sets for usernames, customizing settings US_ASGM_TRANSPORT and USER_REL_IMPORT and parameter settings for rfc/allowoldticket4tt and HANA encryption).
Conclusion – let’s raise the bar and beyond!
Any update or improvement in SAP security standards deserves to be welcomed by the SAP Security community and the same goes for this version 2.5 of the SAP Security Baseline. The update on trusted ABAP connections indeed stands out as one of the main and valuable updates. Other updates are also valuable, of course. But some are frankly quite basic or consider topics that have already been around for many years.
This brings us to a more general observation of the SAP Security Baseline. One that is acknowledged in the baseline’s introduction. The SAP Security Baseline, without debate, should be applied as the minimum set of security measures in your SAP systems. However, we believe security can and should be taken a step further. Using our Security & Compliance module, we enable the use of the SAP Security baseline, but also our own SecurityBridge baseline which covers a larger number of areas and with a lot more controls, in an automated way.
In short: SAP Security Baseline 2.5 can certainly help to bring your security posture to a higher level than relying on insecure defaults. While it is good to see the baseline updated to 2.5, if you want to raise the bar and get your security straight, feel free to contact us for a demo or try out SecurityBridge yourself.

