
Strengthening SAP Security with Access Control Lists (ACL)

Chapters
Share Article
In today’s interconnected digital landscape, where data breaches and cyber threats are on the rise, ensuring robust technical security measures is paramount for organizations. With the increasing complexity of IT systems, safeguarding sensitive data and maintaining regulatory compliance has become more challenging than ever. This is where Access Control Lists (ACLs) can play a vital role in bolstering technical SAP security. In this blog, we will explore the significance of SAP ACLs, understand their importance in mitigating security risks, and compare them with network security measures like firewalls.
Why SAP application security is necessary
Organizations face the ongoing challenge of securing their valuable assets, such as financial data, intellectual property, and customer information, stored in SAP systems. Unauthorized access to these assets can lead to severe consequences, including financial loss, reputational damage, and legal ramifications. Traditional security measures, such as firewalls, can effectively protect the network perimeter, but they often fall short in securing internal systems and data repositories, like SAP systems.
Why? We name two main reasons:
- There are multiple threats / exploits that simply cannot be stopped at the network level alone but require application-specific settings.
- Complex architecture and several components in an SAP system require network connectivity.
To elaborate on this last point, SAP systems have a multi-layer architecture; their components are highly scalable and can be distributed among several hardware resources to facilitate even the highest landscape requirements. This offers excellent flexibility but comes with the price of significant complexity as well! The number of components involved in connectivity is vast, and even with relatively small SAP landscapes, oversight is easily lost. Let’s take a typical SAP ABAP system as an example. From a technical connectivity standpoint, there is connectivity from user interaction, coming from browsers, apps, and (the everlasting) SAP GUI. There is system integration for interfacing and other technical components like LDAP, file shares, email connectivity, monitoring agents, databases, etc. That is all aside from the elements of the SAP system that need various connections to operate, whose complexity significantly increases for more significant landscapes and higher available setups. Look at this overview of TCP/IP ports for SAP products; managing and controlling connectivity in an SAP landscape is no small feat…
So, can this all be managed securely by relying on network components alone? Is a firewall enough? The answer is simple: no, it is not. Firewalls primarily focus on traffic filtering, packet inspection, and network segmentation. These are essential security features, no doubt about that. However, they do not offer the granular form of application security that is required nowadays. In fact, without additional application security, SAP systems are highly vulnerable to known exploits, which can come from external as well as internal sources.
“Is network security enough to protect SAP systems? No, it is not!”
ACLs as a crucial addition
As said, advanced application security is paramount to safeguarding SAP systems. In this blog, we only look at technical connectivity and want to point out the added value that Access Control Lists have for SAP security. It is a great addition to network measures like firewalls and different network zones because it allows for a more granular distinction that can be controlled from the SAP application level. SAP is offering ACL functionality for multiple components, like the following:
- Message server: central component used in SAP ABAP and Java stacks.
- Internet Communication Manager (ICM): mainly used for HTTP(S) and SMTP protocols (but there is a lot more). Note that the Web Dispatcher can be set up similarly.
- RFC gateway: for RFC communication between SAP systems and external programs.
The above list is incomplete, and each named component has its specifics for the configuration of an ACL which would deserve a separate blog. In principle, though, an ACL is a rule set that either ‘permits’ or ‘denies’ a certain type of connection related to the component. Like the example of a message server ACL (see link below).
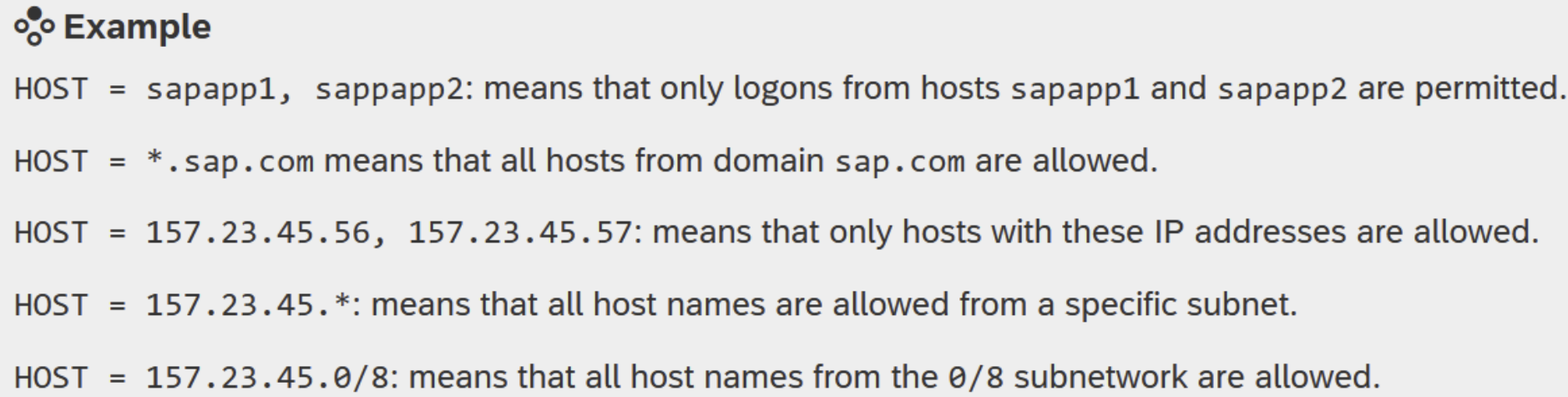
The example entries above define which hosts are allowed to log on to the message server component as an SAP application server. Without a ruleset like this, any host that can reach the message server can try to register itself and exploit known vulnerabilities to the SAP system via this route.
Guidelines for implementation
Interestingly, the option to use ACLs often already exists for years but is often not used at all or inadequately to offer real protection. There can be various reasons for this, like time shortage, lack of insight into the landscape architecture or misguided notion of network security. Whatever the reason, implementing an effective ACL needs to be done properly to prevent disruptions and offer real security at the same time. Therefore, see below some guidelines for implementation:
- Insight in landscape architecture is paramount to identify related systems/components upfront.
- Use additional logging/tracing to identify missing (or already malicious!) connections.
- Implement ACLs at non-production systems first (best practice).
- Allow considerable time, like weeks or months, for steps 2 and 3. This includes connectivity that is not often used but may be critical. Also think about connections needed for month or year-end closures, for example.
SecurityBridge has it covered!
The SecurityBridge platform offers various controls that check for the ACL configuration of several components. The platform also provides a holistic view of the Web dispatcher, ICM Security, and RFC Gateway security status of the SAP systems in one place and recommends improvements that may be required to secure the SAP systems further. This centralized view is a valuable insight so that these can be configured consistently across the landscape.
See below references to the SAP Help pages as a starting point for the mentioned components:
Message server: SAP Help link
ICM: SAP Help link
RFC gateway: SAP Help link
Conclusion
Organizations must adopt a multi-layered approach to safeguarding their valuable SAP systems in today’s interconnected world. While network security measures like firewalls protect the network perimeter, SAP offers an additional layer of security using ACLs that can be crucial in securing internal systems and data repositories. Organizations can enhance data protection, mitigate risks, and maintain accountability by implementing SAP ACLs. As technology evolves, organizations must prioritize comprehensive security measures like SAP ACLs to ensure their critical business information’s confidentiality, integrity, and availability.
Try SecurityBridge and immediately improve the security of your SAP systems! For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!

