
Who are the typical SAP attackers?

Chapters
Share Article
We are asked many times and have already addressed this in our open webinars, which SAP attackers exist? With this blog, we would like to share some insight and answer this question. However, first, we should look into some examples of publicly known SAP attacks:
Greek finance ministry
One of the first known cyberattacks on SAP systems occurred on October 2012, almost ten years ago. The hacker group Anonymous allegedly leaked confidential files and credentials of the Greek Finance Ministry.
It is not 100% clear from the published information how they infiltrated the SAP systems. Reports confirmed that the data source was SAP, showing the hackers’ interest in SAP.
NVIDIA
On January 2014, NVIDIA’s customer service website was under attack. NVIDIA had not implemented a patch that was released three years earlier. This caused the customer service website to be taken offline for two weeks. The attack did not result in a data breach, but the downtime of the Customer Care Portal led to a reputation loss for NVIDIA.
USIS (US Investigation Services)
The news announced on May 11, 2015, a breach by Chinese hackers made possible through a vulnerability in SAP software. An internal USIS investigation revealed that cyber intruders got into the company through a software glitch from tech firm SAP used to run certain back-office operations, such as human resources.
The internet is full of reports of companies that have suffered data theft or outages due to cyber incidents. It is not always clear whether and to which extent SAP systems were affected. However, it is worth noting that SAP systems contain personal data like credit cards, payment information, and much more, making them a target for SAP attackers. When SAP customers are targeted by an attack, it is safe to assume that the leaked data originates from SAP applications.
With this in mind, let’s get into some relevant questions:
Who are SAP Cyber Attackers?
Cyber Attackers are portrayed as malicious programmers who try to gain access to your core system. However, knowing the architecture of SAP systems, this definition is too narrow. Cyber attackers not only use the network (the internet), but also employ methods like social engineering, extortion, and bribery. These attackers use various tools, also known as Tactics, Techniques, and Procedures (TTP), to infiltrate the SAP environment of the targeted organization unnoticed.
5 Types of SAP Cyber Attackers
SAP Cyber attackers present themselves in different forms based on their motivation and methodology of attack. We previously examined the topic and broadly classified the following types:
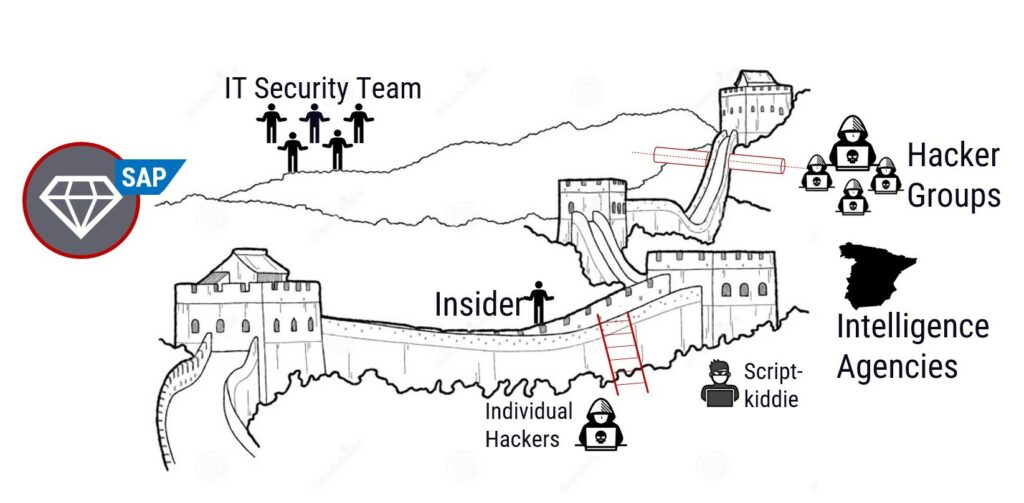
1. Script kiddies – SAP Cyber Attackers
After the pandemic relegated many employees to work from home, this category found a large influx.
Script kiddies are amateurs who learn from the internet and use available tools to crack a system. These beginners are harmless with fewer skills and do not cause heavy damage to the SAP system, especially since SAP is a complex environment without many detailed help pages available. The entry hurdle for Script kiddies is high, although we see more and more published ready-to-use SAP exploits. Script kiddies enjoy being challenged and seek the thrill from it. Over time they may gain experience and even become professional hackers.
2. Cybercriminals – SAP Cyber Attackers
These attackers are individuals or a group of individuals aiming to exploit the victim’s sensitive information. Usually, they hijack the SAP system to gain access to data that they can turn into money.
3. Hacktivists – SAP Cyber Attackers
Remember the SAP hack of the Greek finance ministry? Hacktivists are those who perform malicious and fraudulent tasks to further a political agenda. Hacktivism is digital disobedience undertaken for a cause. These activists fight for justice and are not out for financial gain. They even team up with malicious insiders at times to expose sensitive data.
Organized crime has, unfortunately, also figured out that there is a lot of money to be made from cyber-attacks. Therefore, individual hackers are increasingly organizing themselves into professional structures that can resemble a company in terms of their structures, hierarchy, and shared responsibility.
4. Nation-State Hacker – SAP Cyber Attackers
This attacker works for, or on behalf of, a government to infiltrate key companies that operate critical infrastructure for society, such as power grids. Their objective is to steal sensitive information, damage adversary facilities, or cause an international incident. They use sophisticated attack techniques against their opponents and try to destroy all evidence. Some of these attackers are patriots and work to put the nation in a better position by inflicting high-level damage on their adversaries.nal structures that can resemble a company in terms of their structures, hierarchy, and shared responsibility.
5. Insider – SAP Cyber Attackers
Most often, especially for SAP attacks, it is the insider attacks that cause damage to the companies. Here one must make distinctions that differentiate between the malicious insider attack, the unintentional insider attack, and the negligible insider attack.
Malicious attacks are the most dangerous and are often difficult to detect. They come out of the blue without notice and may exploit vulnerabilities like the SAP Transport Supply Chain issue. External and internal employees are bribed or threatened to perform activities harmful to their employer. But even if the employees disagree with the employer’s actions for political reasons, a malicious attack can occur.
Summary
SAP Cyber Attackers have many motivations and come from all social classes. Some just want to have fun or cause damage, while others want to make a quick buck. Of course, the SAP cyber attackers who pursue a strategic goal, such as espionage, are particularly dangerous. The idea that SAP cyber attackers sit in a dark room in front of many screens, preferably with a black hoodie, does not correspond to reality. Companies must face that attacks could happen at any time and come from any direction. Therefore, defining an individual risk profile and identifying the attack surface to take efficient countermeasures.
