
SAP Data Security 101: Importance of data security

Chapters
Share Article
This article is about data security and data protection, specifically for digital data collected and processed via SAP applications. SAP Data Security is important because plenty of business-critical information gets processed with the SAP ERP, CRM, and SRM applications. The SAP Human Capital Management (HCM) manages employee matters from payroll to employment contracts. All this information is processed digitally and needs protection against unauthorized access, manipulation, or deletion.
With more companies moving from a reactive cybersecurity approach for SAP to building cyber-resilience, it is crucial to address the area of data protection for SAP.
What are the SAP Data Assets worth protecting?
Start with the classification
Firstly, we need to explain what data is worth protecting, and after that, we will look at what strategies and protection options exist. We cannot conclusively tell you what data assets are worth protecting.
Therefore, you should talk with the data protection officers from your company to develop a data classification strategy. It is worth noting here that simple concepts usually work best.
Here is an example: You could start with the idea of throwing your data into three pots. On the first one, you write Public, the second one you label Confidential, and the last one stands for Secret. You can work with these three simple data classifications.
Define classification criteria
Before we define how you can classify SAP data, we must determine which criteria must be met to put the data into one of the three pots.
Public: Data that may be publicly accessible without risk of damage (financial or reputational) to the company. Also, this data should not give any advantage to your competitor, and you must ensure that there are no legal regulations that require protection.
Confidential: To this category, you should add data that should not become public. You can divide the Confidential section into many subsections depending on the severity or risk of an SAP data breach. Depending on the company’s interpretation, confidential data can be characterized by the fact that internal access is not critical, but no outsider may access the data.
Secret: All types of trade secrets fall within this scope. This data must be protected from internal and external access and is subject to the need-to-know principle.
Start assigning SAP data assets
With this simple and incomplete definition of classes, you can start classifying the data objects stored in the SAP database. This is a mammoth task that many IT departments fail at or are happy to outsource to the business departments and their consultants. We recommend that you take on these tasks and bring all departments from Human Resources to Accounts Payable and Sales on board. You should also define a process that ensures that newly collected data objects are directly classified and that you can establish a corresponding protection standard. Learn more about how SecurityBridge helps centralize SAP Data Classification and Monitoring.
What protective measures should you take to achieve SAP Data Security?
Now that you know what data you need to protect, you can define the measures. In general, authorization management is available in every SAP application. Since there is already a lot of literature on this function, we turn to more advanced methods. Here are a few examples to give you a helpful hint on how you can increase the protection beyond the pure SAP authorization handling.
Delete data assets not needed
Disconnect from data you no longer need. Define a Data Lifecycle Management (DLM) for SAP, which regulates how long data is current and valuable for your company. Usually, a DLM/ILM (Information Lifecycle Management) is used to reduce the database size. However, the introduction of GDPR has also regulated the deletion of specific data.
Know your data flow
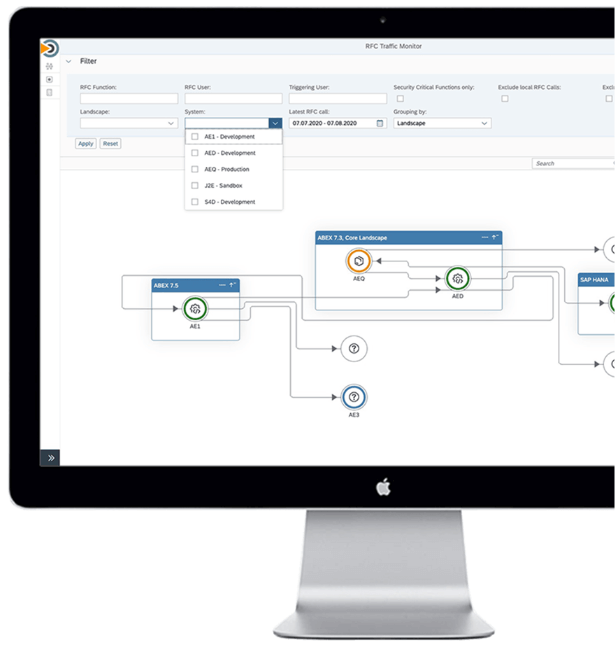
A lot of data breaches occur because single employees or batch processes (i.e., interfaces) exported relevant data from the SAP database.
Threat actors gain access due to insecure communication channels or when the selected storage location does not have sufficient protection.
What path does your data take through your IT landscape and SAP system? Do you have some leftovers here and there, maybe when you store files on the SAP application server?
SecurityBridge’s Interface Traffic Monitor helps you analyze the data flows carried out in the SAP context to a large extent as “remote function calls” and displays them on a graphical map.
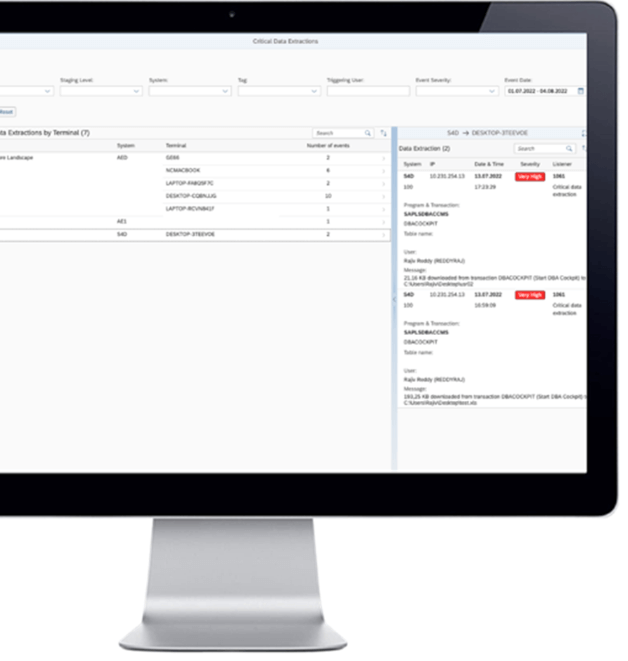
You quickly reach the limits of the SAP authorization concept when you realize that the accounting department regularly extracts the entire customer base and the price conditions into an Excel spreadsheet to present them to the managing director. Not only does the resulting Excel file elude your protection measures, but it is also difficult for you to distinguish whether the data download was legitimate. At the same time, you should also start paying attention to protecting data that supports system integrity. For example, you must prevent threat actors from accessing user password hashes in the USR02 database table. Also, such data must not leave your system. SecurityBridge helps you detect such leaks in real-time.
Encrypt data in transfer
SAP systems exist in a network and exchange data with the end user’s SAP Logon Client and other SAP and non-SAP systems via interfaces. This communication must be encrypted. For this purpose, SAP offers the use of its cyptolib to activate SNC. We recommend the use of SNC, especially between client and server. If the data traffic is not encrypted here, then the user passwords are transmitted in plain text. Furthermore, you cannot distinguish whether the user is accessing classified data with user connections.
Summary
SAP systems offer sufficient protection for your data if you operate them securely. However, to counter today’s threats, you need to consider additional measures for SAP data security. This is especially true if your authorization concept is no longer effective, and data needs to be transferred out of the secure premise of your SAP system. In addition to assigning authorizations based on a need-to-know principle, you should monitor user activities to implement active threat detection.
