The week after SAP RECON
[CVE-2020-6287]

Chapters
Share Article

SAP Patch Day July 2020 shocked the customer community of SAP SE. Although everyone assumed that zero-days with a high-risk potential of exploitation exist, the recent Patch Day has delivered evidence.
While everyone was mentally preparing for a silent summer period SAP released the patch for a previously unknown flaw called #RECON. The vulnerability was named #RECON after its possibility to execute REmote COde on Netweaver systems. Eventually, the security teams watching for the SAP Patch Day release in July also hoped for a „silent“ release without many high CVSS vulnerabilities or at least only such that exist in components that are not commonly used. 14th July 2020 has proven otherwise, the day when SAP released a patch for a zero-day vulnerability in AS Java that impacts many of their 400.000 customers worldwide.
SAP Patch Day July 2020
The vulnerability described with CVE-2020-6287, allows attackers to take full control over an AS JAVA instance. The flaw existed already for many years in SAP applications running on top of SAP NetWeaver AS Java Version 7.30 until 7.50, within Software Component LM Configuration Wizard (LMCTC).
Impact and risk
The given CVSS 10.0 indicates the impact is severe. Already on the 17th July and only 3 days after the patch release, a well known SAP security researcher released a POC exploit on Github
Quick and dirty (sorry i did it during lunch time) PoC for SAP RECON vulnerability (CVE-2020-6287, CVE-2020-6286).https://t.co/i2pImKwmEU
— Dmitry Chastuhin (@_chipik) July 15, 2020
The famous pen-testers framework Metasploit received a thus far not committed new module testing the attack to inject new users. Visit this link for more information about it
We can confirm both exploits work as promised. The inconvenient truth is thus – we are dealing with a very critical vulnerability that impacts many SAP customers. Especially since the application server Java is an essential part of the Enterprise Portal product of SAP that may be exposed to untrusted networks. Attackers can find such systems using google search queries!
What are the next best actions?
The best advice-giving in severe situations is to stay calm and remain clear-headed. If you sense a bit of panic coming up, take a deep breath and follow the steps described below:
- ASSESS YOUR RISK
Before any action can be done, you, the defender need to understand and assess your individual risk situation. In case you answer the two questions with „yes“, you need to add the consideration that your system(s) have been compromised already.– Do you run SAP Netweaver AS Java instances?
– Is any of these instances reachable from unprotected networks such as the internet? - INVENTORY
– Unless already known, create a list of vulnerable instances, listing the component version (LMCTC – LM CONFIGURATION WIZARD).– Understanding the potential impact requires knowledge of which systems are connected to vulnerable instance(s).
– Check whether the Java Service Application described in 2939665 – Disable/Enable LM Configuration Wizard | Critical API’s in LM Configuration Wizard is active. - MITIGATION PLAN
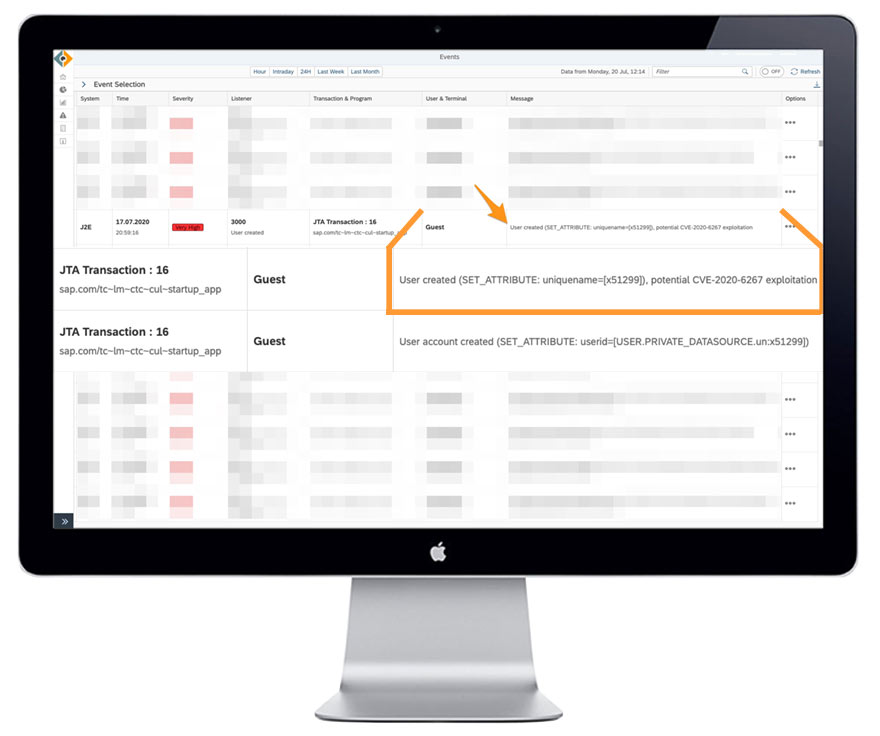
– PLEASE TRY TO INSTALL THE PATCH AS SOON AS POSSIBLE. Unless you can do this almost immediately, we recommend you to deactivate the LM Configuration Wizard application on all Java instances.– Irrespective of the deactivation we recommend you to analyse the AS Java Logs searching for J2EE_GUEST access.
Good indicator that something gone wrong on your Java #SAP system when J2EE_GUEST is creating users 🥳 probably related to CVE-2020-6287 cc @_chipik 😉 pic.twitter.com/4pt9ep8ZYQ
— gelim (@gelim) July 17, 2020
We strongly recommend you to sift through all logs available to ensure your system was not compromised already.
– Once done, you need to plan an SPS update to apply the final solution! According to the Patch you need to install the service pack as described in 2934135 – [CVE-2020-6287] Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard).
SecurityBridge is a modern SAP Security Platform, natively build in SAP. It enhances your SAP landscape with a Thread Detection Sensor (IDS) to guard your systems 24/7. SecurityBridge caught user inject caused by exploitation of CVE-2020-6782.
Zero-Day Vulnerabilities
The recent Patch Day again provides evidence that so-called Zero-Day vulnerabilities exist within the vast product portfolio of enterprise applications. CVE-2020-6287 and CVE-2020-6286 existed for many years and remained unnoticed.
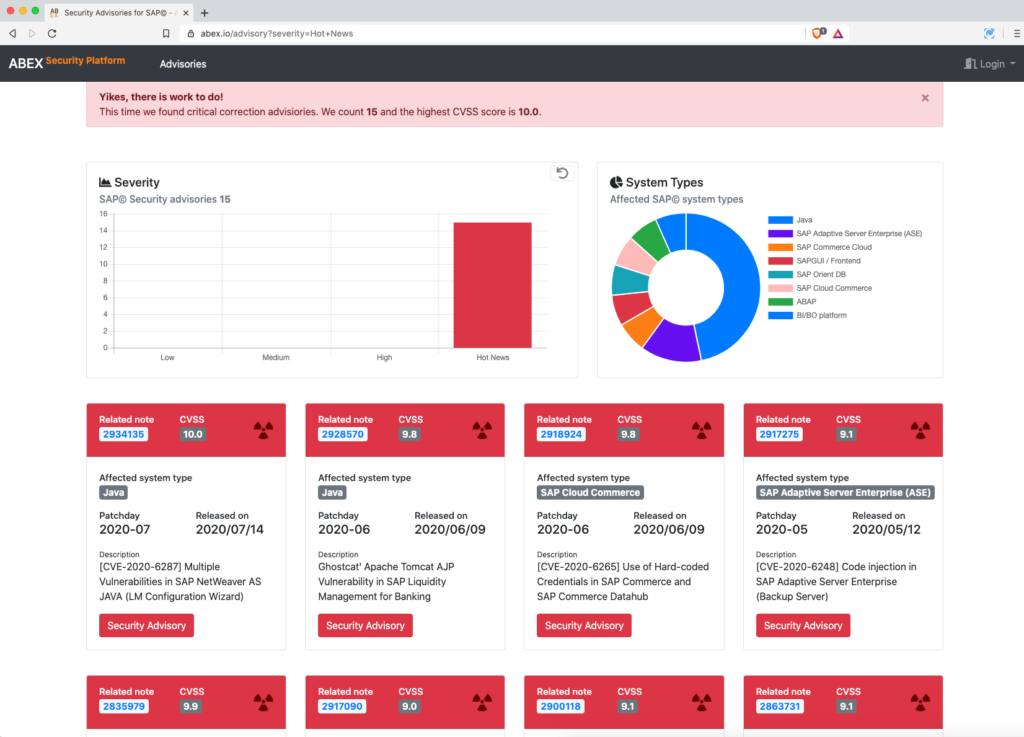
A quick query on high severity vulnerabilities for SAP in 2019 and 2020 shows there are far more highly critical patches that do not make the news. e.g. CVE-2020-6207, affecting the same lifecycle management component, released March 2020, also has an exploitation scoring of 10.
Run your own search on ABEX.io – ABEX Security Platform
Only intense and continuous monitoring of the systems would have allowed customers to reveal the exploitation of the Zero-Day-Vulnerability. The same was suggested by the Cybersecurity and Infrastructure Security Agency (CISA), in situations where patches cannot be applied.