A Comprehensive Guide to SAP Security: Importance, Best Practices, and Solutions

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
Cybersecurity is a paramount concern for organizations worldwide, but what is SAP security, and how can you best protect these business-critical systems?
Among ERP vendor tools that require robust security measures, SAP (Systems, Applications, and Products in Data Processing) stands out, as it is the foundation for critical operations and business processes in large enterprises.
Protecting SAP data through various security measures and compliance with data privacy regulations is crucial.
However, these systems’ complexity makes them a prime target for cyber attacks. This is where SAP security comes into play, ensuring that data and processes are protected from cyberattacks.
What is SAP Security, and why is it crucial?
SAP security encompasses strategies, tools, and best practices to safeguard SAP customers from threats. It protects confidentiality, integrity, and availability within SAP environments.
It prevents unauthorized access, ensures compliance with regulatory requirements, detects and mitigates security vulnerabilities, and maintains the overall health of the SAP applications and infrastructure.
Securing SAP also involves safeguarding ABAP code, emphasizing the importance of secure coding practices to prevent code injection and other vulnerabilities.
SAP security falls under the broader cyber security umbrella, specifically application security. According to Accenture’s “State of Cyber Security Resilience,” cybersecurity is a good investment.
SAP Security Fundamentals
Understanding the risks and threats associated with SAP technology is crucial. These systems are the backbone of an organization’s infrastructure, making them prime targets.
Access Control and Authorizations
Robust access control and authorization mechanisms ensure only authorized users can access sensitive data (such as customer data) and functionalities.
SAP System Configurations
This includes following best practices for system setup, such as enforcing password policies, securing communication channels, and updating system configurations to address potential vulnerabilities.
Secure Development
By integrating security into every phase of the development process, organizations can identify and mitigate risks early, reducing the likelihood of breaches.
SAP Audits
Security audits and assessments are necessary to identify and address security gaps and ensure adequate security measures.
Implementing threat detection mechanisms like real-time monitoring and advanced analytics enables organizations to detect and respond to potential threats promptly.
Key components of SAP Security
Only authorized users should access specific data within the SAP system. Monitoring is crucial for the surveillance of SAP environments to detect threats and maintain a strong security posture and should include:
-
Implementing robust authentication and authorization mechanisms to verify identities and access rights through SAP identity management.
-
Transaction monitoring to manage critical transactions and ensure proper authorization, particularly for transactions and interfaces with external access.
-
Secure communication protocols to protect data in transit, preventing interception and tampering.
-
System audits to identify security gaps and ensure that security measures are effective.
Holistic SAP Security
A holistic approach to SAP security considers the entire ecosystem, with four central pillars:
- Secure Configuration: This includes setting up secure communication channels, enforcing password policies, and applying best practices for configurations. SAP Identity Management plays a crucial role in centralized user access management and ensuring the integrity of identities throughout the entire identity lifecycle. SAP Cloud Identity Services facilitate cloud-based user authentication and provisioning, highlighting their importance for integration scenarios within an intelligent enterprise security framework.
- Patch Management: This involves staying informed about security updates and applying patches to minimize the risk of exploitation.
- ABAP/4 Code Vulnerability Management: Conduct reviews and security assessments of custom ABAP/4 code to identify and remediate vulnerabilities. This includes following secure coding practices and using automated tools to identify security issues.
- Detection of Threats and Malicious Activities: Real-time monitoring and threat detection systems are used to identify and respond to potential security incidents, including advanced analytics and machine learning, and to detect anomalies and unusual activities.
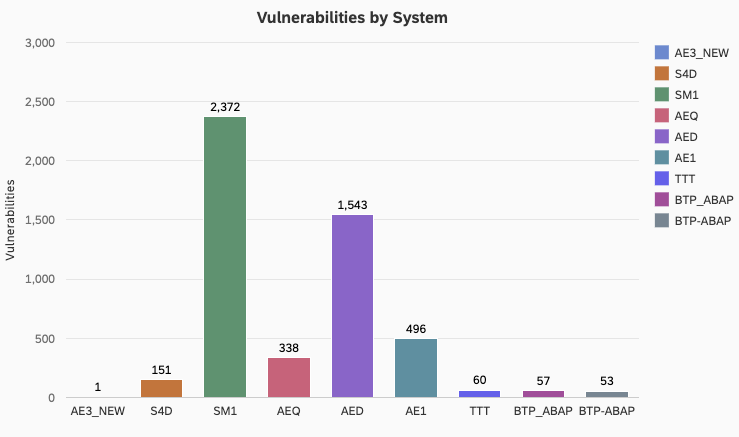
Top 12 SAP Security Configurations
These recommendations focus on SAP SE, specifically SAP S4/HANA and SAP NetWeaver ABAP/4, both on-premises and in the SAP cloud.
The SAP Solution Manager system provides diagnostics, security checks, and automated alert reporting. It enables users to maintain optimal performance and effectively implement necessary configurations and SAP Notes.
While this increases the complexity of securing SAP, integrated cybersecurity platforms like SecurityBridge secure even the most complex environments.
-
Enable the SAP Security Audit Log (SAL). Ensure the SAL is enabled by setting the profile parameter rsau/enable = 1. The SAL is the standard SAP mechanism for recording security-related information and events.
-
Control the RFC Gateway and Filter Unauthorized IPs. Configure RFC destinations to prevent attackers from accessing production systems through RFC hopping. Ensure IP filtering to block unauthorized connections.
-
Identify and Remove Critical SAP Authorizations. Remove unnecessary authorizations, such as access to all table contents via SE16. Implement Privileged Access Management for SAP and enforce the principle of least privilege.
-
Manage and Reduce the Attack Surface of SAP ICM. Deactivate unused services within the SAP Internet Communication Manager (ICM). The SAP Web dispatcher, which acts as a gateway for HTTP(s) requests into your system, can reject or accept connections.
-
Utilize SAP Code Vulnerability Analyzer. This crucial ABAP add-on for SAP NetWeaver AS analyzes your source code and identifies security vulnerabilities before production.
-
Leverage SAP Process Control for GRC. Implement SAP Process Control to enhance governance, risk management, and compliance (GRC) activities within your SAP ecosystem. This solution provides better visibility, control, and automation of GRC processes.
-
Update the Password Hash Algorithm. To prevent brute-force attacks, activate your SAP version’s latest password hashing mechanism. Set the profile parameter login/password_downwards_compatibility = 0 to ensure passwords are stored securely.
-
Enable Table Change Logging. Use the profile parameter rec/client to enable Table Change Logging and protect tables from unauthorized modifications. This mechanism logs changes to tables, though it does not cover changes made through imports using R3trans.
-
Encrypt Data in Transit. Implement Secure Network Communications (SNC) and secure HTTP communication using SSL certificates to encrypt RFC communication.
-
Ensure Transport Control is State-of-the-Art. If the standard SAP Transport Management System (STMS) is insufficient, a transport deployment system should be implemented. Regularly check for security patches for R3trans and the transport control program (tp) to mitigate risks associated with transport requests, especially from external sources.
-
Enable Virus Scanning for MIME Objects. To prevent the upload of malicious content into an SAP system. This is particularly important for environments audited for tax compliance.
-
Implement and Enforce System Change Mode. Adhere to best practices by preventing direct changes to the SAP production system. Updates for customization and the codebase should be applied via transport requests.
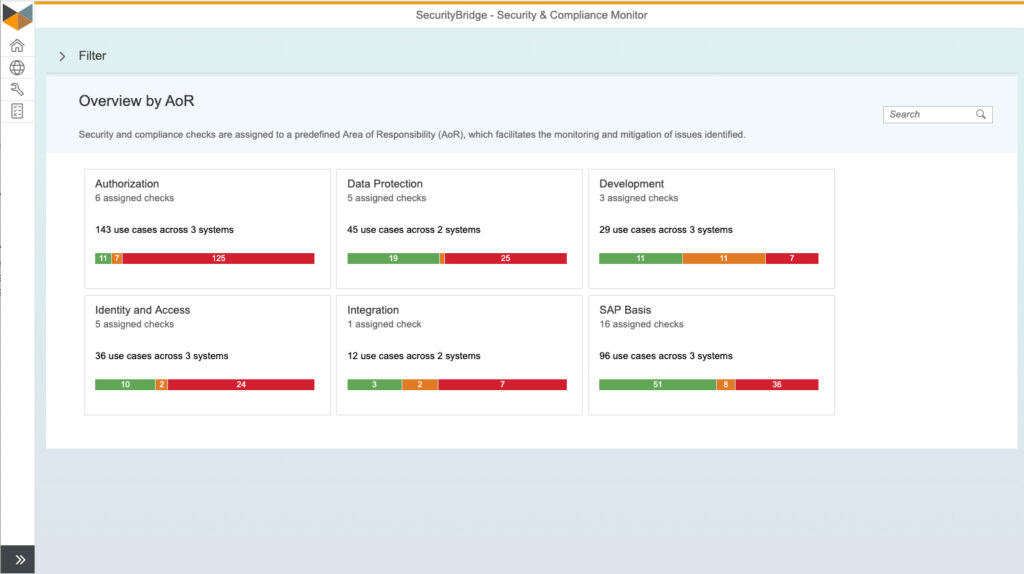
SecurityBridge Workcenter for Cybersecurity
Changing the Paradigm: From Audit to Continuous Security
Periodic audits can leave organizations vulnerable to threats emerging between audit cycles. SAP security solutions are crucial in automating reports, maintaining SAP data integrity, and ensuring prompt notification about critical configurations and SAP Notes.
To address this, there is a growing shift towards continuous security. This paradigm involves real-time monitoring, continuous vulnerability management, and proactive threat detection. By leveraging advanced analytics and machine learning, organizations can detect anomalies and threats as they occur.
Continuous security also includes automated detection of missing security updates, ensuring that the latest security patches are applied promptly to mitigate vulnerabilities.
How to get started with SAP Security?
Getting started can seem daunting, given the complexity of SAP solutions. However, organizations can start by focusing on a few key areas:
-
Risk Assessment: Conduct a thorough risk assessment to identify critical assets and potential vulnerabilities within the SAP environment. The SAP Basis operating manual contains essential guidelines for system settings, which are crucial for establishing and maintaining security.
-
Access Control: Implement strict access control measures to ensure only authorized users can access sensitive data and functionalities.
-
Regular Audits: Perform security audits and vulnerability assessments based on individual security policies or baseline templates to identify and remediate security gaps.
-
Security Policies: Develop and enforce comprehensive security procedures that cover all aspects of SAP security. Mapping security controls from your preferred cyber security framework, i.e., NIST CSF is recommended.
-
User Training: Educate users about security best practices and the importance of following security policies.
Security Governance in SAP
Security governance is a cornerstone of securing SAP, ensuring the systems integrate with organizational security policies and procedures. Effective security governance in SAP includes:
-
Defining Security Policies and Procedures: Establish comprehensive security policies and procedures tailored to SAP. These policies should cover all security aspects, from access control to incident response.
-
Establishing a Security Organization: Assign specific roles and responsibilities within the security organization. This ensures that everyone knows their part in maintaining the security posture.
-
Implementing a Security Management Framework: Adopt a recognized security management framework, such as the NIST Cybersecurity Framework, to guide your security efforts. This framework provides a structured approach to managing and reducing cybersecurity risk.
-
Conducting Regular Security Assessments: Perform regular security assessments and risk analyses to identify potential vulnerabilities and ensure adequate security measures.
-
Compliance Requirements: Comply with regulatory requirements and industry standards, such as the General Data Protection Regulation (GDPR) or the California Consumer Protection Act (CCPA), which requires the organization to delete customer data when requested. Effective compliance management protects your organization from legal repercussions and enhances overall security.
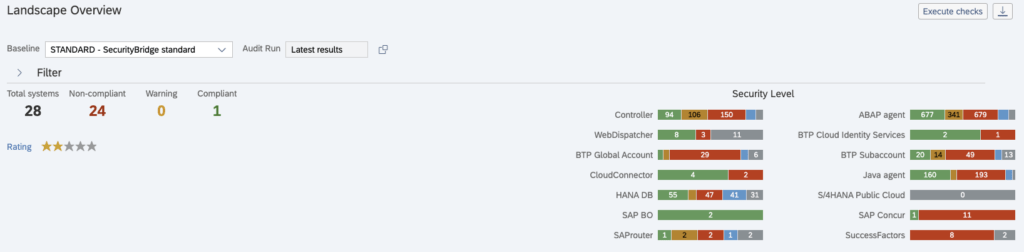
Secure Software Development Lifecycle in SAP
A secure software development lifecycle (SDLC) is essential for ensuring the security of SAP systems. Integrating security into every phase of the software development process helps identify and mitigate risks early, reducing the likelihood of breaches. The secure SDLC involves:
Security Risk Assessments and Threat Modeling: Conduct thorough security risk assessments and modeling to identify potential vulnerabilities and threats during the design phase.
Secure Coding Practices and Code Reviews: Implement secure coding practices and conduct regular code reviews during development to ensure secure code without flaws.
Security Testing and Vulnerability Assessments: During the testing phase, comprehensive security testing and vulnerability assessments are performed to identify and address any security issues.
Secure Configuration and deployment: Ensure systems are securely deployed and configured, following best practices and security guidelines.
Continuous Monitoring and Maintenance: After deployment, continuously monitor and maintain the security of SAP systems to address new vulnerabilities and threats as they arise.
SAP Security Challenges and Risks
SAP environments are complex and pose unique security challenges and risks. Some of the critical challenges and risks include:
-
The complexity of SAP Solutions: SAP systems’ intricate nature makes implementing and maintaining controls challenging.
-
Lack of Visibility: Limited visibility into SAP events can make detecting and responding to security threats challenging.
-
Insufficient Controls: Inadequate security controls can leave SAP systems vulnerable to attacks.
-
Inadequate Patch Management: Failing to apply security patches promptly can expose SAP systems to known vulnerabilities.
-
Insecure Custom Code: Custom code not developed with security in mind can introduce significant security risks and vulnerabilities.
To address these challenges and risks, organizations must implement robust security controls, conduct regular security assessments and risk analyses, and ensure compliance with regulatory requirements.
Security Monitoring and Incident Response
Security Monitoring
Monitoring SAP systems is essential to detecting security-related events and incidents, such as unauthorized access, data breaches, and compromises. By monitoring SAP systems, organizations can identify potential threats early and proactively mitigate them via threat detection.
Incident Response
A well-defined incident response plan ensures that the organization can respond quickly and effectively when a security incident occurs. This plan should outline the steps to be taken in the event of a security breach, including identifying the source of the incident, containing the threat, and recovering affected systems.
Integrate SAP data into the SOC (SIEM)
Integrating SAP security monitoring with centralized security teams can enhance organizations’ ability to detect and respond to threats. The SOC provides oversight and immediate threat identification, improving security posture.
Best Practices for Implementing SAP Security Solutions
Authorization mechanisms ensure appropriate access to specific data and functionalities. However, securing SAP systems requires much more.
A comprehensive SAP security strategy must go beyond authorization to include:
- Threat Detection for SAP: Implementing real-time tools and processes to detect and respond to potential threats.
- Vulnerability Management for SAP: Regularly scanning for and addressing security vulnerabilities in the SAP environment.
- Compliance: Ensuring compliance with regulatory requirements and industry standards through ongoing monitoring and reporting.
- Incident Response: Developing and maintaining an incident response plan to quickly address security breaches and minimize their impact.
- Integrating SAP security monitoring with a centralized Security Operations Center (SOC) to provide critical oversight and immediate threat identification, enhancing the security posture of your SAP solution.
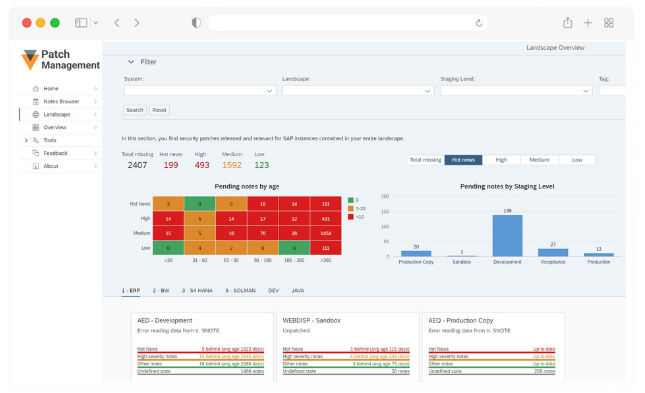
SecurityBridge Patch Management
Patch Management
Monitoring Security Notes and Patches
Regularly monitor SAP security notes and patches to stay informed about the latest security updates.
Prioritizing and Applying Patches in SAP systems
Prioritize patches based on their risk and impact and apply them promptly to mitigate vulnerabilities.
Testing and Validating Patches
Before deployment, thoroughly test and validate patches to ensure they do not introduce new issues.
Timely Deployment
Ensure that patches are deployed in a timely and efficient manner to minimize the window of vulnerability.

Protecting Critical SAP Transactions and Data
Protecting critical SAP transactions and data is essential to ensuring business-critical information’s confidentiality, integrity, and availability.
Implementing access controls and authorization mechanisms is the first step in safeguarding sensitive customer data and transactions.
Data encryption is crucial for protecting data in transit and at rest. Encrypting data ensures that it cannot be read without the appropriate decryption key, even if it is intercepted.
Data masking, on the other hand, obscures sensitive information, making it unreadable to unauthorized users.
Logging and transaction monitoring sap system mechanisms are vital for detecting and responding to security incidents.
Continuously monitoring critical transactions can help organizations identify unusual activities and potential breaches.
Logging mechanisms provide a detailed record of all transactions, which can be used for forensic analysis during a security incident.
The Best SAP Security Solutions and Tools for Threat Detection
Ensuring the security of your business-critical SAP solutions is paramount, and finding the right software can be challenging.
SecurityBridge stands out as a single platform that handles all your SAP security needs while seamlessly integrating with your organization’s overall cybersecurity monitoring – eliminating blind spots for security teams.
Securing SAP can seem overwhelming, but with SecurityBridge, you get a platform that is easy to learn and use, quick to implement, and continually guides you to improve your security posture.
Ready to secure your SAP landscape? Contact us today for a personalized assessment.
Enhancing SAP Enterprise Threat Detection with SecurityBridge
The SAP Enterprise Threat Detection (SAP ETD) application offers essential security information and event management (SIEM) capabilities.
SecurityBridge evaluates security configurations and applies necessary patches to mitigate critical vulnerabilities. By baselining the SAP security posture, SecurityBridge can feed all detected vulnerabilities directly into SAP Enterprise Threat Detection, enhancing the monitoring process.
SAP Security Community and Resources
Leverage SAP user groups and community resources to stay current with the latest security best practices, threats, and solutions.
SAP also provides various security resources to help organizations implement and maintain robust controls. These resources include security guides, whitepapers, and webinars.