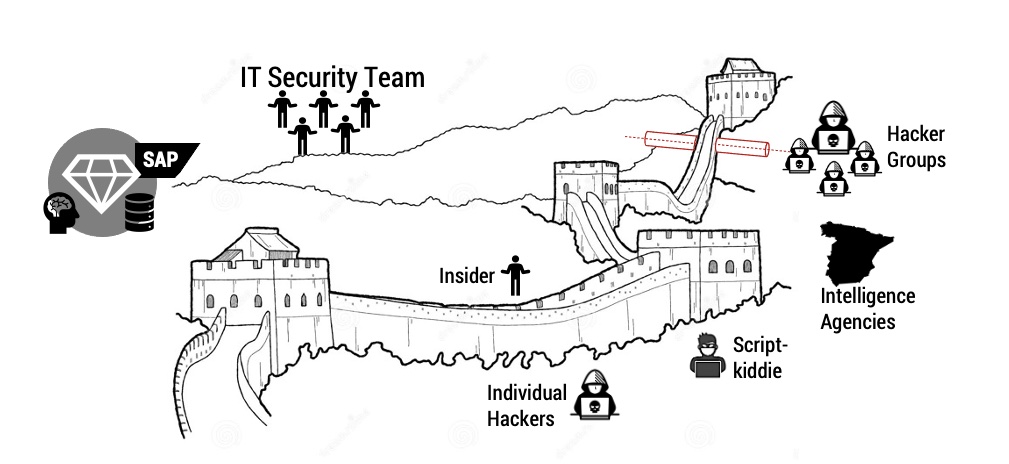
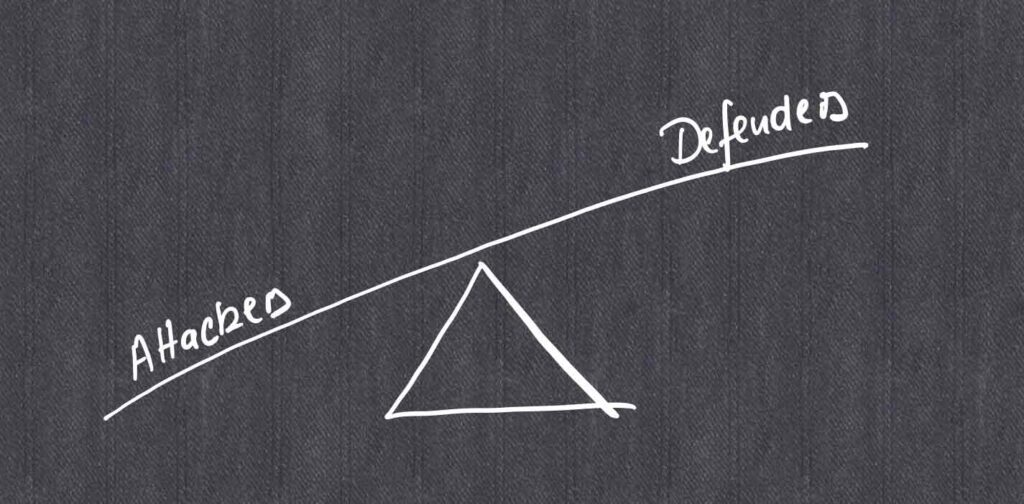
The asymmetry between attackers and defenders

Chapters
Share Article
SAP systems manage many vital aspects of our businesses. SAP based applications serve as the digital backbone of many organizations supporting logistics (SAP LO), financials (SAP FI), human resources (SAP HR), and other important processes. SAP modules hold and process sensitive data of companies that need to be protected from increasing cyber threats around the globe. It is commonly known that such enterprise-critical applications provide a huge attack surface that customers have to manage. Ignoring a single attack vector could lead to an outage, data exfiltration, or corruption of important data assets. Loss of reputation and financial damage or legal fines are at risk for a company if a threat actor succeeds.
SAP systems contain millions of dollars’ worth of information that must not be disclosed to attackers. Unfortunately, the likelihood of such an event is very high because the company’s defenders have engaged in an unfair battle.
Complex, enterprise-critical systems, are not secure by design, and by default. Defenders must put in an effort, usually manual, to maintain and build a secure configuration. Once accomplished, the security posture needs to be maintained, continuously and long-term, while the system is subject to frequent change and version updates.
SAP Attackers’ advantage
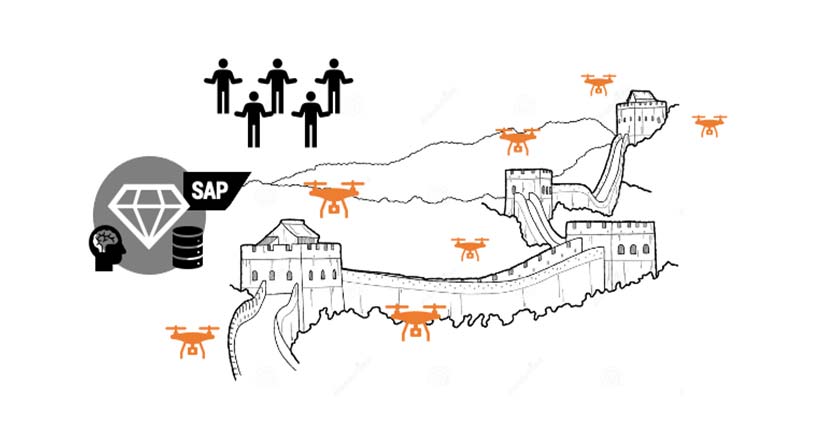
A simple principle of life is that destroying is easier than building. Unfortunately, in many IT scenarios, it is also easier to attack than to protect. Why is this so, you might ask? Imagine the thousands of parameters that exist to secure an SAP system, those represent a catalog of vulnerability an attacker could choose from unless those are maintained with security in mind.
Besides the secure configuration, the defenders need to monitor for commonly known security flaws within the standard product and apply the manufacturer’s patches soon after their release.
The SAP and the cybersecurity teams mostly have limited resources to cover all attack vectors. Consequently, they may lose the battle and an attacker takes advantage of a small loophole to carry out an attack with immense impact on the organization.
SAP protection is a challenging task due to the complexity of the system, but there are other factors that also contribute to the attacker’s advantage. Many of these factors are on the side of attackers, let’s have a look:
- One vulnerability is enough
- Limited people
- Human error
- Unknown vulnerabilities (Zero Days)
- Inefficient detection and response process
- Logging not enabled
- Insufficient hardening of systems
- Missing overview or transparency
- Lengthy processes cause late patching of vulnerability
- Custom code that contains vulnerabilities
These are just a few reasons, while there may be other conditions under which attackers can gain access to your SAP systems to steal your company’s data.
SAP Protection
A drastic transformation must take place to bring about a change in the scenario outlined above. With the goal of increasing SAP security, organizations must begin to equip themselves with tools to help defend and, more importantly, monitor their virtual walls. In a virtual world, walls are typically not broken down, they are bypassed.
Experience shows that it does not help you to define a security requirement for SAP-based systems that you cannot implement or comply with. In particular, ensuring the compliance with the directives involves recurring efforts, audits, and adjustments and is not only often neglected in reality, but is also too tedious.
With the right tool, even small teams can build and maintain a more effective line of defense. The “right” tool is characterized by helping you monitor the configuration, detect intrusions, and eliminate vulnerabilities in the standard product or custom code. Only by gaining control over these areas will it be possible to protect and defend SAP systems in an ongoing Cyber War.
Seize your chance and use technological evolution to your advantage.
Finally, I would like to end on a note that you probably won’t like. No matter what manual protections you have in place for your SAP systems, they are probably already outdated, modified, or ineffective.
Be aware that your opponents are not static, but will react very dynamically to changing circumstances. Attackers are constantly changing their methodologies and techniques and, thanks to the Internet, have access to an almost infinite knowledgebase.
Securing your SAP landscape should be imperative, but unfortunately, most SAP systems are insufficiently secured. The whitepaper describes the major steps on your road to securing enterprise-critical applications based on SAP SE products.
Download the whitepaper YOUR ROAD TO SAP SECURITY to learn about the major milestones towards increasing the cybersecurity posture of your SAP systems