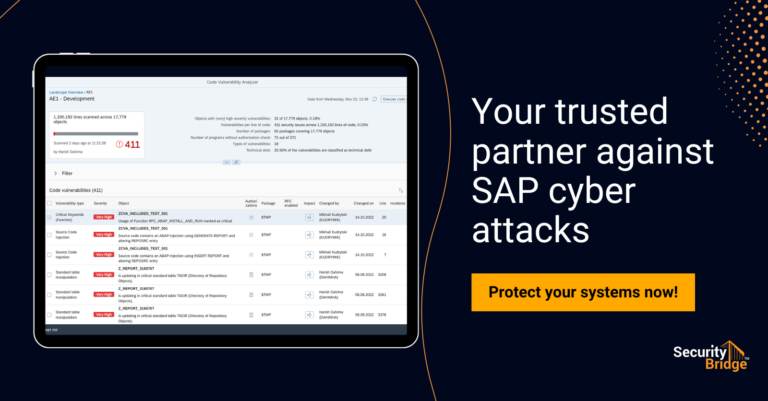
Audit Logs in SAP

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
What is a Security Audit Log in SAP?
A Security Audit Log is a vital SAP system tool to record and track security-related events and changes. This audit log provides a comprehensive view of critical security events, enabling employees responsible for security and auditors to monitor and analyze the system’s security posture.
The security audit log is essential to securing SAP. It captures information about security events, allowing organizations to detect and respond to threats promptly.
This proactive approach ensures that any anomalies or unauthorized activities are identified and addressed before they can escalate into critical incidents.
Why are SAP Audit Logs so important?
SAP Security Audit logs record all activities and changes occurring within the SAP system. These security audit logs include log files that record critical security-related activities, such as failed login attempts and changes to user records.
These logs are crucial for security, compliance, and troubleshooting. They provide a detailed history of user actions, system events, and data modifications and help organizations monitor and maintain the protection of their SAP environment.
They also track changes to audit classes, such as changes to user master records, which are essential for evaluating system activities. In fact, they are often the single point of truth for detecting malicious activities in an SAP system.
Unattended or inactive SAP security audit logs may pose a severe impact during an incident’s detection and response and may leave organizations blind to issues such as data modification.
Benefits of Using Security Audit Logs
Utilizing the security audit log in your SAP system environment offers a multitude of benefits that enhance overall protection and operational efficiency for SAP customers:
Improved Security: Audit logs provide a detailed record of all security-related events within the SAP landscape. This comprehensive logging allows organizations to detect and respond to potential cyber threats, ensuring that suspicious activities, such as multiple failed logon attempts, are investigated and mitigated quickly.
Compliance: Maintaining audit logs is crucial for meeting regulatory requirements. These logs provide a verifiable record of all security-related events, helping organizations adhere to various legal and industry standards.
Forensic Analysis: The security audit log is invaluable for forensic analysis in the event of an incident. They provide detailed information that helps organizations investigate the incident, understand the sequence of events, and identify the root cause, facilitating effective incident response and remediation.
Security Analysis: Regularly reviewing the security audit log offers insights into the system’s security posture. By analyzing these logs, organizations can identify vulnerabilities, monitor for unusual activities, investigate data modification, and take corrective actions to strengthen cybersecurity measures.
Is the SAP Security Audit Log active by default?
The inconvenient truth is “No”. Various Log sources exist that need to be activated by clients’ SAP basis experts or can be filtered. It ultimately falls into the responsibility of the SAP-using organization to decide which logging is relevant, whether legal obligations or limits exist that prevent the activation of logging, and to establish a regular assessment process.
Which SAP Security Audit Logs must I activate for robust Cyber Security?
The simple answer would be – the more, the better.
The reason for this vague statement is the assumption that organizations can make an educated decision based on available information. Acquiring as much information as possible appears vital, but unfortunately, it is not simple.
Each SAP system creates gigabytes of logs per day, which causes system fatigue. The SAP Security Audit Log holds information about business transactions that are not immediately relevant to an analyst assessing a potential incident (for example, a successful or unsuccessful transaction or multiple unsuccessful transaction starts).
Tracking changes to user master records is the best practice for monitoring security-related system information. This functionality allows auditors to track access activities related to user management within the SAP System, ensuring regulatory adherence and maintaining security standards.
But let’s start with the basics: the minimum SAP Security Audit Log an organization needs to activate is the Security Log. A SAP Audit Log exists for the S4/HANA Stack and the databases. Furthermore, we also recommend not using filters on this audit log.
Ensure the Audit log SAP Settings are Properly Configured
Configuring the security audit log in an SAP system is critical to ensure comprehensive monitoring.
Here’s a step-by-step guide to help you set it up effectively:
Activating the Security Audit Log: The first step is to activate the audit log within the SAP system. This activation is essential to start recording events and ensure that all relevant activities are logged.
Defining Audit Log Settings: Once activated, you must define the audit log settings. This includes specifying the types of events to be recorded, determining the log file location, and setting the log file size. These settings ensure the audit log captures all necessary information without overwhelming the system while meeting the auditors requirements.
Assigning Roles and Permissions: It’s crucial to assign appropriate roles and permissions to users responsible for monitoring and analyzing the SAP audit log. This ensures that only authorized personnel have access to sensitive log data and maintains the information’s confidentiality.
Configuring Filters: To make the SAP audit log more efficient, configuration of filters that specify the types of events to be recorded and the users to be monitored. This targeted approach helps focus on the most critical security events and reduces unnecessary log entries.
Regularly Reviewing and Updating the Audit Log Settings: Finally, it’s important to regularly review and update the audit log settings, including long term data access policies and user permissions.
This process ensures that protection is maintained and the audit log meets the organization’s evolving cybersecurity needs.
Important SAP Audit Logs that you need to know:
Security Audit Log (SAL)
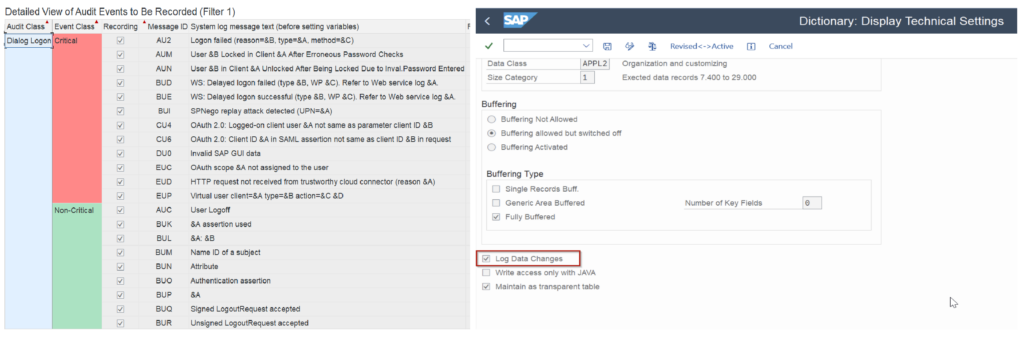
The Security Audit Log is a SAP standard tool for securing the infrastructure, which records security-relevant system and application activities, such as logon attempts, failed logon attempts, and changes to user authorizations. It also tracks changes to user master records, ensuring a detailed record of user interactions and security related changes.
Access to the Security Audit Log is tightly controlled to prevent unauthorized modifications, and configuration of the Security Audit Log to capture various events and activities based on your organization’s policies.
- The audit log can be stored in different ways – for example, in a file system. Hence, there should also be a strategy for log retention at the application level and for archiving it.
Change Document Logs:
These logs record changes made to specific data objects, such as customer master records, material master records, or vendor master records.
Change document logging helps organizations track who made, what kind of changes, and when they were applied.
You can enable change document logs for specific SAP objects through customization settings.
Application Log files
The Application Log records information about application-specific events, such as errors, warnings, and messages generated during program execution. Configuration of the Application Log to record specific events based on your requirements.
You can use it mainly for troubleshooting and tracking application processes.
Transport Log files
This log tracks changes in transport requests and their objects, helping administrators and developers monitor changes to configuration settings and custom developments as they are transported between systems.
System Log (SM21)
The System Log (SM21 transaction) monitors the SAP system’s overall health and performance and provides an overview of system-wide events and messages, including system-level errors and warnings.
Data Change Logs (Database Logs) and Table logs:
Data change logs are critical for auditing and tracking changes to sensitive data. The recorded changes, including inserts, updates, and deletes, are made directly to the database tables.
Custom Audit Logs
SAP also allows organizations to create custom audit logs to record specific business processes or events not covered by standard logs. These can be developed using SAP’s auditing and logging framework.
In conclusion, to effectively use and manage SAP audit logs, it's crucial to:
Activate logging wherever possible.
Define and enforce security audit policies and procedures.
Review and analyze logs regularly to detect and respond to general security events and unauthorized activities.
Configure log retention policies to comply with legal and regulatory requirements, for example by determining long term data access.
Implement role-based access control to restrict access to audit logs.
Integrate SAP audit logs with centralized security information and event management (SIEM) systems for real-time monitoring and analysis.
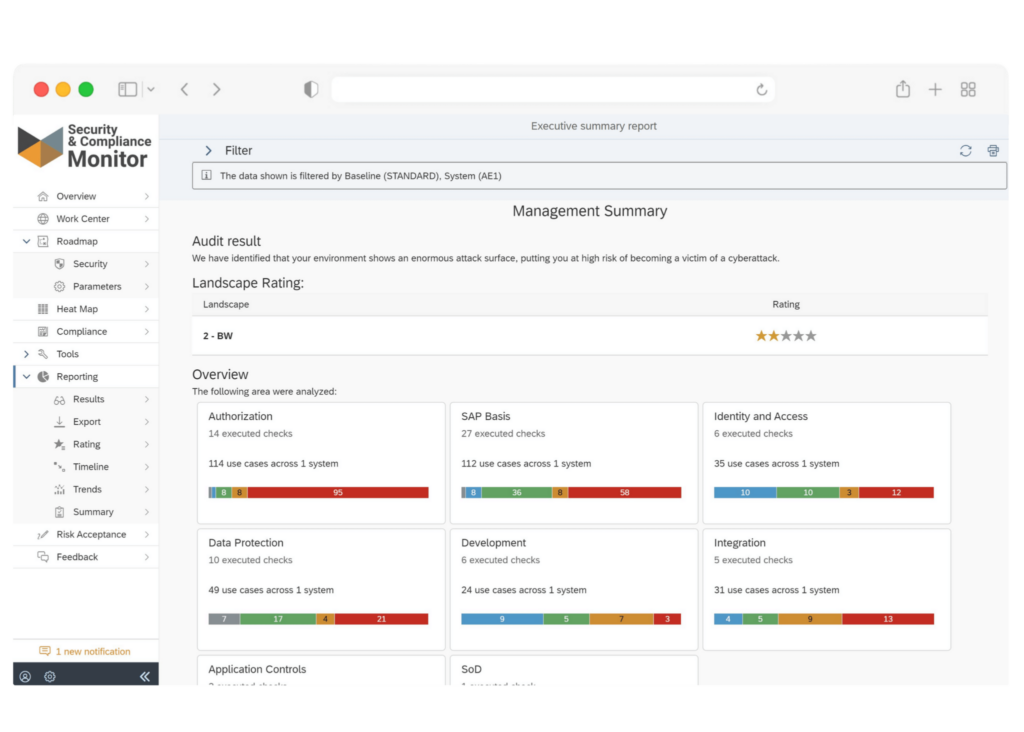
How can the SecurityBridge Platform help?
SecurityBridge leverages data from all the above audit logs and alerts events with a meaningful message so that an admin can easily track them and take appropriate action. The Threat Detection module for SAP also verifies the healthy setup of log sources and provides an alert in case a critical information source has been deactivated.
Here’s an overview of the SecurityBridge Threat Detection module.
Real-time Monitoring
Our Threat Detection module can integrate with SIEM systems to centralize SAP threat data. The platform provides real-time monitoring and alerting capabilities to notify security teams of suspicious activities or potential threats immediately.
Customizable Alerts
Organizations can configure alerts according to their specific security policies and necessities. They can be adjusted to trigger notifications for crucial events that require immediate attention, such as multiple failed logon attempts, which could, for example, be a sign of an ongoing brute-force attack.
Zero-Day Threat Detection
Thanks to advanced threat intelligence and heuristic analysis, the platform aims to detect zero-day vulnerabilities and emerging threats in SAP environments. This way, organizations stay ahead of potential threats that SAP has not yet documented or patched.
Anomaly Detection
SecurityBridge uses machine learning and behavioral analysis to identify abnormal activities within the SAP environments, such as unusual patterns in user behavior, unauthorized access attempts, or deviations from typical system activities.
Continuously Monitor Compliance
Our software solution enables adherence to regulations worldwide by continuously monitoring SAP systems against specific frameworks and generating reports and evidence essential in passing an SAP audit.
Threat Intelligence Integration
The platform incorporates threat intelligence feeds to stay current with the latest threats and vulnerabilities, and it can cross-reference SAP-specific threats with global threat intelligence sources.
Incident Response and Remediation
When threats or vulnerabilities are detected, the SecurityBridge platform offers guidance on remediation steps to mitigate risks and secure SAP environments. Furthermore, it provides recommendations and best practices for addressing security issues.
Detailed Knowledgebase
Finally, our platform has an integrated Knowledgebase that provides detailed information on findings, transparent risk descriptions, and mitigation recommendations.
SecurityBridge’s threat detection capabilities help organizations identify and respond to security threats and vulnerabilities in their SAP landscapes, ensuring the integrity and availability of critical SAP systems and data. It is the most comprehensive solution for SAP security that combines scanning, monitoring, and incident response into a single platform.