3 Benefits of an integrated and holistic SAP security platform

Chapters
Share Article
Although IT security departments often view SAP systems as just applications, it can be argued that SAP systems are actually an infrastructure in their own rights. This also means that the areas which are relevant for the “regular” IT security are also relevant for SAP solutions. Vulnerability Management, Code Security, Security Monitoring – all these areas need to be considered when securing SAP systems. And, similarly to cybersecurity, specialized solutions for each of these areas are also available for SAP systems. Sometimes those solutions are provided by 3rd party companies, however some tools are also available from SAP itself.
Choosing an SAP Security Platform
Selecting a specialized solution for each security area, however, has some limitations. Specifically, with SAP systems, which are accessed by heterogeneous user groups, connected to both legacy and other SAP systems. These are systems that control business processes covering different company departments, so a holistic approach is required in order to gain insight into potential risks and to offer full transparency of the security posture of each system, and its interconnectivity, as well as of the entire SAP landscape.
Securing your SAP landscape is no longer optional. Security shall be unavoidable but workable, a core requirement within today’s interconnected world. For this reason, SecurityBridge is designed to be always on, 24/7.
Deploying a holistic approach over specialized individual solutions offers three main benefits.
Three benefits of having SAP Security Platform
Context information can be considered and integrated very easily. Many custom applications, for example, contain security weaknesses such as missing authorization checks. This vulnerability will be picked up by any code security scanner. However, whether this vulnerability can be exploited depends on other security areas, such as configuration settings or the role and authorization concept. A holistic security solution will analyse the interconnectivity impact for those contextual settings and rate or categorize the security weakness accordingly. In contrast, if using specialized solutions, this would either need to be custom-made or involve significant effort to integrate those solutions. This leads to another benefit of holistic security solutions, namely:
A centralized dashboard where the security status of each individual system as well as the entire SAP system landscape is included in a holistic security solution for SAP. The standard SAP tools unfortunately don’t offer this functionality, and specialized solutions focus on providing dashboards only for their particular security area. Only a comprehensive solution covering all relevant security areas is capable of providing a 360°-degree view of the security posture of an entire SAP system landscape.
Best practices and standards for cybersecurity are based on processes rather than technological areas. The NIST framework for example, which also serves as the reference for all security related developments from SAP itself, is based on the procedures of, identify, protect, detect, respond and recover. Each of these steps touches many security areas. To enable those best practices across all technological areas requires a solution that also works across those technological areas.
While the benefits of using specialized solutions cannot be denied, they have limitations in that they leverage their full potential for specific requirements only. Holistic SAP security solutions, on the other hand, cover all aspects needed to find actual attacks. In addition, they are able to detect and mitigate vulnerabilities in custom coding, configuration and identity protection as well as report on missing patches.
Creating an effective line of defense and providing the transparency and insight needed is only possible when potential attack vectors are known and system activity across all areas is closely monitored. This can only be achieved with security solutions which comprehensively cover all relevant topics and integrate them into a “bird’s eye” perspective of the entire system landscape.
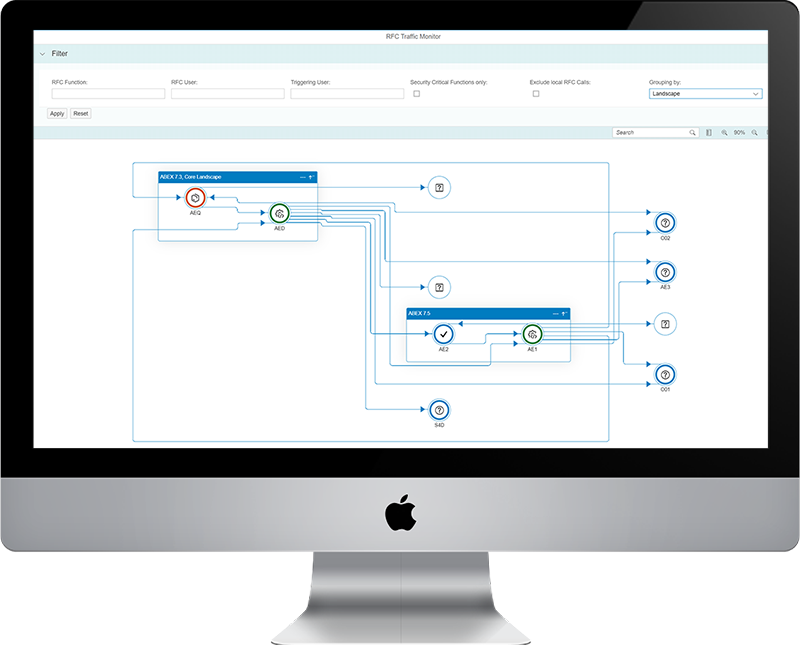
Latest addition to the SecurityBridge suite is a fully integrated interface monitor, which visualizes RFC interface connectivity across your SAP landscape. Through a bird’s eye view security critical traffic and vulnerable interfaces can easily be spotted.