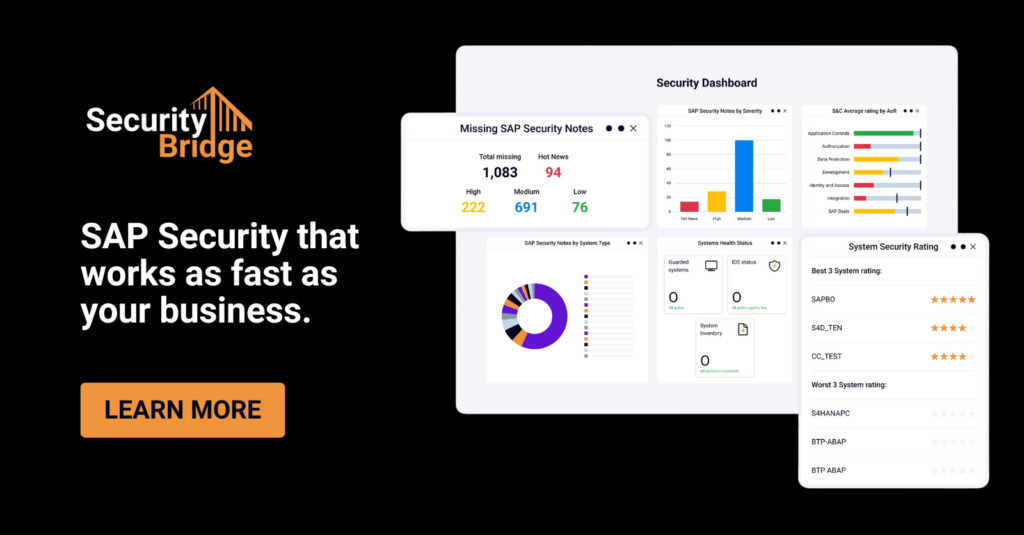
How to Prepare your SAP Security for Zero-Day Vulnerabilities

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
Zero-day vulnerabilities represent one of the most critical threats to enterprise SAP landscapes and a top concern for SAP security teams. The recent disclosure of CVE-2025-31324 – a critical flaw in SAP Visual Composer that allows attackers potential full control of SAP systems – has underscored the urgent need for robust and proactive security measures. This vulnerability, rated with a maximum CVSS score of 10.0, was actively exploited before a patch became available, leaving many organizations exposed. SAP’s response: an emergency out-of-band patch! This demonstrates the unpredictable and urgent nature of zero-day threats.
As SAP environments are the technical core of critical business processes around the globe, organizations must be prepared to respond immediately to emerging threats. This includes the ability to patch swiftly, detect threats and potential exploits in real-time, and maintain a hardened, resilient system configuration to minimize the impact of cyber-attacks.
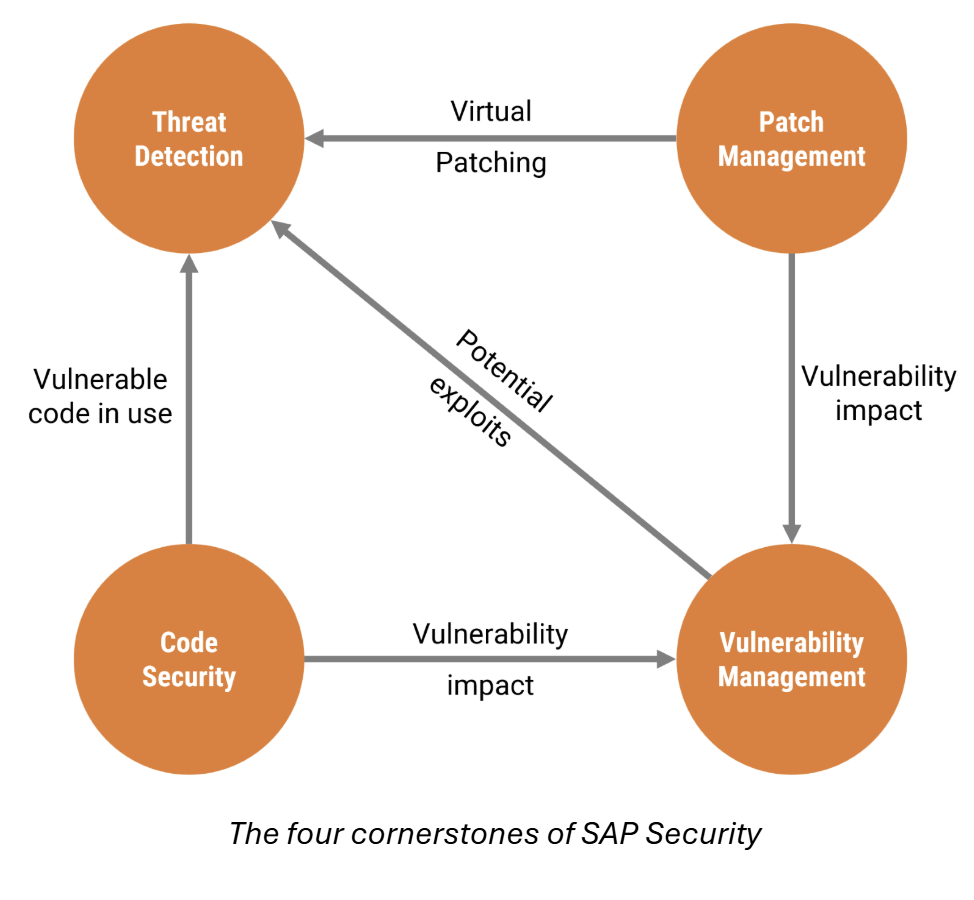
While continuously monitoring SAP SNote releases and engaging with the SAP security community is valuable, being immediately notified when a zero-day vulnerability is published – and having the ability to act, and swiftly – is even more critical. This article covers key organizational abilities based on the four cornerstones of SAP Security that enable cyber security teams to effectively shrink the window of opportunity for attackers and reduce the impact on their SAP landscape in the unfortunate event of a successful exploit.
Make sure you can patch immediately
Unpatched SAP systems are a primary target for attackers. Missing security patches leave known vulnerabilities open to exploitation, as seen with CVE-2025-31324 and previous critical flaws. Attackers actively scan for and exploit these weaknesses, making Patch Management one of the four cornerstones of SAP security. SAP patching is the most straightforward way to shrink your SAP attack surface by eliminating known weaknesses.
Understanding the severity and impact of new SAP Security Notes on your SAP landscape and their relevance to a specific system is key for efficient and short-term system patching. Therefore, customers need to balance patch severity and implementation effort across relevant patches for their specific SAP systems to burn down the patch implementation backlog efficiently and fast.
Patch Automation is an additional way to increase the efficiency of this process. While this is obvious from a high-level perspective, SAP Security experts know how complex and heterogeneous the SAP patch management topic is. This makes automation very challenging. Nevertheless, SecurityBridge has also innovated in this area of SAP Security by providing automated implementation for the majority of SAP Security Notes. If an SAP Note is considered ‘safe’ to deploy in the target system – and with no manual steps – it can be released through SecurityBridge’s Automated Patch procedure.
Use powerful and automated Threat Detection solutions
No matter how fast the SAP team can patch a system, there is always an initial time gap where the SAP landscape is at risk. A good mitigation for this scenario is to integrate Patch Management with another SAP Security cornerstone, real-time SAP threat detection, and establish what SecurityBridge calls Virtual Patching. This works best when both solutions are implemented on the same platform.
Virtual Patching protects affected SAP systems on “Patch Tuesday” or whenever SAP is releasing a critical SNote (so-called “Hot news”) until the patch is implemented, allowing administrators to follow their Patch Management processes without compromising security. Leveraging the SecurityBridge Cloud, customers not only immediately download the latest SAP patches but also receive an update for their Threat Detection configuration for the specific monitoring of vulnerable SAP code or components. Threat Detection MITIGATES RISK until the SAP Security Note can be deployed into the vulnerable environment.
In addition, a powerful Threat Detection solution can detect various anomalies and suspicious user activities, so regardless of the nature of the zero-day vulnerability, malicious activity will become visible. Effective protection of complex and dynamic SAP landscapes requires a comprehensive set of SAP Security sensors or listeners. These must aggregate data from all audit logs, enrich it with relevant contextual information from other SAP sources, and channel it into a detection model built natively within the SAP environment. This integrated approach is essential to ensure robust security.
SecurityBridge Threat Detection plays a crucial role here by transforming and correlating raw audit log data into insightful, actionable intelligence tailored for the appropriate audience. Notably, this audience isn’t always the SAP operations team. Global organizations have 24/7 SOC teams, but due to their limited SAP knowledge, SOC Teams need spot-on alerts, including mitigation guidance, for an effective and automated incident response process for SAP. SecurityBridge combines Threat Detection with HyperLogging technology that provides powerful investigation capabilities to uncover even sophisticated attack patterns in SAP environments.
Harden your SAP systems to minimize the impact
The success of cyber-attacks against SAP environments is also determined by the vulnerability and attack surface of the SAP systems. While Patch Management is responsible for implementing code fixes for known vulnerabilities in the SAP system code, SAP customers must also scan the ABAP code of their custom applications for potential exploits due to insecure programming.
Both topics feed into the fourth cornerstone of SAP Security, Vulnerability and Compliance Management, which ensures that the hundreds of parameters and settings that influence the hardening level of an SAP system are set according to SAP’s security recommendations and other best practices.
Zero-day vulnerabilities are, by definition, unknown until they are discovered and disclosed. However, a mature Vulnerability Management solution for SAP can support Threat Detection by pointing to potential exploits. A hardened SAP system is less susceptible to both known and unknown threats. System hardening involves minimizing the attack surface by disabling unnecessary services, enforcing strict configurations, and maintaining least privilege access.
SAP Security experts know how cumbersome it is to get the SAP system “clean”. Therefore, automating these Security & Compliance checks is a key success factor for SAP system hardening. SecurityBridge leverages a daily updated Security Roadmap for SAP with ranked findings based on a balance between exploitation risk and resolution complexity. Starting with the “low-hanging fruits” that have a high risk but can be mitigated easily, the roadmap also provides all the necessary details for an efficient Vulnerability Management process.
Conclusion
A resilient SAP security posture requires a holistic, integrated approach:
- Immediate patching closes known vulnerabilities before attackers can exploit them. Make it easy to prioritize patching with Patch Management from SecurityBridge
- Automated, real-time threat detection identifies and responds to both known and unknown threats, including those exploiting zero-days.
- Comprehensive system hardening minimizes the attack surface and limits the potential impact of successful exploits.
Organizations must proactively acknowledge that zero-day vulnerabilities are an ongoing reality and design their security strategies accordingly. By combining these pillars, SAP landscapes can achieve a sustainable level of cyber resilience, capable of withstanding both current and future threats.
Are you interested in exploring how adopting an All-in-One Security Platform for SAP can be the fastest and most efficient way to achieve a mature SAP Security posture?
Contact us and we will be happy to tell you more about our guided approach to SAP Security excellence. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!