Understanding SAP BTP: Why you need security for your SAP BTP

Chapters
Share Article
What is SAP BTP?
SAP Business Technology Platform (SAP BTP) is a comprehensive enterprise platform designed to empower businesses to build, extend, and integrate applications seamlessly. Acting as a central access point, SAP BTP provides architects, developers, and administrators with the tools they need to create and run enterprise-grade solutions. This cloud-based platform integrates data and business processes, enabling businesses to innovate and adapt in a secure cloud computing environment managed by SAP. By leveraging SAP BTP, organizations can streamline their operations, enhance their business processes, and drive digital transformation with confidence.
SAP Business Technology Platform: Why your business platform needs security of the same kind?
The recent global SAP user conferences have revealed one common trending topic: SAP Business Technology Platform (BTP), which integrates the former SAP Cloud Platform. SAP customers are about to adopt this platform for tailoring standard processes and creating integrations with their supply chains. We have covered this already in this article one year ago, highlighting how SAP BTP can seamlessly integrate SAP and non-SAP solutions both on-premise and in the cloud.
In 2021, SAP transitioned from the SAP Cloud Platform brand to SAP Business Technology Platform (BTP), consolidating various services to provide a unified solution for businesses.
However, SAP users also understand that a technology platform connecting businesses to the world can also potentially increase the surface of cyber-attacks. Therefore, to protect such a platform, security of the same kind is needed, in other words, a security platform.
Why is security for SAP solutions so challenging?
SAP BTP is an all-in-one, multi-cloud platform that masters seamless interfacing to the S/4HANA environment. It offers customers the flexibility they need for tailoring their business processes while minimizing upgrade efforts by decoupling custom development from the SAP Clean Core.
However, for a clean-core approach, SAP customers must share critical business data through the SAP Cloud Connector with SAP BTP Services in the cloud. These services are running in various technical environments, like Neo or Cloud Foundry, and the ABAP environment that ensures data security across all these technologies is quite challenging. The integration of AI and machine learning can help automate complex business processes, enhancing operational efficiency and allowing personnel to focus on more innovative activities.
A complex, multi-layered technology stack needs a security concept capable of handling this. The scope of this covers everything from ABAP code vulnerabilities to security audit logs and communication and infrastructure components. Ideally, all relevant information is gathered in one view and based on one coherent security platform.
Threats to SAP BTP Environments
While SAP BTP offers robust capabilities, it is not immune to security threats. Some common threats to SAP BTP environments include:
- Unauthorized Access: Hackers may attempt to gain unauthorized access to SAP BTP environments, potentially compromising sensitive data and disrupting business operations. This can lead to significant financial and reputational damage.
- Data Breaches: Vulnerabilities within SAP BTP environments can result in data breaches, exposing sensitive information and causing severe repercussions for businesses, including legal and regulatory consequences.
- Malware and Viruses: Malicious software can infiltrate SAP BTP environments, disrupting business operations and causing financial losses. These threats can compromise the integrity and availability of critical business applications.
- Denial of Service (DoS) Attacks: DoS attacks can overwhelm SAP BTP environments, rendering them unavailable to users and disrupting business operations. This can lead to significant downtime and loss of productivity.
Understanding these threats is crucial for businesses to implement effective security measures and protect their SAP BTP environments from potential risks.
How does the SecurityBridge Platform protects your SAP Integration Suite?
With the SecurityBridge Platform, you can manage the entire security for your SAP landscape, from on-premises systems to the cloud and SAP BTP. You gain insight into user activities and enforce secure configurations, development, and change management processes regardless of whether you use Cloud Foundry, ABAP, or Neo environments. The SAP Integration Suite facilitates seamless information exchange between on-premise solutions and cloud apps, supporting agile business process innovation.
Securing SAP BTP starts with an updated and configured SAP Cloud Connector, recommended BTP account settings, and user access management that follows the least privilege principle. Only users from trusted domains should have access to your BTP subaccount, and tenant and administrative privileges should be kept to a minimum. SecurityBridge Platform’s Security & Compliance module helps enforce these security measures and notifies you in case of obsolete users who should be deactivated to minimize the attack surface.
Ensuring a hardened SAP BTP environment must be complemented by end-to-end security monitoring. The Threat Detection module of the SecurityBridge Platform enables you to accomplish this task by gathering information from the various security audit logs of SAP BTP’s underlying environments and technologies. SAP users receive detailed descriptions of the events and the surrounding context of these activities on an easy-to-investigate timeline. The result is a fast and powerful threat detection process, which is vital for complex environments like SAP BTP.
But the SecurityBridge Threat Detection doesn’t stop on the application layer. It also includes the infrastructure layer by evaluating the SAP-specific IPS logs of your firewall. You can learn more about how SecurityBridge integrates with the FortiGate NextGen Firewall in our previous article here.
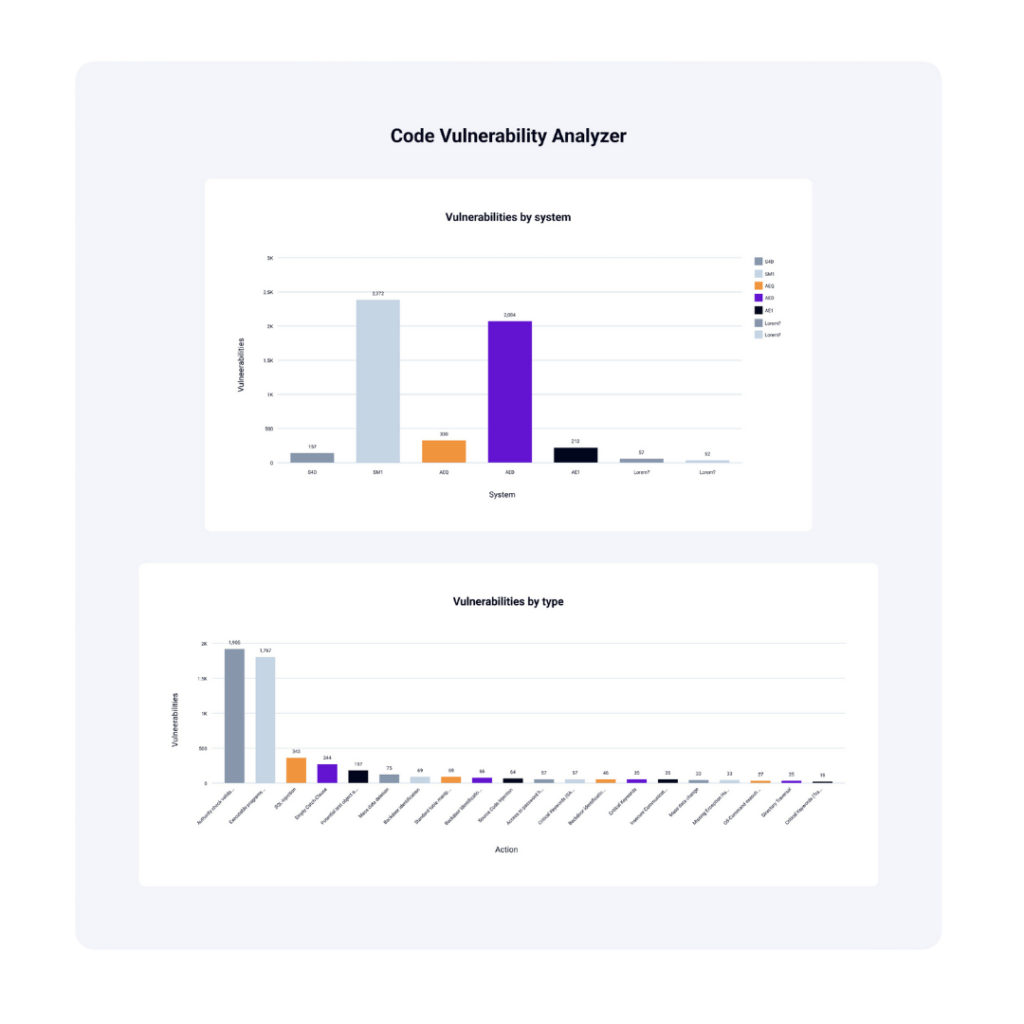
For SAP customers running ABAP applications on SAP BTP, we recommend extending their on-premise best practices for custom code development to the cloud and ensuring secure ABAP code with the Code Vulnerability Analyzer, also part of the SecurityBridge Platform. This analyzer supports both static code analysis and dynamic scans at code compilation, enabling development teams to follow SAP’s recommendations for secure ABAP coding. Learn more about the Code Vulnerability Analyzer here.
Best Practices for SAP BTP Security
To ensure the security of SAP BTP environments, businesses should adhere to the following best practices:
- Implementing Robust Access Controls: Utilize multi-factor authentication and role-based access control to prevent unauthorized access. Ensuring that only authorized users have access to critical systems and data is fundamental to maintaining security.
- Encrypting Data: Protect sensitive data by encrypting it both in transit and at rest. Encryption helps prevent unauthorized access and data breaches, safeguarding the integrity and confidentiality of business information.
- Regularly Updating and Patching: Keep SAP BTP environments up-to-date with the latest security patches and updates. Regular maintenance helps address vulnerabilities and ensures that the platform benefits from the latest security enhancements.
- Monitoring and Logging: Continuously monitor and log activities within SAP BTP environments to detect and respond to security incidents promptly. Effective monitoring helps identify suspicious activities and potential threats before they can cause significant harm.
- Implementing a Security Information and Event Management (SIEM) System: Deploy a SIEM system to collect, analyze, and correlate security-related data from SAP BTP environments. A SIEM system provides comprehensive visibility into security events and helps in the timely detection and response to incidents.
- Conducting Regular Security Audits: Perform regular security audits to identify vulnerabilities and ensure compliance with security policies and regulations. Audits help in assessing the effectiveness of security measures and identifying areas for improvement.
By following these best practices, businesses can enhance the security of their SAP BTP environments, protect sensitive data, and ensure the continuity of their business operations. Implementing these measures is essential for mitigating risks and maintaining a secure and resilient technology platform.
Summary
For a clean-core approach, SAP customers must share critical business data with SAP BTP Services in the cloud. As these services run in various technical environments, ensuring data security across all these technologies is challenging. A complex, multi-layered technology stack needs a security concept that can handle this, like the SecurityBridge Platform. The evolution from the SAP HANA Cloud Platform to SAP BTP illustrates the holistic approach to building an intelligent enterprise. The Security & Compliance module ensures an updated and configured SAP Cloud Connector, recommended BTP account settings, and user access management that follows the least privilege principle. In addition, it is crucial to monitor the SAP BTP security audit logs. The Threat Detection module of the SecurityBridge Platform gathers information from various security audit logs of SAP BTP’s underlying environments and technologies. SAP users receive detailed descriptions of the events and the surrounding context of these activities on an easy-to-investigate timeline. This allows a quick and powerful threat detection process. SAP customers running ABAP applications on SAP BTP can enable their development teams to follow SAP’s recommendations for secure ABAP coding with the Code Vulnerability Analyzer, also part of the SecurityBridge Platform.