SAP Business Technology Platform (SAP BTP) Security Considerations

Chapters
Share Article
Inspired by the many conversations we had at this year’s DSAG Annual Congress 2022, it is time to give some insights into the SAP BTP and its security considerations. As a software vendor with a core focus on SAP security, it is our job to look at the security concerns of new SAP technology. Our approach is to understand our customers’ concerns and integrate effective and efficient solutions into our cybersecurity solution for SAP. The SAP Business Technology Platform is the talk of the town and seems to be SAP’s new winning concept.
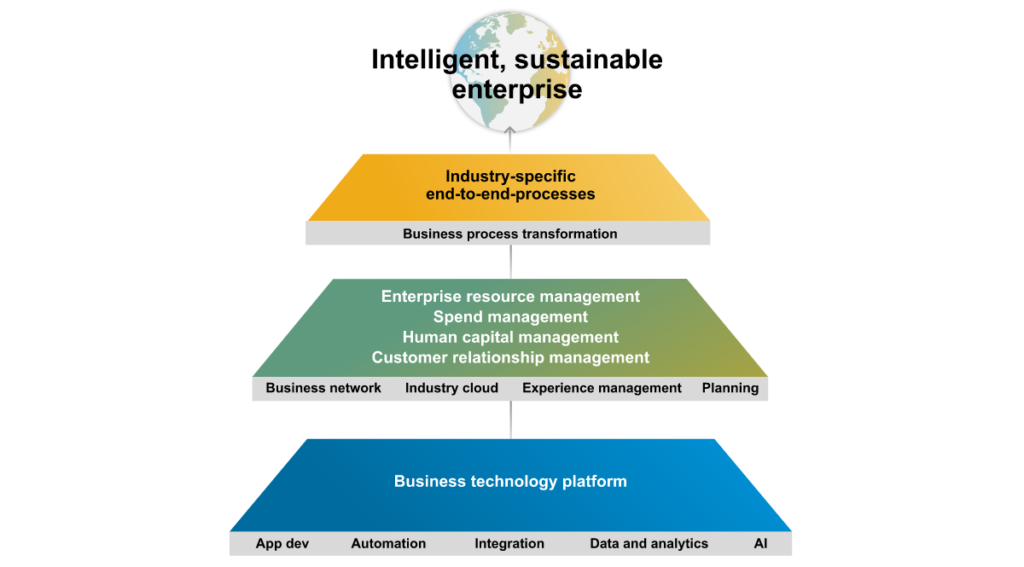
The SAP Business Technology Platform (BTP) plays a fundamental role in SAP’s strategy and represents a building block in the Intelligent, sustainable enterprise of the future. During my research, I came across the Intelligent Enterprise page. Here, the BTP is assigned the following areas: App Dev, Automation, Integration, Data and Analytics, and AI.
Of course, many readers know that SAP BTP is the evolution of the SAP Cloud Platform. However, things have also changed since the name change, and SAP BTP is now becoming a valuable tool in customers’ future SAP strategy.
What is SAP BTP?
SAP BTP is difficult to define, as it is more of an all-in-one, multi-cloud platform. Unfortunately, the above explanation is insufficient to consider the functions and more importantly, the security concerns of the new technology. SAP customers can access the various SAP Business Technology Platform services via the SAP Discovery Center. SAP CTO Jürgen Müller emphasized during his last presentation at the Technology Days 2022 of the German-speaking SAP User Group in Düsseldorf that the BTP particularly masters the seamless interfacing to the S4/HANA environment.
What is the SAP BTP used for?
So, before we think about security, we need to understand the implemented use cases in the customer context. In this conjunction, the term “Clean Core” often comes up. The “Clean Core” approach is nothing new and was declared a buzzword in 2021. However, it is now gaining relevance because SAP BTP offers customers the desired flexibility due to its proximity and simplicity.
The term “Clean Core” describes nothing more than the decoupling and implementation of custom code and customer-specific solution extensions with minimal dependencies on the S4/ECC solution. In theory, this solves the problem of upgrade efforts concerning refactoring custom developments.
In summary, the Business Technology Platform intends to carve out customer enhancements to introduce a clear separation to the S/4HANA product. This promises more flexibility and expandability and at the same time, targets to reduce the effort required for SAP upgrades.
Is security still in the hands of customers?
It is evident that when cloud and SaaS solutions are used, the provider manages much of the security activity. Customers often fall into the deceptive trap of thinking that the manufacturer is responsible for the consequences of a cyber incident. However, this is only partially true, as accountability often lies with the customer. The “Shared Responsibility Model” has often been advocated concerning Hyperscale, so it also applies to the use of SAP BTP, which also operates in the data centers of Google, Microsoft, AWS, and SAP. To fully implement a clean-core approach, the customer must share critical business data with BTP Services. This requires a certain level of trust, as customers can only gain insight into the technical processes to the extent that they can evaluate them via the audit service.
Insights via the Audit Log Service
Analogous to the SAP Security Audit Log available in S4/HANA, the SAP BTP also uses a central log that can be consumed and viewed via the Audit Log Service. We consider this a solid prerequisite for monitoring, so we have integrated BTP Audit Log Service into SecurityBridge Threat Detection.
What security precautions should customers take?
Before using SAP BTP, you considered whether your sensitive data could be processed on a multi-cloud platform. The next step is to think about data exchange and integration architecture, particularly encryption of data transfer, authentication, permissions, and identity management. Depending on the BTP service used, you will find (74, as of today) recommendations from SAP on the help page SAP BTP Security Recommendations.
SAP BTP: Integration & Architecture
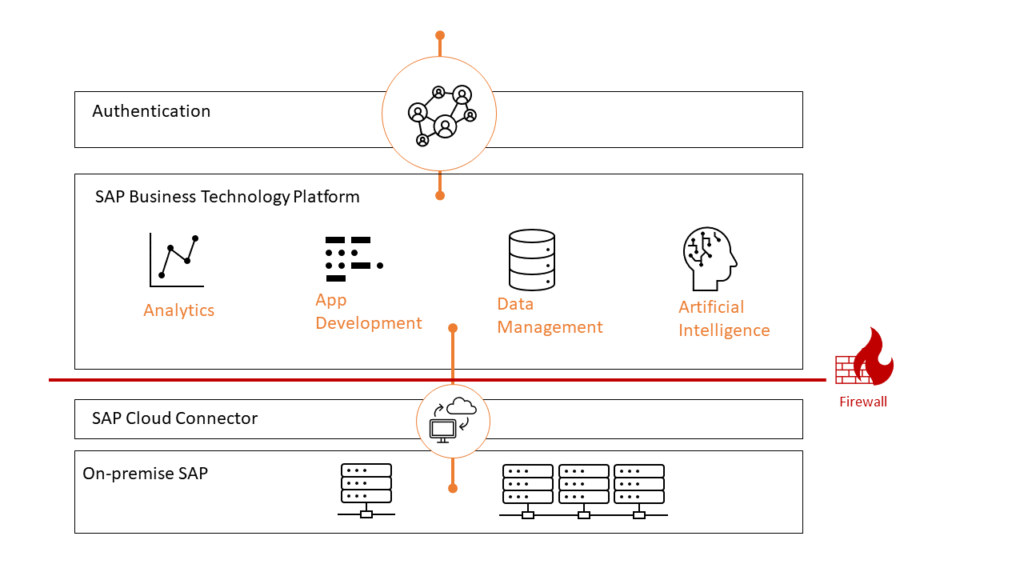
The entire data communication path in the integration architecture should be reviewed from a security perspective, in addition to considering which BTP services should be used and to what extent. Also, consider the secure configuration of the SAP Cloud Connector and bring experts from the network team on board to precisely set up the available firewalls. SecurityBridge monitors the hardening configuration of technical communication components such as SAP Cloud Connector and can even evaluate the SAP-specific IPS logs of the FortiGate NextGen Firewall. Read more about this integration on the SAP Attack Detection page.
SAP BTP: Development
The SAP Business Technology Platform provides ready-to-use services and enables access to new development environments. The available development environments are the following:
- SAP BTP, ABAP Environment
- SAP BTP, Cloud foundry runtime
- SAP BTP, Kyma runtime
Due to its diversity and flexibility, SAP BTP will become the first port of call for many deployment scenarios. At the same time, the need for governance and standardization will increase to comply with the security standards desired by the company.
Customers using the BTP development environments should think about how the quality and security requirements can be checked, e.g., in the BTP ABAP environment. We recommend a similar approach for ABAP/4 in the on-premises SAP environment and offer an integrated ABAP Code Vulnerability Analyzer as part of our SecurityBridge Platform.