
An Introduction to SAP Cloud Identity Governance
Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
SAP Cloud Identity Access Governance (IAG) enables organizations to manage user access and compliance effectively within SAP systems. It offers tools like Access Analysis, Role Design, and Access Request, which help ensure a secure and compliant SAP environment.
This article explains these core features and how they facilitate continuous identity management, monitoring, and audits to meet regulatory requirements.
Key Takeaways
SAP Cloud Identity Access Governance (IAG) facilitates user access management and compliance through features like Access Analysis, Role Design, and Access Requests, which are essential for securing SAP systems.
The platform includes a dashboard interface that enhances user experience and decision-making by providing real-time insights and analytics for effective access management.
With the addition of automated Privileged Access Management (PAM) from SecurityBridge, SAP Cloud IAG supports continuous compliance by reviewing and certifying access while mitigating risks associated with emergency access.
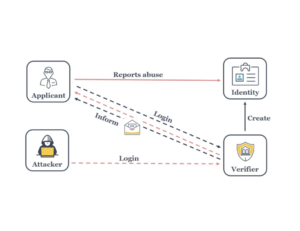
Understanding SAP Cloud Identity Access Governance
SAP Cloud Identity Access Governance (IAG) is a crucial tool for managing user access and maintaining compliance within SAP systems. It provides services like Access Analysis, Role Design, and Access Request, critical to a secure and compliant environment.
Proper configuration of master data, including business data, processes, and risks, is essential for maximizing these services.
SAP Cloud Identity stands out by facilitating continuous identity lifecycle management, monitoring, and audits. This overview allows organizations to meet regulatory requirements and adapt to changes. Features like real-time analytics and risk assessments enable businesses to address regulatory needs proactively.
Key Features of SAP Cloud Identity Access Governance
The Access Analysis component is a standout feature of SAP Cloud IAG. It offers real-time visualizations and analytics to streamline access management and ensure compliance.
Another key feature is the Role Design Service. It supports a role-based access control (RBAC) model, assigning access based on roles and responsibilities. Predefined access policies can be customized to meet specific business needs, ensuring alignment with organizational policies and risk management strategies.
The Access Request service completes the core features by offering robust SAP access control across various applications and devices. It enables efficient management of access requests and ensures that all access actions are tracked and audited.
Access Analysis in SAP Cloud IAG
Access Analysis in SAP Cloud IAG continuously evaluates access risks, allowing organizations to effectively manage user access. Real-time insights help maintain compliance across both on premise and cloud applications, aligning access permissions with business requirements.
Additionally, access analysis results can be directly linked to the role design process, optimizing governance and accurately defining roles and access rights. This integration helps maintain a compliant and secure access management system while ensuring thorough access risk analysis.
Dashboard-Driven Interface
The dashboard-driven interface of SAP Cloud Identity Access Governance enhances the user experience with personalized layouts and analytics capabilities. This interface facilitates accurate access assignments and prompt resolution of critical issues.
Users can create and analyze rules to mitigate access risks, ensuring potential violations are detected and managed effectively.
Utilizing dashboards allows organizations to monitor and manage access more efficiently, ensuring all access actions are transparent and traceable.
Role Design Service
The Role Design Service in SAP Cloud Identity Access Governance is focused on creating, optimizing, and maintaining business roles. It enhances the role design process by linking access analysis results to role definitions, ensuring alignment with corporate policies and risk management strategies.
The Role Design Service promotes consistent business roles across platforms through integrated reconciliation processes. Utilizing SAP Fiori-based tools and audit reporting functionalities streamlines the compliance management process, ensuring accurate definition and maintenance of all roles.
Streamlining Access Requests
The Access Request service in SAP Cloud Identity Access Governance offers a self-service capability that simplifies the process of request access to both on premise systems and cloud applications. It supports access requests for various systems, establishing transparent workflows and business rules to guide each stage of the process.
Detailed audit logs are maintained for all access actions, enhancing security and facilitating the provisioning and deprovisioning of approved access.
Automating Access Certification
The access certification service in SAP Cloud Identity Access Governance periodically reviews and certifies user access to cloud and on premise systems. It automates the review of access permissions, ensuring alignment with regulatory requirements and organizational policies, including SAP access control.
The access certification service enhances decision-making and ensures comprehensive governance by providing data-driven views of the review process. It supports various scales of reviews, allowing organizations to tailor the certification process to their specific needs.
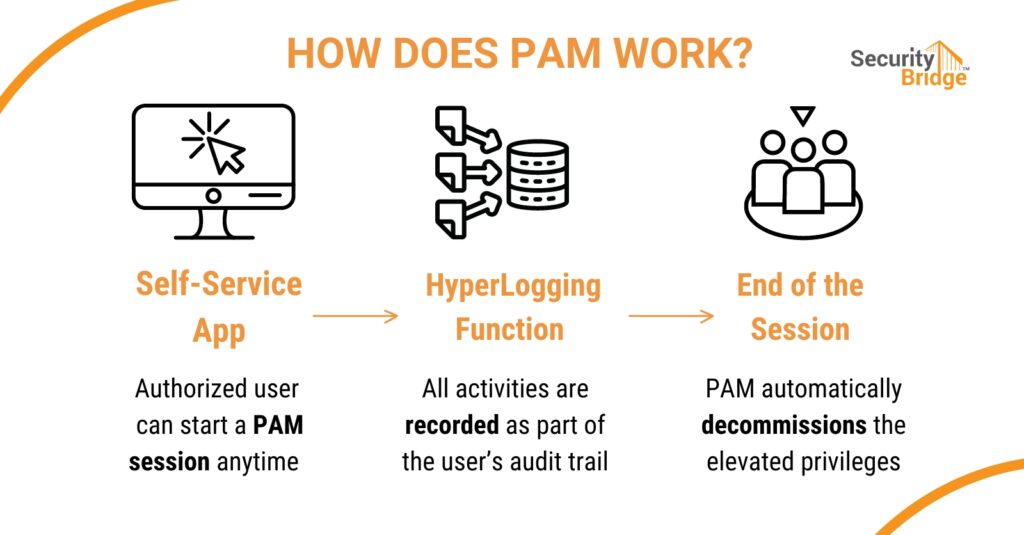
Managing Emergency Access with PAM
SecurityBridge’s Privileged Access Management (PAM) is essential for regulatory adherence and mitigating risks associated with emergency access. PAM thoroughly assesses access and usage patterns, providing a secure framework for managing critical access situations.
Users can independently request emergency access, ensuring immediate action when standard processes fail. Afterward, the security team can audit usage and logs, ensuring accountability and adherence to access policies.
Integration Scenarios
SAP Cloud Identity Access Governance is a cloud-based service within the SAP Business Technology Platform (BTP) that integrates seamlessly with other SAP solutions. This integration efficiently manages user identities and access rights through identity and access management.
SAP Identity Authentication Service (IAS) provides end-to-end authentication without disruption, ensuring a smooth and secure user experience.
Compliance Practices
Detailed reporting on access request activities is fundamental to compliance management in SAP IAG. The solution ensures traceability of all SAP access control activities, helping organizations meet regulatory standards.
Predefined access policies and rules aid in managing SAP access control processes effectively. Configurable policies streamline the process, ensuring consistency with internal and external regulations.
SecurityBridge’s Privileged Access Management (PAM) mitigates risks such as fraud by enabling regular access reviews and implementing effective access control processes to enable robust privileged access management.
xr:d:DAFyvx4RAak:110,j:9161859694151136980,t:23121309
Benefits of SAP Cloud Identity Access Governance
SAP Cloud Identity Access Governance offers significant benefits, including enhanced security and increased efficiency. Integrating various identity access governance functions helps organizations safeguard data integrity and streamline operations.
The adaptive and scalable capabilities of SAP Cloud IAG ensure maintenance-free updates and responsiveness to changing user needs.
Summary
In summary, SAP Cloud Identity Access Governance provides a comprehensive solution for managing user access and ensuring compliance within SAP systems.
Leveraging features like access analysis, role design, and access request can help organizations optimize their access management processes and mitigate risks.
Adopting SAP Cloud IAG enhances security and efficiency and ensures that businesses remain compliant with evolving regulations. Additionally, adding a solution like SecurityBridge’s Privileged Access Management (PAM) is a strategic move towards a secure and compliant future.
Frequently Asked Questions
What is SAP Identity and Authorization?
SAP Identity and Authorization refers to a comprehensive suite of tools and processes designed to manage user and application access rights within the SAP environment. This management is crucial for maintaining security and compliance and ensuring adherence to internal policies and external regulations.
What are the primary services provided by SAP Cloud Identity Access Governance?
SAP Cloud Identity Access Governance primarily offers Access Analysis, Role Design, and Access Request services, essential for effective user access management.
How does the Access Certification service benefit organizations?
The Access Certification service enhances organizational governance by automating periodic reviews of user access permissions, thereby facilitating informed decision-making across SAP cloud and on premise applications.
What is the role of Privileged Access Management (PAM) in SAP Cloud IAG?
Privileged Access Management (PAM) plays a crucial role in SAP Cloud IAG by ensuring regulatory adherence and mitigating risks related to emergency access. It provides a secure framework for effectively managing critical access situations.
How does SAP Cloud IAG integrate with other SAP solutions?
SAP Cloud IAG effectively integrates with other SAP solutions by leveraging the SAP Business Technology Platform and connecting with the SAP Identity Authentication Service (IAS) for streamlined user identity and access management. This integration enhances security and ensures efficient user permissions management across SAP applications.
