SAP Governance, Risk, Compliance (GRC): What is it?

Chapters
Share Article
SAP GRC stands for Governance, Risk, and Compliance and essentially describes an SAP product’s business processes and the product itself. Many organizations seek SAP GRC experts and jobs, which are therefore in high demand.
In this article, we explore the relevance of SAP GRC in the context of the necessary measures for robust cybersecurity.
Definition and Overview
SAP Governance, Risk, and Compliance (GRC) is a robust suite of solutions designed to enable organizations to manage their enterprise resources effectively. It includes modules such as SAP Access Control, SAP Process Control, SAP Risk Management, Audit Management, Fraud Management, and Global Trade Services (GTS).
The framework enables organizations to identify, assess, and mitigate risks, enforce internal controls, and monitor compliance procedures. As a critical component of SAP’s risk and compliance strategy, SAP GRC aims to reduce the cost of enterprise application risk management while ensuring that businesses can operate smoothly and securely.
SAP GRC as a Critical Component of the Risk Management Strategy
SAP Governance, Risk and Compliance is a crucial component of a comprehensive risk management strategy. It enables organizations to identify, assess, and mitigate risks across their operations.
By integrating GRC activities, SAP provides a unified platform for managing risk and ensuring regulatory compliance.
This approach helps organizations to reduce the risk of non-compliance, improve operational efficiency, and enhance their overall risk management posture.
The Main Components of SAP GRC
SAP GRC comprises three key components: Governance, Risk Management, and Compliance Management. Each component is critical in ensuring an organization’s GRC efforts are effective and aligned with its overall business objectives.
By integrating these three components, SAP GRC provides a comprehensive platform to manage risk and ensure regulatory compliance. This approach helps organizations to reduce the risk of non-compliance, improve operational efficiency, and enhance their overall risk management posture
Governance: Ensuring Accountability and Transparency
Governance is the foundation of SAP GRC, providing a framework for ensuring accountability and transparency across an organization.
This component involves establishing clear policies, procedures, and controls to govern an organization’s operations and ensure they align with its overall business objectives.
Governance also involves ensuring that an organization’s leadership is accountable for its actions and that adequate reporting and disclosure mechanisms are in place.
Risk Management: Identifying and Mitigating Risks
Risk Management is a critical component of SAP GRC, enabling organizations to identify, assess, and monitor risks across their operations.
This component uses a risk-based approach to identify potential risks, assess their likelihood and impact, and implement controls to mitigate or manage them.
The component also enables monitoring and reviewing capabilities to ensure that risks are appropriately managed and controls are adequate.
Compliance Management: adhering to laws and standards
Compliance Management is the third component of SAP GRC, ensuring that an organization adheres to relevant laws, regulations, and standards.
This component involves identifying and assessing compliance requirements, implementing controls to ensure compliance, and monitoring and reporting compliance activities.
Compliance Management also ensures that an organization’s compliance activities align with its overall business objectives and that adequate reporting and disclosure mechanisms are in place.
What are the SAP GRC modules?
There are multiple modules represented in the SAP product. The most used SAP GRC modules are:
SAP GRC Access Control
SAP GRC Access Control and management are pivotal aspects of SAP GRC. SAP Access Control is essential for identifying and preventing organizational access and authorization risks. It supports user lifecycle processes from hire to retirement, reducing compliance and control procedures costs and enhancing access governance.
The tool provides a workflow-based model for managing access data requests, allowing customization to meet organizational needs within access governance.
SAP GRC Access Control automatically logs roles and authorizations when access requests are approved and perform compliance checks to identify potential threats to monitor emergency access sessions. Key features include Emergency Access Management, Access Risk Analysis, and Business Role Management, designed to enhance access governance and ensure robust identity and access management.
SAP GRC Process Control
SAP Process Control is software designed to manage compliance and internal control processes. It enables continuous monitoring of controls across business processes, ensuring compliance with regulatory requirements and internal policies.
Key features include control design and assessment, automated control testing, and issue management. SAP Process Control provides real-time visibility into control effectiveness, allowing organizations to quickly identify and address potential risks.
This module integrates with other SAP systems, providing a unified approach to corporate governance and compliance.
Governance and Risk Management
Governance involves establishing frameworks, rules, and policies to achieve business goals and objectives.
At the same time, it is a crucial module for identifying, analyzing, and continuously monitor risks, providing detailed insights into risk factors and their impacts on operations and business reputation.
SAP offers a unified technology platform that coordinates GRC efforts. This integration helps organizations reduce business risks, improve efficiency, and comply with industry and government regulations.
Audit Management
SAP Audit Management is a fully integrated solution that enhances internal and external audits by simplifying activities such as documenting evidence, organizing electronic working papers, and generating audit reports for external and internal auditors.
It protects data, assets, and reputations by implementing an effective risk management system.
SAP Fraud Management
Fraud management aims to detect and prevent fraud across internal processes and external partnerships.
SAP Fraud Management focuses on SAP customer-related risks using tools like SAP Business Integrity Screening. Governance, Risk, and Compliance (GRC) teams typically manage fraud using fraud controls and data analysis strategies.
Tools in this area centralize risk data, automate screening, and integrate with broader GRC efforts.
SAP Global Trade Services
SAP Global Trade Services helps businesses streamline and automate their global trade processes, improving efficiency and compliance with international regulations.
The platform centralizes compliance data, supports import and export management, and offers real-time compliance checks. Key features include sanctioned party list screening, management of free trade agreements, and support for special customs procedures.
International Trade Management
SAP solutions empower organizations to conduct trade in evolving markets with greater confidence and agility, maximizing the potential of trade strategies and partnerships.
Recognized by ARC Advisory Group as a market share leader in global trade compliance solutions, SAP Global Trade Services centrally manages trade compliance based on regulatory requirements, geopolitical risks, and market opportunities. This ensures that organizations can navigate complex global trade regulations and maintain compliance, enhancing their ability to manage risk and capitalize on international business opportunities all within the SAP system.
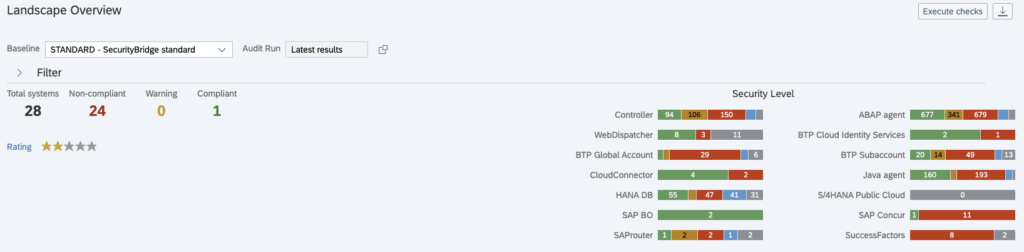
What is the need for SAP GRC in risk management?
SAP Risk Management is a crucial module for identifying, analyzing, and continuously monitoring risks. It provides detailed insights into risk factors and their impacts on operations and business reputation, enabling organizations to manage compliance processes and minimizes risk in business processes.
This functionality does not necessarily focus on cybersecurity. SAP Governance, Risk, and Compliance is more about managing business risks, such as helping organizations enhance cross-border supply within the limits of international trade management.
Automate for Efficiency
Automation minimizes risks, improves security management, streamlines processes by minimizing manual intervention, enhances operational efficiency, and reduces compliance costs.
Continuous risk monitoring is crucial to improving internal controls and ensuring compliance with corporate governance requirements. Through these capabilities, SAP supports organizations in maintaining robust GRC frameworks. Maintaining compliance through evaluations of workflows and configurations is essential to managing corporate governance risks effectively.
Benefits of SAP Governance, Risk and Compliance (GRC)
By providing a comprehensive approach to enterprise risk management, SAP GRC offers integrated platforms and applications for ensuring compliance, reducing the risk of fraud, and improving decision-making by providing real-time insights into potential risks. The SAP GRC framework also streamlines audit processes and increases transparency across to avoid organizational silos, allowing for seamless risk and compliance processes across all business operations.
GRC and SAP Security
SAP has already recognized that compliance and risk concerns alone are insufficient to address internal and external threats, emphasizing the need for improved SAP cybersecurity in addition to GRC software. The following topics also always come into play here:
Real-time threat detection and anomaly detection
Secure configuration
Timely patching
All of them become the focus of attention to address cybersecurity threats. Digital enterprises today need to close the existing gap for cybersecurity and data protection in their current business processes.
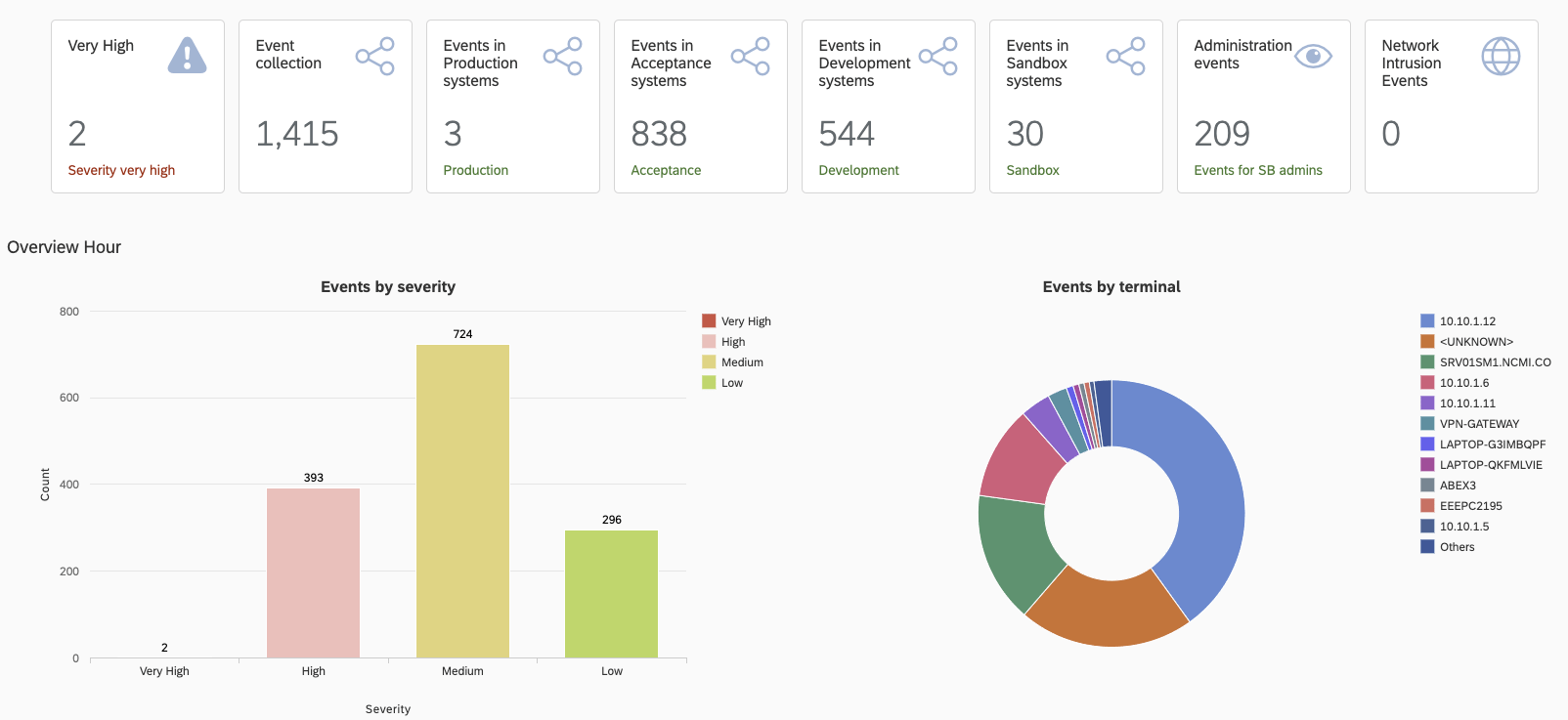
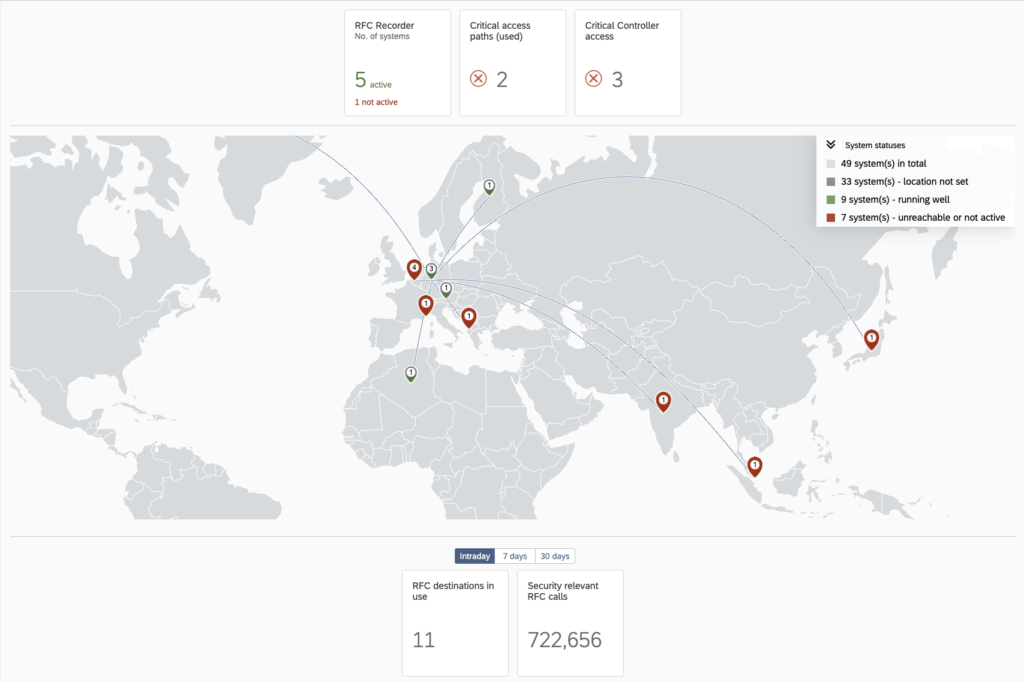
Is SAP Enterprise Threat Detection (ETD) Enough?
While SAP Enterprise Threat Detection is a critical module to identify threats and address security threats within IT systems, it lacks proactive security capabilities properly protect SAP environments.
In addition to SAP Enterprise Threat Detection, organizations need intelligent, automated, and embedded event management and analysis of data for complete security in their SAP solutions
Identity and Access Management
With the increasingly complex environments of IT systems, safeguarding sensitive data, maintaining compliance, and reducing risk drivers have become more challenging than ever. This is where SAP Access Control Lists (ACLs) can play a vital role in bolstering technical SAP security. Additionally, user access management is crucial in streamlining processes within a SAP system, automating user provisioning, and managing privileged access.
To Conclude - Governance Risk and Compliance in Evolution
The software solution and the associated processes are necessary, especially when high risk businesses are active in international trade, but also otherwise. Some time ago, SAP rearranged the building blocks in the GRC area on its website and has now introduced the following main areas:
Enterprise Risk and Compliance
International Trade Management
Identity and Access Governance
Cybersecurity, Data Protection, and Privacy
This seems logical because cyber threats continue to evolve, becoming more intense and increasingly successful in reaching critical applications and sensitive data – even among seemingly security-conscious organizations.
Now that many companies, maybe including yours, are undergoing a digital transformation or are planning to migrate to S/4HANA, we encourage you to add cybersecurity to your existing SAP GRC framework and rethink it to build a secure foundation.
Ready to secure your SAP landscape? Contact us today for a personalized assessment.