Time is of the essence when preventing and detecting SAP cybersecurity attacks

Share Article
This article outlines key SAP systems vulnerabilities, emphasizing the importance of timely prevention and detection for mitigating SAP cybersecurity attacks.
The sooner you catch an intruder in your network, the better. Attackers can stay undetected in your network for weeks to months, even more than half a year according to this recent IBM research. The longer attackers remain undetected, the more damage is done, since they can penetrate deeper into the network and the risk of data theft and extraction of sensitive data increases.
The same applies to your SAP applications. The longer an attacker has access to your business-critical SAP systems, the more SAP systems can be infiltrated, and more business-sensitive data can be extracted.
Time is of the essence here. Two factors are related to the factor of time:
- The harder it is initially to penetrate an SAP system, the longer it takes to do so. This might have opportunistic attackers move next door.
- The sooner you detect malicious activity, the bigger the chance of catching this and minimising further damage.
When zooming in on the first item, we see in our SAP penetration testing and SAP security assessments these typical blind spots, leaving SAP systems vulnerable to exploitation. Some typical ones are:
- Missing critical SAP Security patches
- Insecure default values for parameters
- Existence of default accounts with default passwords
- Insecure Access Control Lists around critical components
- Insecure connections between SAP systems
- SAP Secure store with default encryption key
- Old and insecure password hashes
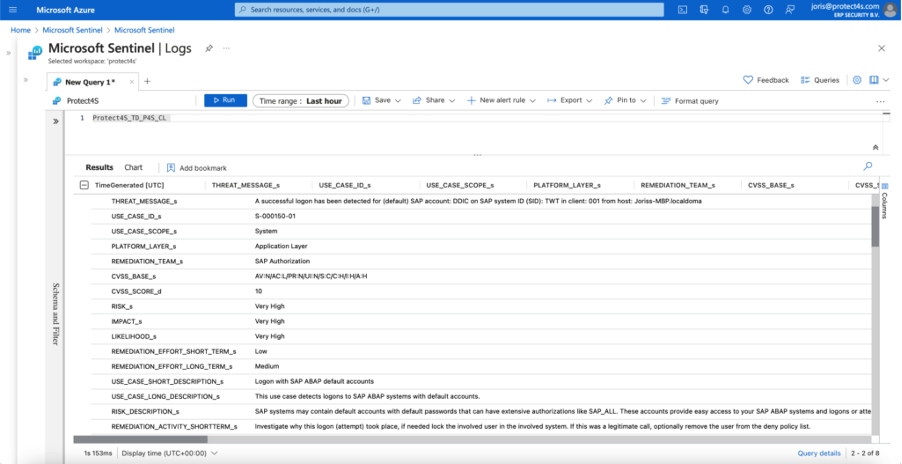
These vulnerabilities can be exploited to gain access or move between SAP systems too easily. For example, when attackers use default accounts to login to your SAP systems as in the example below:
The above is just an easy example, however not properly addressing the above-mentioned vulnerabilities via a Vulnerability Management process, can leave your SAP systems prone to exploitation. This underlines the need for a last line of defence, specifically aimed at your SAP applications.
Making it harder to exploit your SAP systems is an important first step, but there is more. The best defence cannot 100% avoid security incidents. If an attacker still manages to gain access to your systems, it is important to reduce the time spent in your systems to minimize the damage done. The SecurityBridge Event Monitoring solution does exactly that. By reading the log data sources of connected monitored systems and extracting potential threats from a constant stream of events. Only qualified threats are sent to SIEM solutions in a Secure Operation Centre for further follow-up by an analyst. These threats contain the underlying event, enriched with additional technical data and more information to enable direct containment, but also to help prevent similar threats in the future.
To summarise: To keep your business-critical SAP systems as secure as possible and minimize risk, two activities are important – Prevention and Detection. Make it harder for attackers to initially gain access to your SAP systems and have a mechanism in place that if they still do, you detect them as soon as possible to minimize risk and damage done.
The SecurityBridge Security & Compliance and Event Monitoring solutions complement each other perfectly for this purpose.
Interested to learn more? We are happy to tell you more about SecurityBridge’s capabilities. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!