Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
As we know, SAP (Systems, Applications, and Products in Data Processing) is a widely used enterprise resource planning (ERP) software suite that helps organizations manage various business operations. No digital system is secure by nature or by default – there will always be security challenges, and SAP is no exception.
In this article, we discuss the Top 10 vulnerabilities in SAP – how they affect the security of an SAP system, and finally, how to identify and manage them with SecurityBridge.
1. Incomplete Patch Management:
Patching is one of the most significant tasks and security concerns in SAP. Patches, or “SAP Security Notes” (that are, in general, released every 2nd Tuesday of the month) often contain critical security fixes that address vulnerabilities. Failing to apply these patches promptly can leave systems vulnerable to known exploits, as cybercriminals often target systems with known vulnerabilities.
2. Default Credentials:
One of the most prevalent SAP security issues is the use of default or weak passwords. SAP systems often come with default usernames and passwords that are well-known. If organizations do not change these defaults or enforce strong password policies, it becomes relatively easy for attackers to gain access or escalate privileges.
3. Inadequate User Authorization controls:
Role-based access control (RBAC) is crucial in SAP systems, but many organizations struggle with proper role and authorization management, with poorly managed user access being a common issue. Organizations must implement robust role-based access controls (RBAC) to ensure that users have only the permissions necessary for their roles. In fact, failing to do so can lead to data breaches and unauthorized activities. Overly permissive roles or insufficient segregation of duties (SoD) can lead to unauthorized access and fraud – conversely, overly restrictive roles can hinder productivity.
4. Unsecured Interfaces:
SAP systems often have multiple interfaces for communication, including RFC (Remote Function Call) and HTTP. Attackers can exploit inadequately secured interfaces to access and manipulate SAP data or move easily between SAP systems and compromise the entire landscape. There are several ways to secure the interfaces, for example, by avoiding passwords by configuring trust between systems or by using UCON functionality of SAP to lower the attack surface drastically. Another measure is to enable data encryption, as it is essential for protecting sensitive information both at rest and in transit: without proper encryption measures, data can be exposed to eavesdropping and theft.
5. Inadequate Authentication:
Weak authentication mechanisms, such as: simple passwords and insufficient authorization checks, can result in unauthorized access and privilege escalation. Organizations should implement multi-factor authentication (MFA) and regularly review and update authentication policies. When it comes to SAP, enforcing Single Sign-on greatly reduces the attack surface and the password reset effort by the teams.
6. Insecure Custom Code:
Again, no digital system is perfect and the custom-developed code within SAP environments can introduce security vulnerabilities. Organizations must enforce regular code reviews and security testing to identify and remediate issues in custom code.
7. Poorly Managed Security Logs:
Many organizations still do not activate SAP Security Audit Log in their systems, which leaves a huge gap in terms of incident investigation. Proper logging and monitoring are essential for detecting and responding to security incidents. Inadequate or misconfigured logging can make it challenging to identify suspicious activities or breaches. Organizations need to establish robust monitoring and alerting systems to stay vigilant against potential threats.
8. Configuration errors and leaving settings on insecure defaults:
Misconfigured SAP systems can expose sensitive data and functionality to unauthorized users. This includes incorrect or overly permissive settings / parameters for database and application servers, network configurations, SAP components like Message Server, RFC Gateway and the ICM, and user authorizations. Configuration errors are often the result of human oversight or lack of expertise. Hence, 4-eye principle must be applied wherever possible, while performing configurations.
9. Lack of Security Awareness:
Employees and users can inadvertently introduce security risks through actions like social engineering or falling victim to phishing attacks; regular security training and awareness programs are essential to mitigate this risk.
10. Obsolete and Unsupported Systems:
Running outdated or unsupported SAP systems, Operating systems, and Databases can be a significant security risk. These infrastructures are more likely to have known vulnerabilities that attackers can exploit. If an SAP system is decommissioned, proper steps must be taken to ensure that all users are locked out, and the data is deleted to prevent unwanted data usage; sometimes, even decommissioned systems may contain sensitive business data.
In conclusion, SAP security and proper configuration management are critical concerns for organizations due to the sensitive nature of the data managed within SAP systems and how business-critical they are. To mitigate these top 10 security issues, organizations should establish a comprehensive SAP security strategy that includes regular patch management, robust access controls, secure custom code development, and ongoing user training. Organizations should stay informed about the latest SAP security vulnerabilities and best practices to adapt their security measures accordingly. Addressing these security challenges is essential to safeguard the CIA triad (Confidentiality, Integrity, and Availability) of SAP systems and the information they contain.
Additionally, organizations may consider using specialized SAP security tools such as SecurityBridge, the all-in-one SAP Security platform that has innate functionalities to effectively identify and manage all the above listed vulnerabilities in SAP systems.
The Security Bridge Threat Detection module identifies the incidents happening in SAP in almost real-time and alerts the relevant teams for further analysis and investigation.
The Security & Compliance module effectively shows the data of various vulnerabilities in the SAP systems regarding authorizations, authentication, and security configurations/parameters.
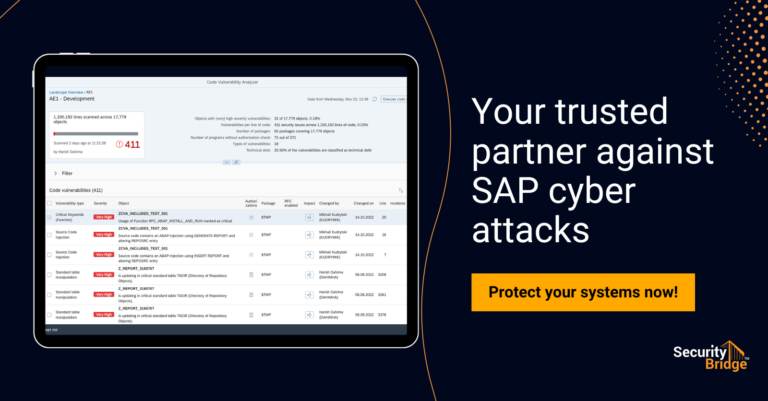
The Code Vulnerability Analyser can scan the custom code, while the SecurityBridge Patch Management application can effectively manage the crucial task of Patching. Do you want to learn more about our platform? Feel free to request a Proof of Concept or contact us for a demo anytime.