
Chapters
Share Article
Ensuring the security of SAP code is critical to protect your business from cyber threats. This article will explore essential tools and practices for enhancing code security. You will learn about methods to detect vulnerabilities, perform thorough code reviews, and integrate the necessary checks into your development workflow. Let’s dive into securing your SAP applications effectively.
Key Takeaways
Understanding and implementing SAP code security is critical for protecting business operations from unauthorized access and cyberattacks.
Utilizing tools like the Code Vulnerability Analyzer from SecurityBridge enhances security by identifying vulnerabilities and enforcing secure coding practices within the development workflow.
Regular system updates and integration of security checks throughout the development lifecycle are essential for maintaining SAP code security and compliance.
Understanding SAP Code Security
Securing SAP systems encompasses various facets, including infrastructure, network, operating system, and database, alongside secure development practices. A significant component of this framework is monitoring SAP authorizations and access controls to prevent internal and external threats. SAP Developers play a crucial role in this ecosystem by ensuring the integrity of ABAP code. However, without thorough inspections, vulnerabilities in the ABAP code may go unnoticed, making the system vulnerable to attacks.
A robust code security strategy involves multiple layers, including regular code reviews, secure development practices, and specialized solutions for detecting vulnerabilities early. Integrating these practices into the development lifecycle helps safeguard SAP environments and maintain operational integrity.
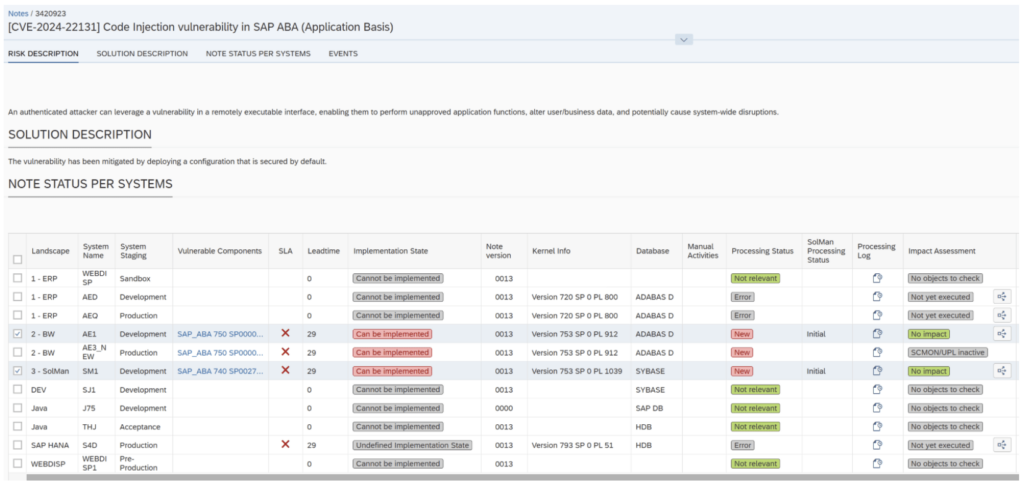
Key Features of SAP Code Inspector (SAP CI)
The SAP CI is a powerful tool designed to enhance the performance of SAP products. It enables checking repository objects for performance issues, vulnerabilities, errors, and adherence to naming conventions. Unlike a regular syntax check, the SAP CI provides a comprehensive analysis beyond surface-level errors, offering a deeper insight into the code’s health.
Integrating the SecurityBridge Code Vulnerability Analyzer (CVA) with the Code Inspector enhances ABAP Test Cockpit’s capabilities. This combination allows static analysis of ABAP source code to detect issues, providing an extra layer of protection.
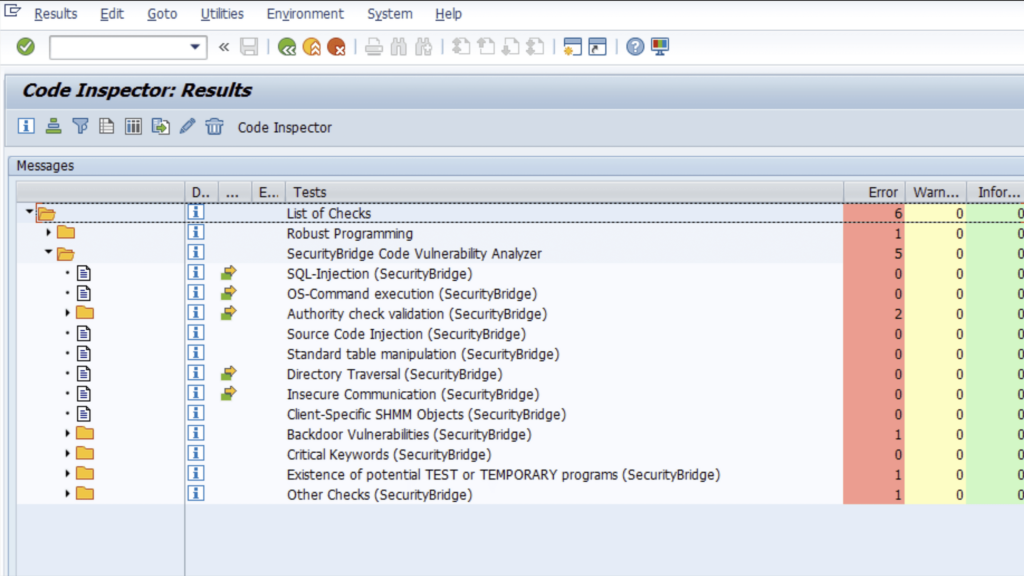
Leveraging ABAP Test Cockpit
The ABAP Test Cockpit (ATC) is another tool for enhancing code security for SAP Business Suite, SAP NetWeaver, and SAP S/4HANA. It allows for the execution of comprehensive checks across ABAP programs, identifying and mitigating potential vulnerabilities. The ATC improves efficiency by allowing automatic mass runs of checks, enabling SAP developers to scan multiple objects simultaneously and identify issues quickly. Analysis within the ABAP Test Cockpit can highlight various risks, including SQL injection and unauthorized access, before they reach production.
Integrating the ATC into the development workflow ensures that cybersecurity remains a continuous process.
Analyzing Results from Inspections
Analyzing the results from inspections is a critical step in enhancing code security. Security audits, including source code reviews and application penetration tests, are essential for identifying vulnerabilities in SAP custom code. These audits help in uncovering weaknesses that could be exploited by malicious actors, thereby providing a roadmap for remediation.
It is also necessary to regularly review older Fiori developments for vulnerabilities, as once-secure components may become outdated and be exposed to threats.
Identifying vulnerabilities early in the development process is crucial. It minimizes potential damage and reduces long-term costs. The SAP CI and ABAP Test Cockpit allow developers to perform ad hoc inspections and detailed analysis, ensuring their code is robust.
Integrating Security Checks into Development Workflow
Integrating checks into the development workflow is essential for maintaining a secure SAP environment. A tool like the SecurityBridge Code Vulnerability Analyzer (CVA) plays a crucial role in this integration, embedding cybersecurity measures directly into the development lifecycle.
SecurityBridge’s CVA integrates directly with ABAP Workbench and SAP NetWeaver to support seamless security checks and create a secure-development culture within the environment.
Advanced Cybersecurity Measures for Custom Code
Advanced cybersecurity measures are critical for safeguarding code in SAP products. These customized checks can be tailored to address unique requirements, ensuring the code meets the highest standards.
By using the SecurityBridge’s CVA functionality in Code Inspector, SAP developers can perform a detailed custom code analysis, identifying potential issues before they become critical. The extended program check feature provides an in-depth review of the code, highlighting areas that need improvement.
Implementing these advanced measures ensures that the code is functional and secure, mitigates risks, and maintains the integrity of the SAP system.
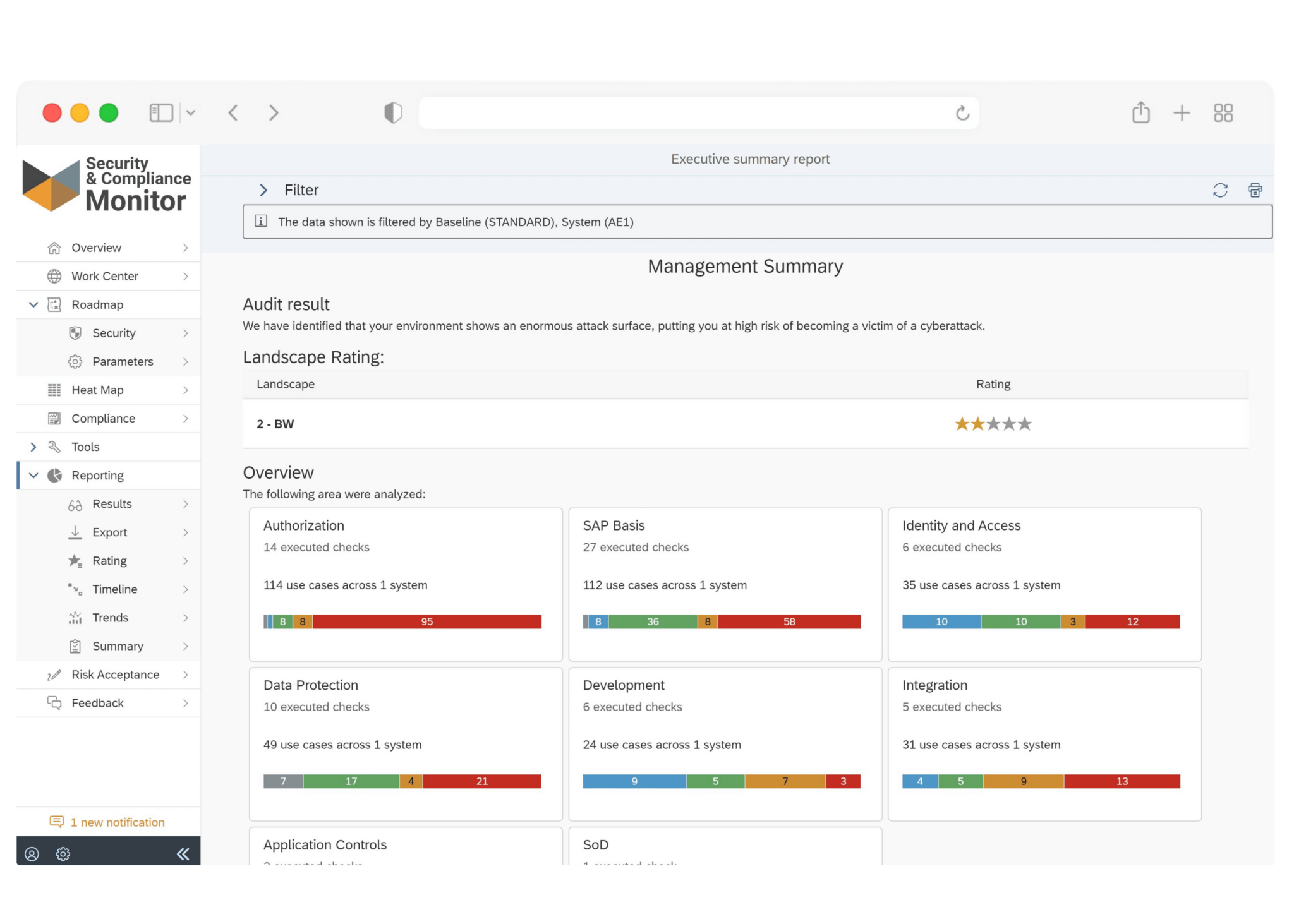
Common Pitfalls and How to Avoid Them
Common vulnerabilities in SAP custom code include SQL injections, cross-site scripting, and broken access control. Broken access control can lead to unauthorized information access, often due to insufficient authorization checks in ABAP programming.
Dynamic SQL statements in ABAP can also pose risks, but the SecurityBridge CVA in ABAP Test Cockpit provides methods to validate and secure user inputs before execution.
A robust software development lifecycle (SDL) is vital for managing custom code safely. It allows tracking of development objects from planning through maintenance. Auditing and logging are essential to detect suspicious changes in custom applications, contributing to proactive SAP security processes.
Staying Updated with New Versions and Updates
Creating and managing Check Variants is essential. By defining and executing these variants, SAP developers can ensure their custom code adheres to the latest cybersecurity standards. This proactive approach helps identify and address potential issues, including the default variant before they become critical.
Staying current with new versions and updates ensures that SAP systems remain secure and compliant. This continuous improvement process helps maintain a robust security posture and protects sensitive data from cyber threats.
Summary
In conclusion, SAP code security is a multifaceted process that involves using powerful tools like the Code Inspector and ABAP Test Cockpit in combination with SecurityBridge’s Code Vulnerability Analyzer, integrating cybersecurity checks into the development workflow, and implementing advanced measures for custom code. By staying updated with new versions and understanding common pitfalls, the SAP developer can ensure that their systems remain secure and compliant without error. Prioritizing cybersecurity is essential for protecting sensitive data and maintaining the integrity of business operations.
Frequently Asked Questions
What is the importance of SAP code security?
Code security is essential for safeguarding sensitive business operations and data against unauthorized access and attacks, thereby preventing financial loss and preserving the organization’s reputation.
How does the SAP Code Inspector (SAP CI) help enhance code security?
The Code Inspector secures code by evaluating repository objects for vulnerabilities and performance issues. It offers detailed feedback that enables SAP developers to address critical vulnerabilities effectively. However, the Code Inspector only covers a few cybersecurity checks, which isn’t sufficient for most organizations.
What are the benefits of using the ABAP Test Cockpit for security checks?
The ABAP Test Cockpit identifies vulnerabilities such as SQL injection and unauthorized access while also generating reports that facilitate tracking and code corrections. Adding the SecurityBridge Code Vulnerability Analyzer empowers a proactive approach to ensuring the integrity of your ABAP programs.
How can SAP developers integrate security checks into their development workflow?
Integrating checks into the development workflow can be achieved by utilizing tools such as the ABAP Workbench and SAP NetWeaver with SecurityBridge, which embed cybersecurity measures directly within the SAP development lifecycle. This approach fosters a culture of security while enhancing coding efficiency through features like one-click fixes.
Why is it important to stay updated with new versions and updates in SAP systems?
It is essential to stay updated with new versions and updates in SAP systems to mitigate security vulnerabilities and ensure the latest security patches and features are implemented. This practice protects sensitive data from cyber threats and maintains a robust security posture.
How to Handle Legacy Code in SAP?
Dealing with legacy code in SAP can be a challenging task for developers. Legacy code often contains outdated practices and vulnerabilities that can pose significant security risks. To master SAP code vulnerabilities in legacy code, developers should focus on several key areas.
