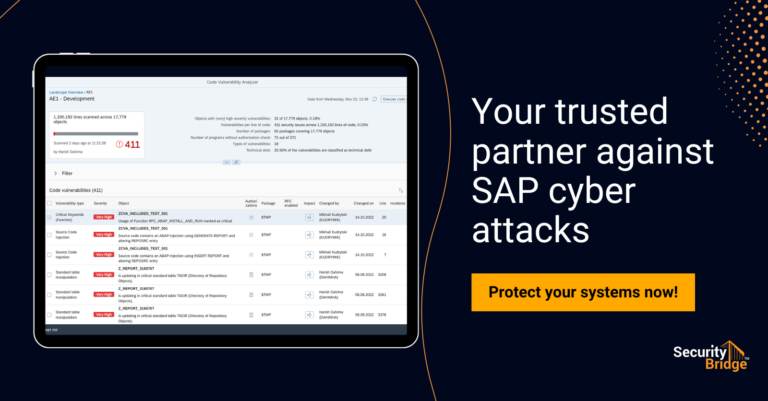
How do you prevent the SAP attack surface from outgrowing control?

Chapters
Share Article
The Log4J and ICMAD experiences
When the Log4J vulnerability was released, many information security teams and SAP customers faced significant challenges. The news was all over the place and immediately caused friction in security departments. In fact, Log4J is a vulnerability that was particularly hard to fix. Internal experts had to investigate the usage of the impacted component before they could investigate individual remediation on a case-to-case basis. Many IT employees were exhausted by sleepless nights and weekend work, but that was needed to get the situation under control.
To make things worse, shortly after the public news regarding Log4J, SAP confirmed that its product portfolio had also been impacted, and customers had to wait for specific patches to be released. SAP systems play a crucial role in creating value for the company, and any unplanned downtime frequently results in financial losses. Even scheduled downtime for security update installation can be challenging to justify in many cases.
As soon as the Log4j wave had finally settled down, another critical message came to SAP customers on February 8, 2022. SAP announced during the monthly SAP Security Patch Day a critical vulnerability in SAP Gateways and Internet Communication Manager (ICM) and published a fix. Installing the patch for this vulnerability, which was later named ICMAD, demanded another downtime. Again, this led to a similar, chaotic situation, especially for those organizations that were not cyber-ready.
It's high time to rethink the strategy
The mentioned events have shown that the strategies existing within many SAP departments are not good enough to counter the unexpected publications of severe vulnerabilities. Organizations should proactively acknowledge the presence of zero-day vulnerabilities and anticipate their exploitation. Under this assumption, new tactics need to be defined. Choosing a proactive approach, rather than merely reacting to situations, helps prevent chaotic responses to critical security incidents and promotes organized handling of such events. Organizations need to target a long-lasting and sustainable security posture that is resilient against currently unknown vulnerabilities.
First phase: Accept and reconsider
The first phase of the solution is for organizations to acknowledge that their existing strategy is insufficient. Acknowledgment entails building management awareness and allocating a budget to address the problem.
This is a crucial investment if you consider the financial impact and the potential reputation damage of a successful breach to your organization. Neglecting cyber security after such devastating past experiences is not an option.
The importance of a sustainable strategy
Cybersecurity is not a project; it is a program. It is crucial that management also understands the continuous investment that is needed to foster a resilient strategy.
Given the assumption that vulnerabilities exist and may be exploited, organizations should consider reducing the level of trust granted to their business-critical enterprise applications. One effective approach is to create an inventory of existing software applications and sort them based on enterprise risk metrics. It’s not uncommon to find SAP applications listed among the top 10 in this inventory.
Alongside a general security program that covers traditional security components such as network segmentation, virus scanning, and client monitoring, an application-specific security program needs to be created. Many organizations refrain from application-specific security initiatives because specific know-how is needed and standardized interfaces to established cyber security frameworks (NIST CSF, MITRE) and Security Information Event Management (SIEM) do not exist.
However, it is of utmost importance that a multi-layered security approach is implemented to provide enough coverage and insight to allow timely detection and adequate response.
What is needed?
The goal is to avoid chaotic situations caused by the release of previously unknown security vulnerabilities. Organizations need to have a plan which consists of multiple dimensions to foster the cyber security posture. Any of the below-mentioned areas need to adhere to continuous innovation methodologies. In other words, this needs to be a dynamic, living standard that gets continuously revisited and optimized.
1. Monitoring
Security monitoring is crucial, because it allows us to detect anomalies. If you accept the existence of zero-days in your technology stack, you will find that monitoring is helpful in detecting the effects of misuse. Transparent monitoring of malicious actions enables timely threat detection and increases the ability to respond with precision to prevent significant damage to the business.
2. Security Hardening
Because of the complexity of SAP applications, many organizations lack understanding of their individual attacker’s surface. This is needed to implement efficient security hardening that targets to increase the security posture of the SAP environment. Combined with regular assessment, organizations can achieve a steady optimization of their cyber resilience.
With every change applied (e.g. the creation of new RFC Destination (SM59)) the security impact needs to be questioned. This area also needs to be continuously improved to reflect the rapidly changing attack landscape.
3. Regular assessments
Continuous assessments that alert upon deviation from security hardening guidelines will be needed to retain the desired level of protection. In today’s world, IT landscapes are constantly changing. Therefore, it is no longer sufficient to check the system security only once a quarter, for example. Every deviation from the established standard should be detected in real-time. Furthermore, a process must be established so that deviations can be quickly corrected.
Solution
Now that you have learned that you cannot rely on the producer of a software solution and that serious vulnerabilities could become public at any time, you should reflect on an appropriate action plan. Being aware of vulnerabilities or exploitation techniques that are currently popular is not sufficient. It’s essential to concentrate on establishing a scenario that maintains your composure when others are in a state of panic. The SecurityBridge Platform offers SAP customers a straightforward and efficient method to achieve this, while also saving valuable resources.