
SAP Security Notes 2025: A Year of Intensifying Critical Risks

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
An analysis of the 2025 SAP security patch landscape so far
SAP has released a significant number of security notes in 2025 already, and the trend is clear: critical vulnerabilities – including several Hot News notes – are becoming more frequent, more severe, and more impactful on SAP customers.
SecurityBridge Research Labs has been actively contributing to these improvements. To date, our responsible disclosures have led SAP to publish 16 official SAP Security Notes, with three high-risk vulnerabilities already included in the 2025 patch cycle: 3550816, 3627998, and 3668705.
This blog highlights some of the most critical vulnerabilities and compares the overall risk landscape with 2024.
2025 at a Glance: Volume and Severity Increasing
• 2025 notes so far: 207
• 2024 total notes included in comparison: 149
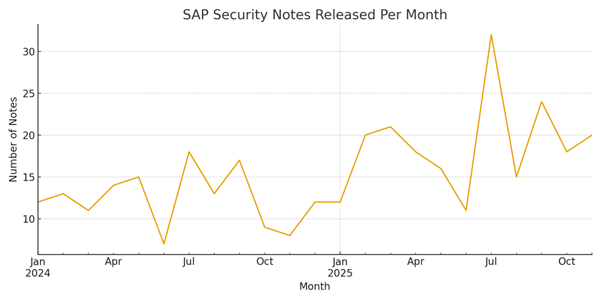
This shows a 39% increase in published notes year-over-year – and the year isn’t over. More importantly, the severity distribution tells a story of escalating risk:
High/critical 2025 notes (CVSS 7.5):
• HotNews (CVSS 9.0): 25 notes, including five at a perfect 10
• High priority corrections (CVSS 7.5–8.9): 35 notes across core SAP components
The Most Critical SAP Security Notes of 2025 (So Far)
Below is a selection of some of the most severe vulnerabilities, sorted by CVSS score and security impact.
1. SAP Security Note 3594142– CVSS 10.0
Missing Authorization check in SAP NetWeaver Visual Composer – Remote, Unauthenticated Exploitation
- CVSS: 10.0 (maximum)
- CVE-2025-31324
- Category: HotNews
- Impact: Complete compromise of confidentiality, integrity, and availability
- Interpretation: Attackers can upload malicious files, enabling full system takeover.
2. SAP Security Note 3668705 – CVSS 9.9
Code Injection Vulnerability in SAP Solution Manager
Reported by SecurityBridge Research Labs
- CVSS: 9.9
- CVE-2025-42887
- Impact: Arbitrary code execution with high-impact pivot potential
- Component: SV-SMG-SVD-SWB
- Why it matters: Solution Manager environments often have deep integration into customer landscapes, making vulnerabilities extremely sensitive.
3. SAP Security Note 3550816 – CVSS 8.8
SQL Injection vulnerability in SAP NetWeaver
Reported by SecurityBridge Research Labs
- CVSS: 8.8
- CVE-2025-0063
- Impact: SQL injection that could lead to gain full control over the data in Informix database
- Component: BC-DB-INF
- Why it matters: Even through Informix Databases are not that common, this vulnerability potentially leads to a full system compromise.
4. SAP Security Note 3627998 – CVSS 8.8
Code Injection vulnerability in SAP S/4HANA (Private Cloud or On-Premise)
Reported by SecurityBridge Research Labs
- CVSS: 8.8
- CVE-2025-42957
- Impact: SAP S/4HANA includes a flaw that enables the injection of arbitrary ABAP code into the system, bypassing essential authorization checks. This effectively functions as a backdoor, leading to full system compromise
- Component: CA-DT-ANA
- Why it matters: S/4HANA is the defacto standard nowadays for customers. Vulnerabilities there affect immediately thousands of customers worldwide.
2025 Compared to 2024: How Does the Risk Landscape Differ?
Volume Comparison
Year | Number of Notes | Change |
2024 | 149 | |
2025 (YTD) | 207 | +39% increase |
2025 is on track to outpace 2024 in the total number of vulnerabilities published significantly.
Severity Comparison
Hot News notes:
• 2024: 11 notes, but fewer with CVSS 9.8
• 2025: 25 notes, Already includes multiple 9.9 and 10.0 CVSS-rated issues
High-severity (CVSS ≥ 7.5):
- Doubled in numbers, from 17 notes in 2024 to 35 in 2025
- Greater focus on components that are:
- Internet-exposed
- Authentication-sensitive
- Critical middleware (ICM, Web Dispatcher)
- Administrative/technical interfaces (Solution Manager, SAP Gateway)
Overall risk trend:
- 2025 > 2024 in both frequency and severity, see below chart for a graphical representation.
- Increase in:
- cryptographic mechanisms
- remote execution surfaces
- cross-system trust relationships
- cloud-connected SAP services
SecurityBridge’s Role: 16 Vulnerabilities Reported to SAP So Far
SecurityBridge Research Labs continues to be one of the most active contributors in identifying critical SAP weaknesses.
To date, our team has:
- Responsibly disclosed 16 vulnerabilities to SAP
- Resulting in 16 published SAP Security Notes
- Including three of the high-risk notes featured in the 2025 patch cycle
These contributions reinforce our position as a leading research group in SAP cybersecurity and demonstrate SAP’s commitment to timely vendor collaboration.
Conclusion: What SAP Customers Should Do Now
2025 has already surpassed 2024 in both volume and severity of SAP vulnerabilities. Organizations should take the following steps:
- Prioritize HotNews notes immediately: The notes with a CVSS of 9+ should be patched without delay.
- Assess cross-component impacts: Many high-risk vulnerabilities can propagate beyond a single SAP system. Make sure to harden your complete SAP landscape, not just Productive systems.
- Strengthen vulnerability detection and monitoring: Solutions such as the SecurityBridge Platformcan detect exploitation attempts, configuration weaknesses, and missing patches.
- Expect more high-risk notes as the year progresses: Given the pace, 2025 may set a record for SAP vulnerability disclosures.
