SAP ABAP Directory Traversal Vulnerability: Risks and Solutions

Chapters
Share Article
SAP developers know that ABAP/4 (Advanced Business Application Programming) is not immune to security vulnerabilities like any other programming language. One significant security risk associated with SAP ABAP is directory traversal vulnerability.
In this blog post, we will discuss what a directory traversal vulnerability is, why it is a problem for SAP customers, how it can be exploited, and what measures to take to prevent it.
What is Directory Traversal Vulnerability?
Directory traversal vulnerability, also known as path traversal vulnerability, is a web application vulnerability that allows an attacker to access files and directories outside the web server’s root directory. The vulnerability, however, not only exists on the SAP web server like SAP Gateway but also poses a risk to ABAP/4 programs.
Similarly to SQL-Injections, this vulnerability can also be exploited by manipulating user input or URL parameters containing file path information. Once the attacker gains access to sensitive files or directories, they can modify, delete, or steal data, causing significant damage to the targeted SAP system.
Why is Directory Traversal Vulnerability a Problem in SAP applications?
Any security vulnerability residing in the mission-critical SAP application can lead to the compromise of data.
Directory traversal vulnerability, i.e., in SAP ABAP/4, is particularly dangerous because it can allow attackers to access critical files and directories that contain configuration information, source code, and user credentials. Attackers can exploit this vulnerability to gain unauthorized system access, escalate their privileges, and execute malicious codes to shut down the system. They can even remain undetected while stealing sensitive business data, including financial information, employee records, and customer data.
How can SAP Directory Traversal be Exploited?
The SAP directory traversal vulnerability exploitation usually involves manipulating the input parameters of a vulnerable function. The attacker can inject path traversal characters such as “../” into the input parameter to traverse the directory structure and access files outside the web server’s root directory.
If, for example, the vulnerable function takes a file name as input and appends it to a fixed path without validating it, an attacker can access any file.
What are Typical SAP Directory Traversal Exploits?
The following code shows an example of a vulnerable function in SAP ABAP:
METHOD read_file.
DATA: filename TYPE string,
filepath TYPE string,
filedata TYPE string.
filename = request->get_form_field( ‘filename’ ).
filepath = ‘/var/www/uploads/’ && filename.
CALL FUNCTION ‘GUI_UPLOAD’
EXPORTING
filename = filepath
IMPORTING
filelength = len
TABLES
data_tab = filedata.
response->set_data( filedata ).
ENDMETHOD.
In this example, the function reads a file from the /var/www/uploads/ directory based on the filename parameter passed by the user. An attacker can manipulate the filename parameter to access files outside the “uploads”- directory.
An attacker can inject path traversal characters into the filename parameter to access arbitrary files outside the uploads directory.
To construct the filename, the attacker would typically use a web proxy or a tool like Burp Suite to intercept the HTTP request sent to the server. They would then modify the filename parameter by appending path traversal characters to access sensitive files.
For example, if the attacker wants to access the /etc/passwd file on a Linux-based SAP server, they could construct the following filename:
../../../etc/passwd
The “../” characters traverse up the directory tree until they reach the root directory and then access the etc/passwd file. This file contains user account information, including usernames and hashed passwords, which the attacker can use to escalate privileges or perform further attacks.
What is SAP Recon?
One of the most infamous directory traversal exploits in SAP ABAP is the “SAP Recon” exploit. This exploit targets SAP NetWeaver systems and can be used to extract sensitive configuration information, including usernames, passwords, and server settings. The attack exploits a directory traversal vulnerability in the SAP NetWeaver configuration file, allowing the attacker to download the file from the server. SAP Recon exploit works by injecting path traversal characters into the URL parameter used to download the configuration file. The following URL shows an example that is not related to the SAP Recon exploit:
http://example.com/irj/servlet/prt/portal/prtroot/pcd!3aportal_content!2fevery_user!2fgeneral!2fdefault
How can SAP Customers Protect Their Systems?
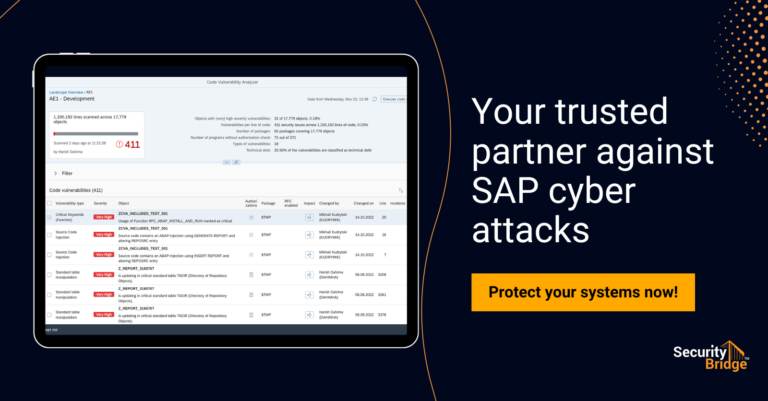
SAP customers can use the SecurityBridge Platform to spot vulnerable coding that resides within their SAP applications. The SecurityBridge Platform provides a Code Vulnerability Analyzer specifically designed to scan customer-created code for vulnerabilities of all types in SAP ABAP/4 programming language.
The Code Vulnerability Analyzer is a static code analysis tool that scans ABAP source code to identify potential vulnerabilities and security risks. It works by analyzing the structure and content of the code to detect patterns and code smells that indicate potential security issues.
Code Vulnerability Analyzer checks for many vulnerabilities, including directory traversals, SQL injections, and Cross-Site Scripting (XSS).
One of the main advantages of using the SecurityBridge Platform is that it provides a centralized view of security risks and vulnerabilities across multiple SAP systems. As a result, SAP customers can prioritize their security efforts and remediate vulnerabilities before attackers can exploit them.
In addition to the Code Vulnerability Analyzer, the SecurityBridge Platform provides various other security tools and capabilities, including:
- Vulnerability Management for SAP: It is a system that identifies, prioritizes, and manages vulnerabilities across the SAP landscape.
- Threat Detection for SAP: A real-time monitoring system that detects and alerts potential security threats and attacks.
- Compliance Management for SAP: A tool that helps SAP customers comply with industry regulations and security standards.
In summary, the SecurityBridge Platform provides SAP customers with the most comprehensive security tools available to identify and remediate vulnerabilities in their SAP systems. The Code Vulnerability Analyzer is a critical component of this platform that enables customers to scan their custom ABAP code for vulnerabilities and ensure that their applications are secure from the ground up.