Chapters
Share Article
The application security market is obscure and holds one or two surprises for those looking for an SAP security solution. Cybersecurity solutions for SAP help customers understand the ever-growing threat landscape and protect themselves effectively. In this article, we would like to discuss some points you should focus on when looking for a security solution for SAP.
What is an SAP Security or SAP Cybersecurity Solution?
As the name suggests, SAP Security or SAP Cyber Security solutions are highly specialized software products that can monitor cyber threats, security-critical activities, application configuration, and more. In the case of SAP’s business-critical applications, other aspects such as security patch management and monitoring of interface traffic also become necessary. The distinction between SAP GRC and SAP Cybersecurity is not clear-cut, and therefore, it is often needed to think of an integrated approach. For more on this, see the article: GOVERNANCE, RISK, COMPLIANCE (GRC), REGARDING CYBERSECURITY FOR SAP.
Special forms of SAP Security Solutions
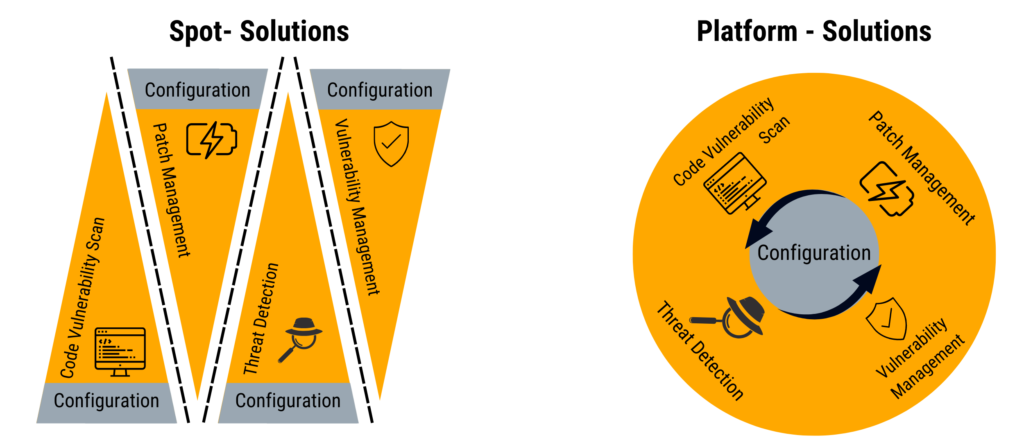
SAP Cybersecurity products are divided into solutions and platforms. In contrast to a solution that usually covers a single topic area, an SAP Security Platform takes a holistic approach to protect customer data. Unfortunately, it is not always easy to tell from the glossy brochures of the suppliers whether a platform product is not a single solution.
A real platform characterizes itself when the customers’ maintenance effort (TCO) is reduced thanks to the software architecture. This is the case when a central basic configuration exists on which the security applications are based. Also, the platform should not require you to update each SAP security application individually. The platform gets an upgrade. The special added value of the real platform approach is that the security applications exchange necessary information and expand the user’s view in a systematic form. When properly implemented, the end user can always access all the crucial information needed to evaluate a security incident.
Architecture differences
If you look around for SAP security applications, you will quickly realize that there are not only solutions with different functional scope and depth but also different architectural approaches. Which one suits you best depends on the application and purpose.
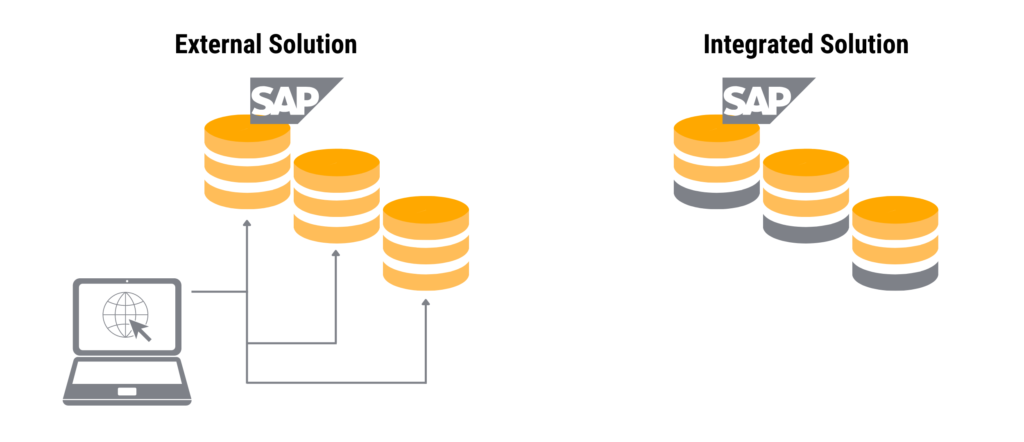
The integrated approach relies on a software architecture that tries to extend the SAP application’s technology stack with required capabilities to protect the crown jewelry. A particular advantage of this approach is that usually no additional hardware (or virtual appliances) is required. These are often forgotten in the cost analysis and the licensing costs and lead to a nasty surprise in the implementation project.
In contrast, there is also an external solution that accesses the SAP application via an interface and attempts to read out the data necessary for security analyses.
This approach advertises a reduced footprint on the application, which looking closely, is often not so small. External security applications are certainly an excellent choice for closed systems where customers cannot install plugins. However, this does not apply to SAP because, just like with operating systems, you can use additional add-ons. Since this article is about a security solution to protect SAP, it is crucial to note that additional software and appliances often introduce new attack vectors that the customer must analyze. If an attacker can exploit a vulnerability in a security solution, the solution becomes a problem for SAP security. So, check the selected SAP Security Solution for security vulnerabilities and standard security measures brute force protection (2FA), remote access, and update architecture.
What to expect from SAP Security solutions?
In this section, we look at the functional scope of an SAP Cybersecurity Solution. A word of caution – No matter what the provider promises you on the website or in glossy brochures, you should form your own opinion in any case. It has already happened that product comparisons were wrong or biased. Be sure to ask for a demonstration of the features you want, and if in doubt, ask for a test installation. Make sure the product you want to buy is used during the test!
Now to the functions you need as an SAP customer. On the one hand, there are four functional vectors that SAP security solutions should cover. Depending on your requirements profile, you may, of course, only be interested in one area. But at the end of the day, to effectively protect SAP against cyberattacks, you must address all of them.
Consider the following functions:
Of course, the functional depth, which details what the selected solution offers you varies among manufacturers. Therefore, we advise you to create a requirements list of the required functions, which will help you with an objective evaluation. At SecurityBridge, we believe in transparency and openly disclosing to our prospects what is covered and what features are on the roadmap. Be sure to ask for a product roadmap to learn from the vendor of your choice if there is a solid innovation plan. Especially in cybersecurity, innovation is necessary to prepare for the rapidly changing risk situation.
When should you look for SAP Security solutions?
Fundamentally, it is true – it is never too early, but it could be too late.
According to this principle, you should prefer proactive actions to reactive ones. Especially, when it comes to securing critical enterprise infrastructure and applications such as SAP.
Here are some examples:
- If you are a CISO, Chief Information Security Officer, or a CRO, Chief Revenue Office, and you feel that your SAP systems are not patched regularly, and on time, you should look for a solution.
- If you are an SAP Basis manager who cannot keep up with monitoring security-related settings, you should look for a solution.
- If you manage ABAP developments and notice that the established code quality checks do not sufficiently cover security aspects, you should look for a solution.
- If you are responsible for the integration and can no longer say with certainty whether all SAP RFC connections are sufficiently hardened, you should look for a solution.
To conclude, if you have determined that you need an SAP Cybersecurity solution, you should talk to us to have a look at the SecurityBridge Platform for SAP.