- February 1, 2021
IBM QRadar Security Intelligence

Key Takeaways
- The article explains why a direct integration between SAP and your preferred SIEM solution (we use IBM QRadar in this example) makes more sense than using a pass-through solution.
- How to build a solid and reliable integration and why you should prefer a smart vs big data approach to monitor complex applications like SAP.
- You can find information on how the interface and the architecture in an SAP to SIEM integration scenario using SecurityBridge works.
Enable SAP insight within your Security Operation Center (SOC)
In recent years, IT security departments have been primarily focused on monitoring the corporate network, ranging from firewalls, routers, and operating systems. Currently, we are seeing this focus shift to critical enterprise applications. SAP is one of the world’s leading providers of software for managing business-critical processes. The solutions developed by SAP are the backbone for many organizations, enabling effective data processing and a cross-company flow of sensitive information.
With ever-increasing pressure on IT security managers due to increased challenges in the protection of critical data assets, it’s no wonder that the demand for standardization and harmonization of SecOps processes is substantial. A central component is the Security Information and Event Management System (SIEM). While SIEM tools have been around for many years, Security Orchestration Automation and Response (SOAR) is both newer and increasing.
Seldomly, security agents working in a security operation center (SOC) have insight into SAP, as SAP is notoriously complex. Although SAP acknowledges the need for application security, the SAP systems are still perceived as black boxes. SAP ABAP, JAVA and HANA technology stacks have a wide range of data sources that are relevant for security and audit monitoring. One of the best-known data sources may be the SAP security audit log, which improved considerably over the past years. But what shows as a red alert in an audit log, may in reality be just a regular SAP process. Additionally, there is still a range of attack vectors that don’t leave any trails in the SAP security audit log.
Enabling a SIEM or SOAR platform to directly access your SAP’s audit log, may allow you to tick some audit requirements, but in practice, it doesn’t make your systems any more secure and often results in alert fatigue.
Our mission at SecurityBridge is to help customers secure their SAP systems, without the need for SAP security expertise, intense implementation projects or increased hardware requirements.
Years ago, we recognized the need for an intelligence security data feed, enabling SOCs to bridge-the-gap between SAP systems and well-established IT security platforms. Since then, SecurityBridge has enabled SAP customers to have a SOC monitor for SAP exploits, breaches and vulnerabilities, in real-time and 24/7.
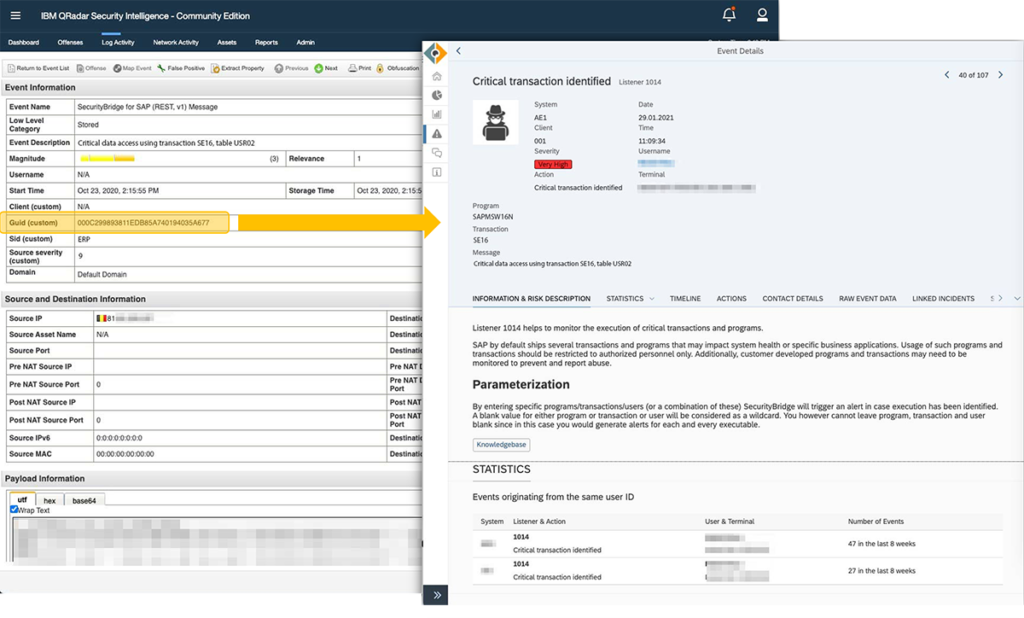
SecurityBridge applies a unique approach by translating the cryptic and technical messages sourced from the various SAP application logs into speaking and actionable security intelligence, which can be interpreted without explicit SAP expertise. SAP alerts are converted into a language understood by IT security teams, which massively reduces training effort and accelerates the time-to-security enormously. For every single alert, SecurityBridge provides a clear risk description, severity rating, and all relevant context information which will help a security agent to triage effectively.
The SecurityBridge intrusion detection system, distinguishes SAP application messages from security-relevant alerts and only sends the relevant events to the security team. Such events are not only singular alerts, as intelligence is applied to also identify specific patterns such as authorization bypasses, cover-ups, and much more.
Converting the mass of data into an intelligent data feed reduces the flood of information flowing from SAP to your SOC. SAP events are correlated and complemented with all other data sources to provide 365-degree monitoring.
SAP to SIEM Interface
Converting the mass of data into an intelligent data feed reduces the flood of information flowing from SAP to your SOC. SAP events are correlated and complemented with all other data sources to provide 365-degree monitoring.
The interface between your SAP landscape and the SOC operating a SIEM/SOAR platform is mission critical. The communication channel must be infallible, reliable, easy to install and with minimal maintenance.
A man-in-the-middle approach using a third-party pass-through component should be avoided. SecurityBridge makes use of the SAP NetWeaver Stack. It’s trusted and readily available in the landscape. The data flowing between SAP and the SOC should be end-to-end encrypted.
In this article we will use IBM’s SIEM, QRadar Security Intelligence, as an example. SAP customers using SecurityBridge will have a plug-and-play experience in establishing a secure and reliable connection. QRadar instantly connects to SecurityBridge’s RESTful API. Other SIEM platforms such as Azure Sentinel, Splunk, ArcSight, and many others can be connected in a very similar way.
How does the connection work?
Firstly you install the SecurityBridge platform within SAP. SecurityBridge is a certified SAP add-on which is widely used and easy to deploy. As part of the installation, you also download the latest configuration, ensuring that you are up to date with the latest signatures and recognition patterns. Once installed, the intrusion detection, which is the engine that continuously harvests all SAP data sources and which monitors interface and user traffic, can be started.
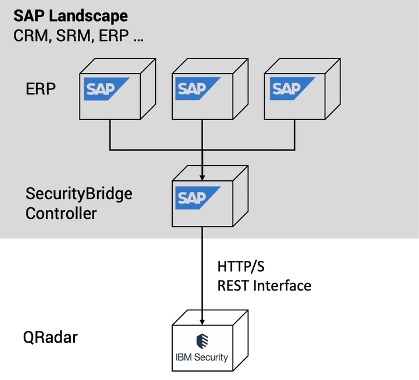
A single system in your SAP landscape is nominated as the “Controller”, responsible for collecting and aggregating all security-relevant events across the entire landscape. It’s also the hub for feeding your SIEM.
IBM QRadar has an adapter for the distinct purpose of connecting with RESTful APIs. The adapter module is called Universal Cloud REST API for IBM QRadar.
The adapter configuration can be completed in minutes using a preconfigured SecurityBridge workflow available directly from the official IBM QRadar GitHub repository.
The mapping between SecurityBridge and IBM QRadar is done using a custom Device Support Module (DSM), which can be downloaded by SecurityBridge customers.
This setup ultimately results in a simple yet stable, low-maintenance integration.
Once SAP can be monitored by your SOC, a project that is far easier than you might have anticipated, you can then focus on the crucial purpose, the detection of cyber-attacks targeting mission-critical enterprise systems.
Author's note
During the development of the SecurityBridge workflow and the custom Data Server Manager, for the IBM QRadar Universal Cloud REST Adapter, we were in close contact with the IBM QRadar product management. In addition to the comprehensive and detailed documentation provided, we could also always rely on support from our partners at IBM. The IBM QRadar Security Intelligence SIEM is a leading platform due, not only to its excellent technology, but also because of the dedicated support of the IBM employees, the usability of the IBM QRadar SIEM solution itself, and the great community.
Posted by
Looking into securing your SAP landscape? This white-paper tells you the “Top Mistakes to Avoid in SAP Security“. Download it now.







