
The Art of SAP Security

Chapters
Share Article
Key Takeaways
- Security is a skill. Organizations need to learn, train and enhance their security skills to become efficient in cyber defense.
- 100% may be your biggest enemy. Doing anything is better than nothing. Realizing that 100% security does not exist, is a necessity.
- Continuity is key. Cyber threats are always present. A moment of carelessness can lead to major damage. That is why SAP security must be constantly kept in mind.
A role model for SAP Security
Headlines about a publicly available exploit for a vulnerability existing in SAP Solution Manager have shocked the SAP community. This raises the seriousness of securing SAP applications amongst CISOs and other senior level security.
In practice what often happens is this: The IT-Security member responsible reaches out to the SAP team, seeking the support of the subject-matter experts to address the issues. From the perspective of the SAP team, this means additional work, on top of a likely over-burdened workload.
At this point, it is important that the IT-Security experts address a common misunderstanding within the application team. IT-Security, particularly for complex enterprise-critical applications, is a skill and not a static attribute. There is an especially important and distinct difference which I will explain. A “Skill” is defined as something that can be taught, needs practicing, and which might improve going forward. With more practice, the skill level increases. Challenges, such as the detection of false positives, are part of the learning process, as this is the only way for a company to increase its level of experience in cybersecurity. If SAP security is wrongly perceived as an “attribute,” it is likely that the initiative will fail, as it is not a single event, it is a continuous problem. In the worst-case scenario, the issue is reported to senior executives as a “solved”, tick-box set.
SAP Security Strategy: what is needed
Starting a security initiative for SAP, requires clear communication, change management skills and a deep understanding of the structure of the SAP organization. Onboarding the right players within the organization and adjusting their perspective on the upcoming security task is essential. You may have recognized that I deliberately used the term „security initiative“ and not project. That is again to emphasize that once started, the initiative will never end. A project on the contrary is initiated to solve a specific requirement or problem and ends after the project goals have been reached. A security initiative consists of many projects and demands a comprehensive strategy and the backing of your management.
Start with a Strategy
Building the security strategy for SAP may be a challenging task that requires knowledge about the SAP system architecture, business processes, data classification, interfaces and even the SAP team structure. The strategy needs to address many areas:
- Hardening: Secure configuration, Authorization management, etc.
- Vulnerability Management: Patching the standard product and detecting vulnerable custom code
- Monitoring: SAP specific monitoring and the connection to general security monitoring and automation (SIEM and SOAR)
- Training: Education of key players like SAP Basis, and Developers but also end-users shall not be forgotten.
- Internal control systems: Regular audits including compliance checks. Introducing 4-eye principles for critical activities.
The strategy needs to be built under the premise to implement a continuous innovation cycle.
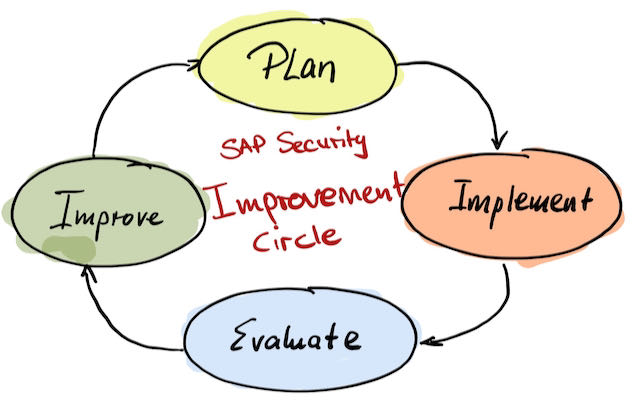
Summary
Positioning SAP security for your management teams requires input from security people and SAP experts. Your organization can only improve and grow its’ SAP security posture when an initiative is started.
100% security just doesn’t exist! Any security measures taken will not be perfect, ever, and will require continuous adjustment. Ignoring security for SAP is not an option, it’s merely applying due diligence to any company’s most valuable, and essential core business.
