The ‘Rapid Reset Attack’ – an SAP perspective

Chapters
Share Article
Recently, we have seen the release of several SAP Security notes that address the so-called ‘Rapid Reset Attack’ vulnerability. In this blog, we will zoom in on this vulnerability, look at how it affects SAP systems, and what countermeasures can be taken.
The Rapid Reset Attack
In 2023, a ‘Denial of Service’ vulnerability was made public called the ‘Rapid Reset Attack’. It is cataloged under CVE-2023-44487 and reported to be exploited publicly ‘in the field’. So, what is it exactly, and why did it get this fancy name? To understand this, we need first to have a look at the Hypertext Transfer Protocol (HTTP) protocol and its different versions.
Everyone knows or has heard of the HTTP protocol. At least anyone who has ever used an internet browser… However, probably not everyone realizes that this protocol comes in different versions. For an average user, that’s perfectly fine, there is no need to know these things. For IT experts though, it IS of crucial importance and this vulnerability shows exactly why. We don’t mean to give an extensive overview of the protocol here, many resources go in the nitty gritty details (see references below). But we’ll give you a summary in the context of this vulnerability.
Protocol Versions HTTP/1.1 and HTTP/2
For a long time, HTTP protocol version 1.1 was the main version in use everywhere. HTTP1.1 was released in 1997 and thrived along with the massive growth of the internet. Like everything though, it wasn’t perfect. The 1.1 version of the protocol is limited in handling multiple requests over a single TCP connection. As demand for this protocol increased and optimizations were added, there was an overall negative impact on the efficient processing of requests between the HTTP client and server.
These efficiency issues were addressed and released in version 2 (HTTP/2) in 2015. The main differences are that HTTP/2 is:
- based on binary protocols which are more compact and less prone to errors;
- using multiplexing for parallelization to prevent blocking of requests;
- using header compression;
- allows servers to ‘push’ a response rather than only waiting for clients to ‘pull’;
- doing all this over a single TCP connection.
The ‘multiplexing’ part is of interest here. This means multiple ‘streams’ of data can be opened, containing multiple messages in request/response format. That is great for efficiency, but it also came with the option for HTTP clients to request a server to cancel a previously opened stream. And that is where this vulnerability comes into play. A client can open a stream and immediately cancel it afterward. This open/cancel activity requires few resources from the client but can put a resource strain on the server. So, a client can open and immediately close large numbers of streams and by this try to overload the server side. Hence the term ‘Rapid Reset’ for this attack.
Impact on SAP Components
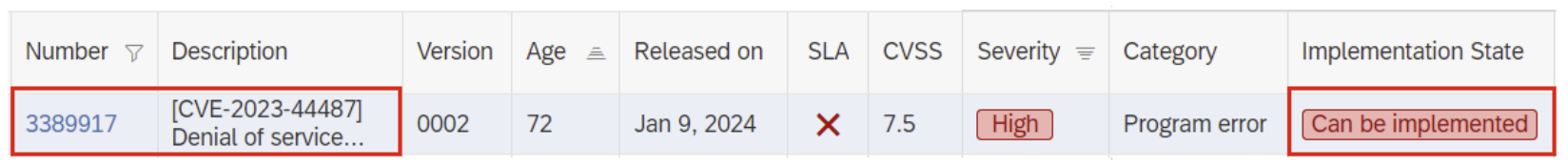
Now that we have this summary of the attack, let’s look at the impact on SAP. The vulnerability was disclosed in October 2023. SAP has released 3 security notes so far that address the issue and recommend action: 3398186, 3389917, and 3410615. Based on the security notes released by SAP, it is mainly the Internet Communication Manager (ICM) and Web Dispatcher components that require patching or disabling of HTTP/2 as a workaround. Concretely: this concerns the following components:
- Web Dispatcher (standalone or embedded variant)
- NetWeaver ABAP
- Web Dispatcher (XS Classic and Advanced)
- PowerDesigner
Other components like NetWeaver Java, SAP Cloud Connector, and SAP Business Objects are not affected.
How to fix the Rapid Reset Attack Vulnerability?
The obvious answer to this question is: PATCH IT! While this is true, there are some points to consider when checking this manually:
To find out if your systems are vulnerable, check the version of the ICM and Web Dispatcher in use. Depending on the version, HTTP/2 is either: not available at all OR only active if specifically set OR active by default. If HTTP/2 is active, the version may be vulnerable and require patching, or rather not.
Then to patch the components, keep in mind that you need to patch in different ways:
Component | How to patch? |
Web Dispatcher standalone | Patch Web Dispatcher component directly |
Web Dispatcher embedded NetWeaver ABAP | Patch the kernel of the affected ABAP system. Note that the embedded Web Dispatcher is a part of the ABAP central services instance (ASCS)! |
Web Dispatcher XS Classic / Advanced | Patch the HANA database and runtime components. |
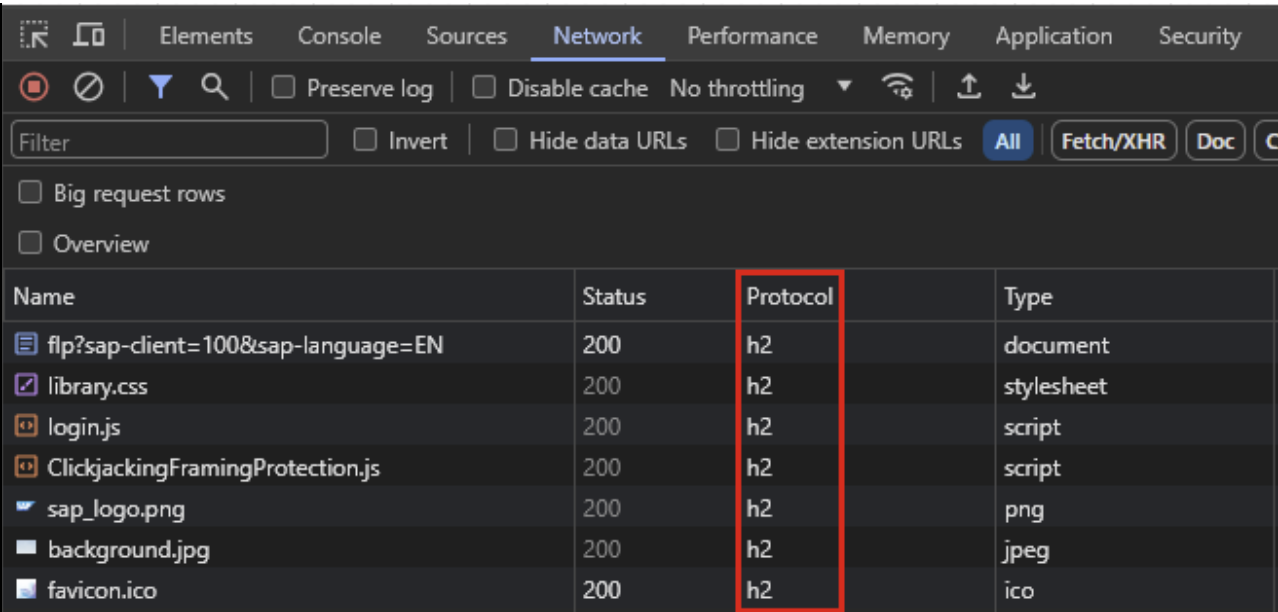
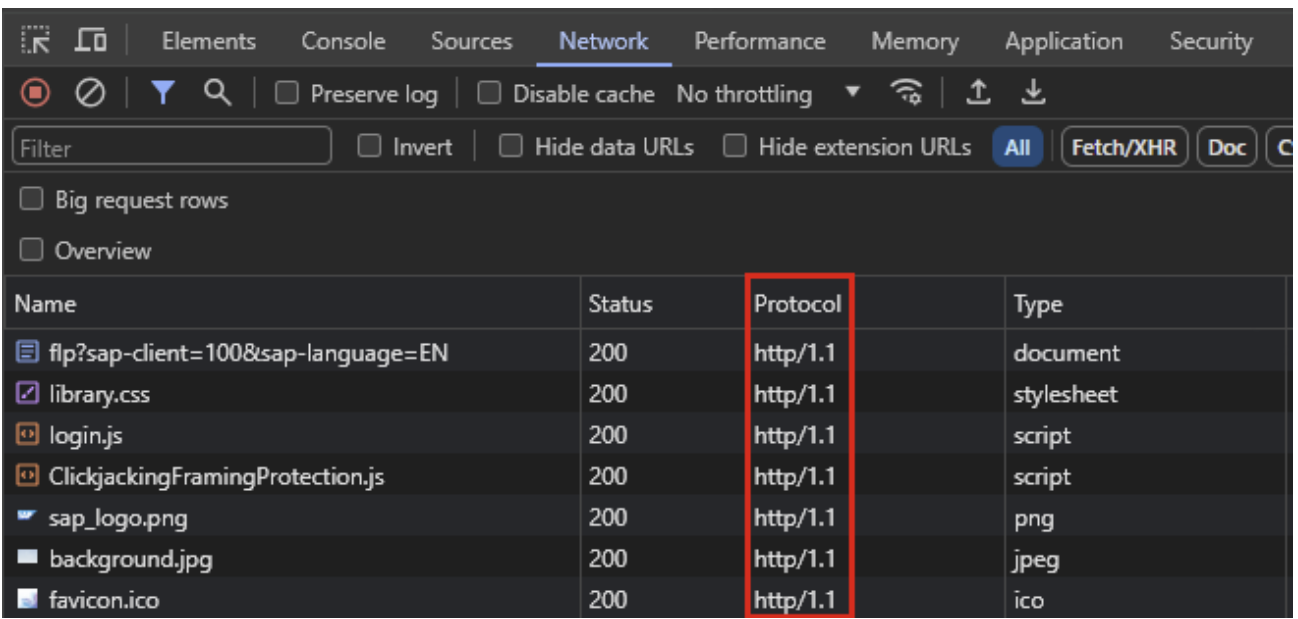
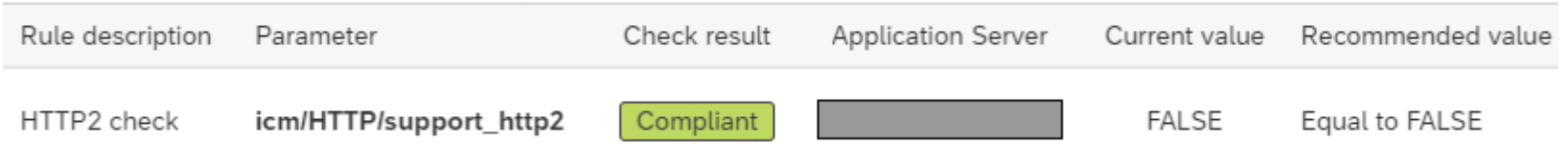
Another possibility is to first – temporarily – apply a workaround. This is controlled with ICM parameter icm/HTTP/support_http2. Setting this to ‘FALSE’ will disable HTTP/2 altogether and as such, will render the component not vulnerable to the ‘Rapid Reset Attack’. Checking the workaround can be done with a simple browser check using the developer tools, see below.
A Better Solution
Going through the versions manually for each component in your landscape or setting and checking the workaround is time-consuming and error-prone. There is a much easier way! Our SecurityBridge ‘Patch Management’ solution easily shows what components need to be fixed in a clear and effective overview. As simple as this:
And checking for parameters – in the case of applying the workaround – is just as easy. With a custom baseline setting on our Security & Compliance monitor, all systems can be checked for the correct value. Showing the parameter this way:
If you would like to see these capabilities demonstrated, you can contact us, and one of our team members would be happy to meet you in a live online session to demonstrate this capability from one of our lab environments.
With these solutions, it is no longer required to do a lot of manual activity for checking and re-checking, only to make sure your SAP landscape is secure. Try SecurityBridge and immediately improve the security of your SAP landscape. Find out for yourself the ease of use of our solutions and how much time can be saved on basic security tasks. Explore the ton of other functionalities we have to offer to make your SAP landscape more secure while saving precious resources and money at the same time.
For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn.