
Weekly routine of successful SAP Security Administrators

Chapters
Share Article
Protecting SAP environments is a specialized topic within the overall IT Security of enterprises today. It requires specific knowledge and highly specialized tools to cover the entire SAP technology stack and all aspects of SAP Security. Successful SAP security administrators stay on top of these tasks by embracing a weekly routine, like this one, to continuously mature their SAP Security practice.
Analyze SAP Security Logs statistics to continuously reduce false positives
Monitoring the security and audit logs of SAP is a 24/7 task, ideally implemented by leveraging tools that collect the data from all available SAP sources, filter them based on rules, and forward them to monitor consoles or SIEM solutions. Cyber-attacks and malicious user activities are like needles in the haystack of audit log records. To make finding the needle easier, one best practice is to reduce the “haystack” of false positives.
Powerful rule engines and flexible filters are the critical success factors for reducing the number of events that require the attention of an SAP security administrator. Once a week, the administrator reviews the event statistics of the past 7 days to identify event types that show a high frequency. There is a high chance that many of them are caused by normal user activities and process workflows. Rich event attributes help create new filter rules that reduce the number of false positives in the SAP Security monitoring tool.
Here is an example from the SecurityBridge Threat Detection monitor that uses smart filters to identify frequent events and allows simple filter rule creation based on the selection. In this case, a certain system user is always used for critical activities and the corresponding logons can be filtered out. With a few clicks, the rule engine is finetuned and the “haystack” of false positives is reduced.
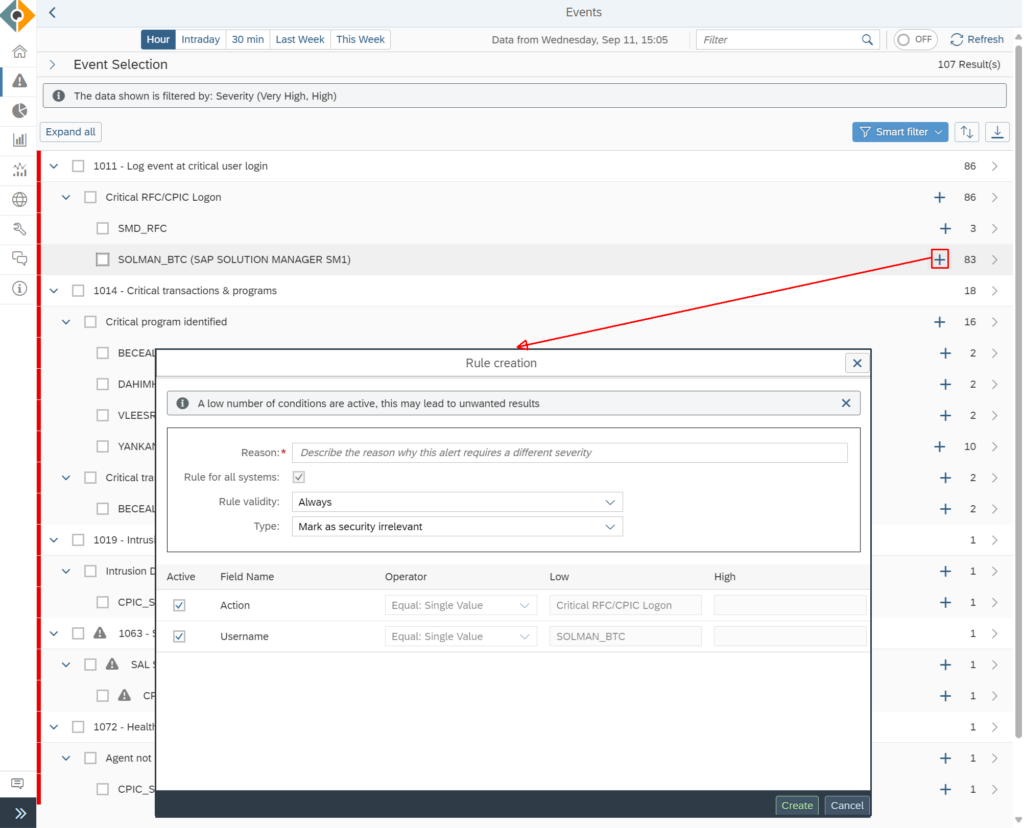
There are definitely other ways to identify the few critical activities that can lead to a cyber-attack. A Threat Detection engine with powerful preconfigured attack vectors is one option. Additionally, the enforcement of the least privilege principle by implementing solutions like Privilege Access Management will help you reduce the background noise in your event log caused by normal administrative activities.
Check Patch Management progress status
Implementing SAP patches (also known as SAP Security Notes or SNotes) as soon as possible significantly reduces the attack surface of the SAP landscape. On the second Tuesday of the month, on Patch Tuesday, SAP releases patches for known vulnerabilities in SAP systems. This is the starting point for the race between attackers and defenders. SAP security administrators can only win by either implementing compensating controls or installing the patch, if available, before the exploitation.
Successful SAP security administrators continuously push the Patch Management process forward and track the progress on a weekly basis. Ideally, the SAP team can implement all new patches within 4 weeks, before the next Patch Tuesday. Understanding the severity of patches, their impact on your SAP landscape, and their relevance to a specific system is key for efficient and short-term system patching.
Therefore, SecurityBridge helps customers with a guided approach to balance between patch severity and implementation effort within the relevant patches for a specific SAP system. The example below shows the Heat Map of pending SAP Security Notes in the landscape grouped by severity and age. This allows customers to burn down their SAP patch implementation backlog efficiently and quickly.
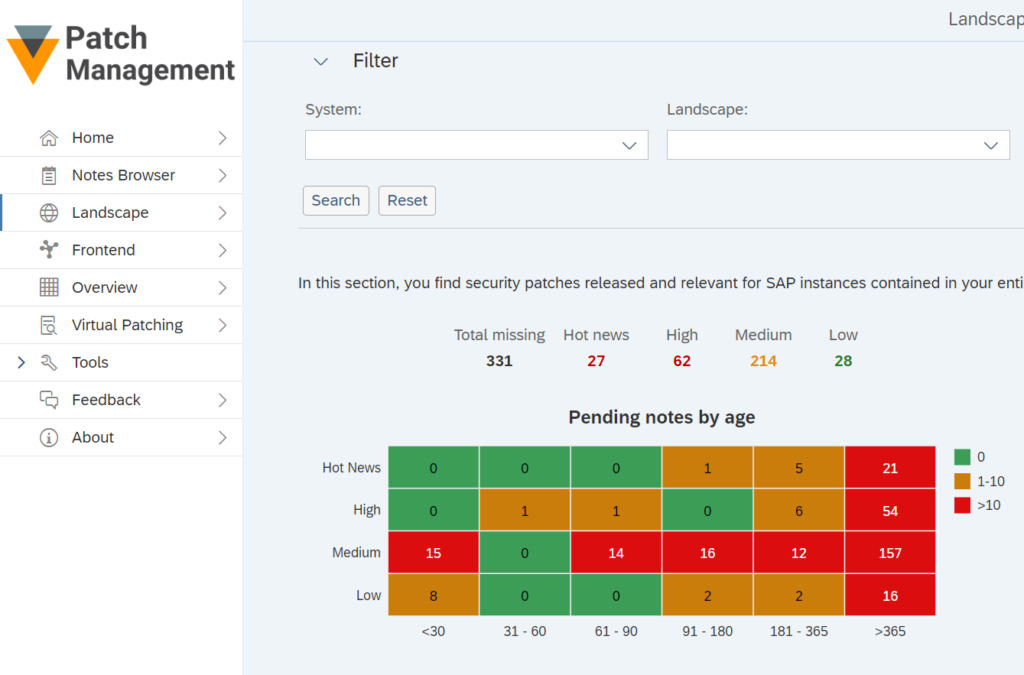
Automating the implementation of SAP notes and patches is another way to increase the efficiency of this process within a customer’s organization. SecurityBridge is also innovative in this area of SAP Security by providing an automated implementation for the majority of SAP Notes. Only patches with no manual steps are released for this automated procedure and can be safely deployed in the target system.
When timely patching is not possible, though this should always be an exception, SecurityBridge offers compensating controls like Virtual Patching. This feature leverages the power of an integrated platform by automatically configuring the Threat Detection rules to monitor the usage of unpatched SAP programs or function modules. This allows SAP security administrators the chance to identify the potential exploit of vulnerabilities in the SAP standard code.
Check SAP Security configurations and compliance status
SAP systems contain a huge number of parameters, many of which are security-related and have a significant impact on the attack surface. SAP Security experts understand how cumbersome it is to check these parameters for secure settings to “get clean” and “stay clean,” especially with the constant changes in an SAP environment. Therefore, automating these checks and tracking the process of system hardening on a weekly basis are key success factors for achieving a mature SAP security posture.
A good starting point is the SAP Security Baseline, which is regularly updated by SAP. It contains minimal recommendations for secure settings in SAP environments. Other baselines, such as the one from DSAG (the German-speaking user group), go further by extending the security recommendations. The SecurtiyBridge baseline contains all best practices for hardening SAP systems and environments, providing a comprehensive approach to SAP security.
These best practice recommendations are presented in a daily updated Security Roadmap for SAP , featuring ranked findings based on a balance between exploitation risk and resolution complexity.
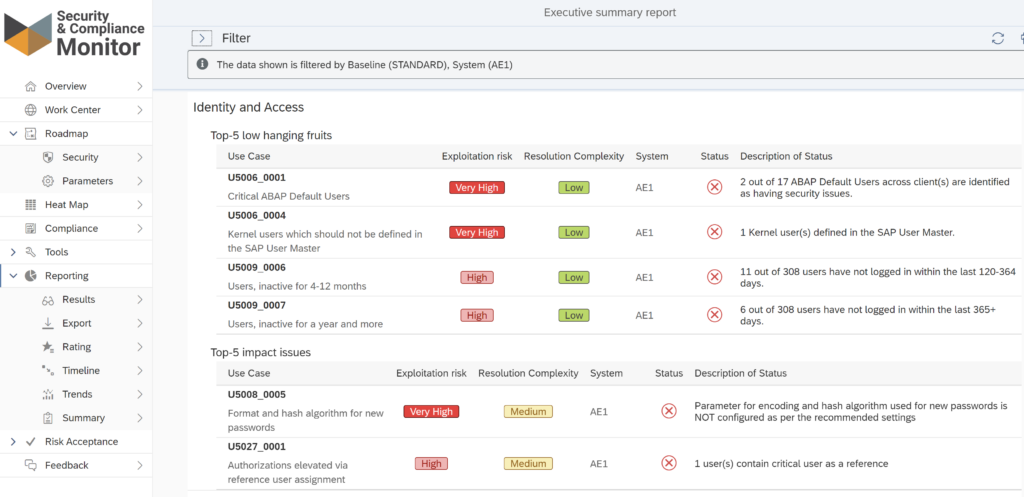
Starting with the “low hanging fruits”, vulnerabilities that have a high risk but can be easily mitigated, the roadmap also provides all necessary details for decision-making, including the recommended parameter values. With this information, SAP security administrators are on the best track to harden their SAP systems and preserve that level moving forward.
Regardless of the underlying baseline, successful SAP security administrators use them to continually validate the security level and hardening of their SAP landscape. As this is quite a comprehensive task, it makes sense to distribute areas of responsibility (AoR) across the SAP team members for efficient parameter maintenance and validation of the compliance rating per AoR, as shown in the following SecurityBridge Security & Compliance trend report.
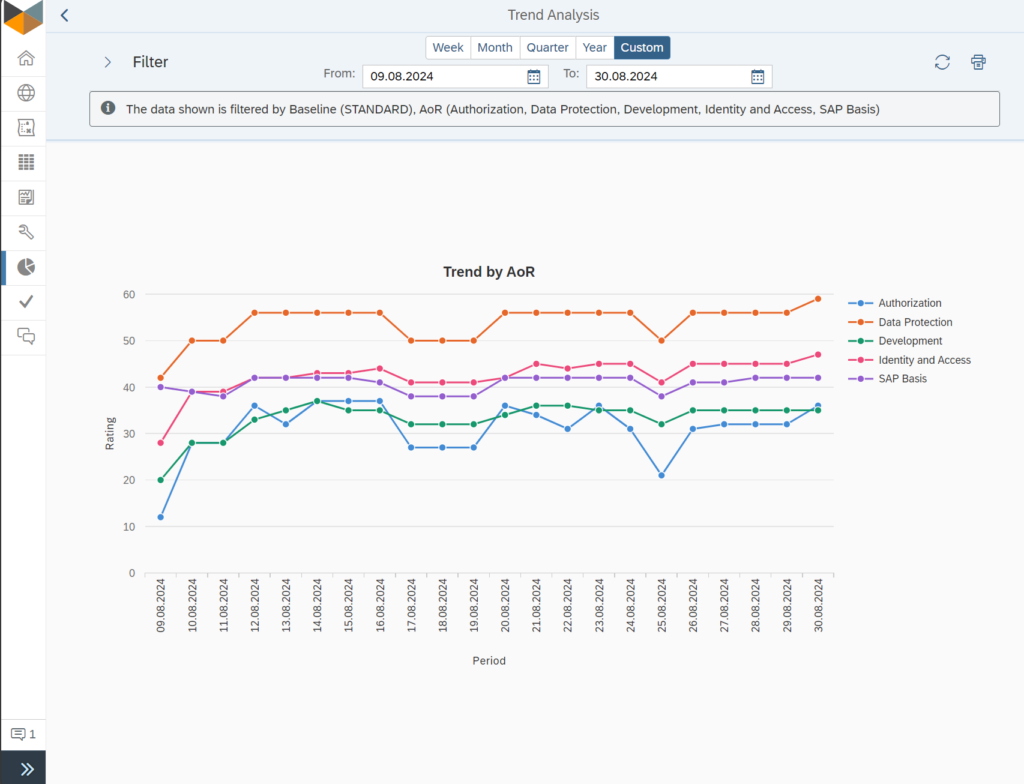
Documenting these checks is an important task for the next security audit. Ideally, it includes risk acceptance for any deviations from the baseline, whether due to postponed mitigation or justified by environment-specific factors. SecurityBridge supports SAP security administrators with these features, helping them effectively master and pass any security audit.
Are you interested in learning how we can help you adopt Security & Compliance and establish an SAP Security Hardening Roadmap? Contact us and we will be happy to tell you more about our guided approach to SAP Security excellence. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!

