Understand and reduce the Attack Surface

Chapters
Share Article
Knowing the attack surface in today’s world is very important to reduce the risk of exploitation of the so-called unknown-unknown. Zero days are vulnerabilities that have not been patched and are also not widely known. Organizations need to assume that any application, also the enterprise-critical solutions from SAP, contains a severe vulnerability that can’t be patched since no patch is available. Waiting for the moment the vulnerability gets published and patched by the software vendor, may not be a safe bet, since threat actors may already know and exploit the open loophole.
At SecurityBridge we interact with partners and customers to understand their risk appetite and to engender a solution to mitigate the unacceptable risks. One of the first questions is the following: Do you know your attack surface?
What is the attack surface?
The attack surface is the sum of all possible entry points, or attack vectors, where an unauthorized attacker can access a system or application to e.g. extract data or manipulate sensitive information. The smaller the attack surface, the easier it is to protect.
Why is the SAP attack surface so important?
Organizations must constantly monitor their attack surface to identify and block potential threats as quickly as possible. They also must try to minimize the attack surface area to reduce the risk of cyberattacks succeeding. In context of SAP the Internet Communication Manager (ICM) or Internet Communication Framework (ICF) available via SAP transaction SICF, but also the remote function call connection setup is prone to overexposing services to the outside.
SAP customers with SAP security in mind need to continuously assess and inventory the exposed services (SOAP, WebService, API’s). Any service that is not used or does not serve a specific SAP business scenario should be deactivated to reduce the attack surface and thus also to minimize the risk of exploitation.
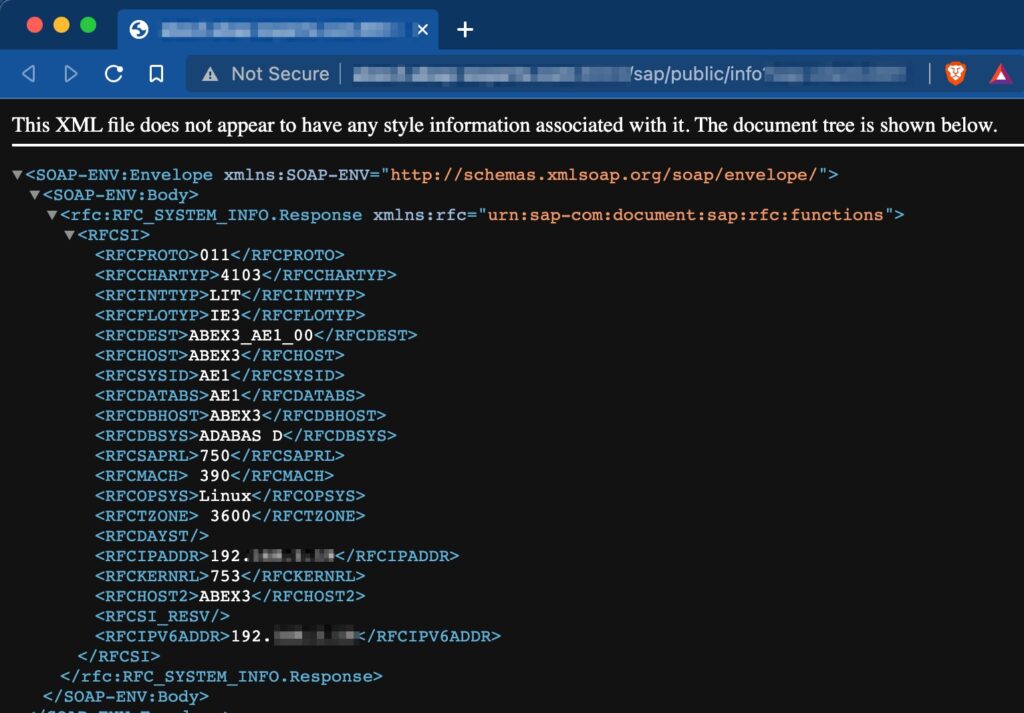
Furthermore, a close tab needs to be kept on those services that are not requiring authentication. In SAP they exist in the /sap/public/ namespace that can be found in transaction SICF. Services like /sap/public/info are the number one touchpoint for threat actors to gather information in the exploration phase of an attack.
Effective counter measures against SAP Zero-Day exploitation?
Just to remind, a zero-day is a vulnerability that is not yet widely known, and no patch exists. Hence patching is not an option. This does not mean that regular and timely patching is not one of the most effective exercises to protect against exploitation, on the contrary. Next week Tuesday on the 8th of February, SAP customer expect to see another SAP Security Patch Day. Any second Tuesday of a month, SAP publishes the new security patches. This event starts the race between attackers and defenders, who can only win by installing the patch before the exploitation.
SAP sponsors bug bounty programs to support bug hunters and security researchers. There are various individual researchers but also entire research labs that analyze standards software for vulnerabilities, however, even with a combined effort zero-days can’t be eliminated.
SecurityBridge Patch Management informs you once a new patch has been published that is relevant for your specific system installation to reduce effort and lead time before patching. Additionally, the SecurityBridge product team instantly issues signature updates that allow customers to monitor for potential exploits of yet unpatched vulnerabilities.
However, as no patch is available for a zero-day, there are a few other things that you need to consider:
- Inventory of attack vectors
Knowing your attack surface overall is important and serves as the foundation for further countermeasures. It also helps organizations to understand their individual risk situations. - Reduce the attack vectors
Any connection point such as the previously mentioned SAP Internet Communication Framework (ICF) services that are not used or needed, shall be deactivated. Also, ensure to sufficiently harden all touchpoints with untrusted networks or the public internet. - Software Components
that do not serve a distinct purpose, shall be uninstalled or at least deactivated. Most of the SAP customers still run at least one SAP NetWeaver system where the client 066 exists, which is not needed anymore but until recently was shipped with the standard installation. There are various other examples that SecurityBridge instantly identifies after being installed. - Surveillance of change
Whenever a new service is enabled or introduced, there are security considerations to make. SecurityBridge helps customers do monitor any change to the attack surface. Those changes are immediately reflected in the overall SAP security posture. - Threat detection
The recent Log4j incident but also the somewhat older RECON release have impressively proven that vulnerabilities can exist for a long period of time without being noticed. Detection of malicious and monitoring of action with impacts to the SAP system security are key elements to protect against severe damage. - Layered security
Introduce additional security layers. Besides precise hardening, patching, and monitoring it is beneficial to consider adding intrusion preventions systems and network segmentation based on your individual risk situation.
How to reduce the SAP attacker surface?
This is not an easy task and especially becomes difficult for SAP organizations that expand their digital footprint and embrace new technologies. Reducing means
- Deactivation of services of SAP Internet Communication Framework (ICF) and Internet Communication Manager (ICM)
- Deinstallation of unused software components
- Deletion of unused or obsolete RFC Destination and service endpoints. Those in use need to be sufficiently hardened
- Elimination of trusting (SMT1), which is not needed
- Deletion of SAP clients that are not used
- Governance and tracking of SSL certificate handling in SAP (STRUST)
- And many more…
It may be a fine line between accepting the risk and fulfilling the business department’s wish for a new service. This is especially true if the new service only adds additional comfort but comes with a very specific risk. And this already describes the one challenge to master – many SAP experts do not have the classification of benefit versus SAP security impact at hand – the moment they evaluate a request for change. SecurityBridge provides the missing piece of information by a sophisticated classification system that sets the likelihood of exploitation in perspective.
The previously described scenario applies to a particular change, and mainly connects to the security governance model that needs to be in place to ensure the attack surface of SAP does not increase. Taking a step back and looking at the overall surface of an existing system or an entire landscape is a lot more complex. It typically requires an extensive assessment phase before dependencies and other environment-specific considerations, like the existence of additional security layers, can be made. Additional security layers can be introduced by network segmentation, intrusion prevention systems contained in intelligent firewalls like the FortiGate by Fortinet.
Conclusion
Next week Tuesday, like every 2nd Tuesday of a month, SAP customers will see new security patches. It is very likely that some of the security updates released will again force you to patch severe vulnerabilities within your enterprise critical SAP applications.
If services are impacted that are deactivated, the risk of exploitation is typically reduced – hence often the deactivation of an impacted service is mentioned as a workaround for those that can’t install the patch.
Log4j has hit many organizations and also SAP customers unprepared. Be aware this can happen any time again, better assume that this will happen and form your security strategy adequately.
“SecurityBridge is committed to supporting our ecosystem of partners to continue our fast company growth. Our partners bring us the scale we need with their extensive customer relationships and substantial technical expertise that ensures customer success.”

Christoph Nagy
CEO SecurityBridge