Get a grip on SAP Interface Security

Chapters
Share Article

When SAP introduced their ERP solution R/3 back in the 90s, it was a monolithic solution. While the concept of having a line of systems consisting of a development, a QA and a productive system was already in place, little to no interfaces to other systems were needed. Since then, a lot has changed. Not only did SAP introduce new modules and standalone solutions, which also needed to connect to the “core” ERP system, with the rise of the internet, SAP systems were more and more connected to legacy systems as well as to the web.
Today, interfaces between SAP systems and other systems have increased in numbers to the point where it is literally impossible to keep track of all connections. A little anecdote to highlight the point: an SAP customer wanted to know how many interfaces there were for a specific system. They asked their administrators to estimate the number of interfaces to and from the system – guesses were around 15-20 interfaces. When that customer evaluated the landscape, they found more than 60 interfaces just for this single SAP system!
Securing your SAP landscape is no longer optional. Security shall be unavoidable but workable, a core requirement within today’s interconnected world. For this reason, SecurityBridge is designed to be always on, 24/7.
SAP Interfaces
As we well know, not knowing your interfaces is a nuisance when, for example, an old system is shut down and processes are disturbed as there was with this one interface which shuffled important data. But, more importantly, hidden interfaces are a massive risk for your SAP security.
The -well known- interfaces may be vulnerable, too and could become an attack vector. RFC user rights may deteriorate over time, RFC destinations and service endpoints may not be securely configured, access control lists do not properly restrict remote requests, etc. It is therefore of utmost importance to secure all interface channels and to react on changes that impact the secure configuration.
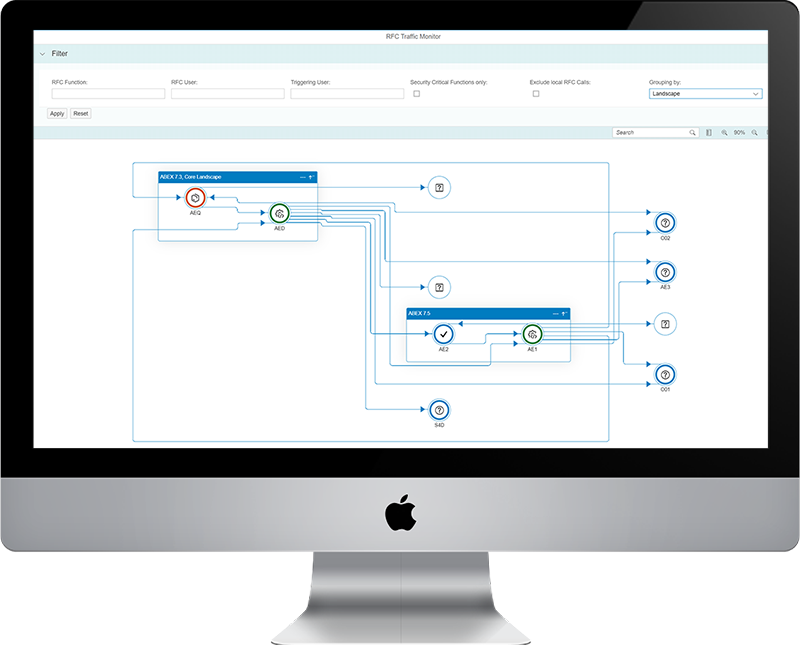
This is why the SecurityBridge suite does not only focus on a static audit of your system. Its Security & Compliance monitor will ensure the system is hardened by validating the system and interface configuration, interface user authorizations and much more. The real-time SecurityBridge Threat Detection acts as a 24/7 gatekeeper. Whenever there is critical interface traffic it will alert and call for automated actions. And to close the circle there is also an interface monitor which visualizes all interface traffic, to easily spot new, unknown or insecure channels.
Digitalisation demands connectivity
With trends like digitalization and IoT leading to even more connected systems, not having an overview of your interfaces poses a major threat to your system landscape – and, eventually, your most valuable data. As a matter of fact, unused, unpatched interfaces are – quite literally – every hacker’s dream, as they point the way to where an attacker really wants to go: the heart of your productive systems.
Besides having an overview of the interfaces, there is another challenge that SAP customers are faced with. SAP uses RFC interfaces to exchange data between systems. Those RFC interfaces are calling RFC function modules for specific requests. In theory, each interface should use those function modules which are required to get the job done only. The reality, however, looks quite different. A high manual effort is involved in selecting RFC function modules, which consequently leads to interfaces that are allowed to access more function modules than are necessary. The fact that RFC interfaces represent only one interface technology among many, complicates matters further.
The security baseline delivered in the SecurityBridge standard ensures you do not require an extensive side project while implementing S/4. Upon installation of SecurityBridge, all security-critical roles and authorizations are instantly monitored.
The Solution
So, what’s needed to overcome these challenges? To start with, an overview of all existing interfaces is required. SAP systems have built-in tools which help, starting with the transaction SM59 which gives an overview of most interfaces for one system. However, interfaces have to be validated on a regular basis and manually checking SM50 in dozens, sometimes hundreds of systems is serious work. What’s needed here is a centralized overview spanning all systems and all interfaces with a centralized dashboard.
The latest addition to the SecurityBridge suite is a fully integrated Interface Traffic Monitor, which visualizes RFC interface connectivity across your SAP landscape. Through a bird’s eye view, security-critical traffic and vulnerable interfaces can easily be spotted.
Secondly, apart from being aware of all interfaces, it’s equally important to know what data is flowing through those interfaces. More precisely, which function modules are used by which interface. Again, some of the built-in standard tools for SAP will support customers in this task, but that involves even more manual effort.
For this reason, SecurityBridge not only validates your interface setup, it also continuously listens to which functions or services are consumed, and from where. Since it knows what to listener for, and yes the platform continuously learns, you will be alerted in case of anomalies or security critical events.
The weakest link breaks the chain
Lastly, those interfaces also need to be properly secured. With interfaces in an SAP environment, many things can go wrong when it comes to security. Storing user and password or using a trusted connection incorrectly are just two examples when it comes to RFC, any of these mistakes will make it possible for an attacker to “hop” from system to system. And hardening interfaces is, again, time consuming cumbersome work.