
SAP Patch Day: Essential Security Advisories for SAP
Chapters
Share Article
Key Takeaways
SAP Patch Day occurs monthly on the second Tuesday, providing critical updates that safeguard organizations from vulnerabilities.
Timely application of SAP Security Notes is crucial for maintaining system security.
Utilizing tools like the Patch Management from SecurityBridge is essential for effectively managing and applying updates.

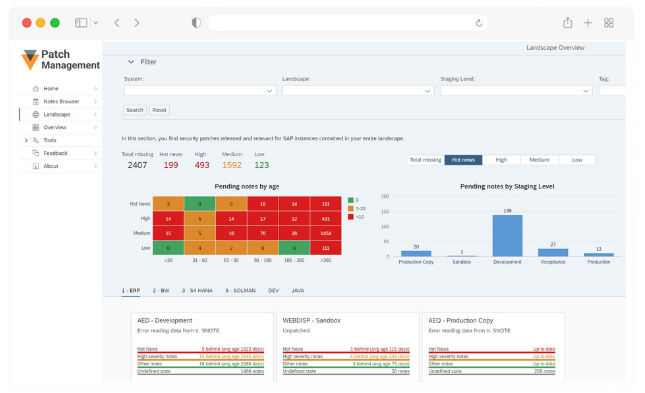
Understanding SAP Patch Day
SAP Security Patch Day includes publishing critical SAP security notes for its product portfolio. Following security notes plays a crucial role in maintaining SAP systems’ confidentiality, integrity, and availability.
Customers can find the SAP Notes for the respective month in Digital Asset Management.
The security notes can be selected in the SAP Support Portal in the ONE Support Launchpad application “SAP Security Notes.”
Schedule and Timing of SAP Security Notes
SAP Patch Day occurs on the second Tuesday of each month, allowing organizations to plan their patch management efficiently. New fixes are released at 9:00 a.m. CET.
How to Apply SAP Security Patches
Start applying SAP patches by identifying the relevant notes for your system. You can automate SAP patch management with SecurityBridge, which gives control over the thousands of released SAP Security Notes by getting insights into their nature, prerequisites, relevance, and impact on your specific systems.
Once identified, apply the patches according to the specified procedures. Staying up-to-date with the latest patches and implementing them promptly allows organizations to significantly reduce the risk of security breaches by hardening the SAP environment.
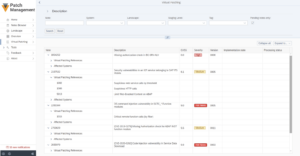
The Critical Risks of Unpatched SAP Systems
Unpatched SAP systems pose serious security risks, exposing organizations to cyberattacks and operational disruptions. SAP is integral to managing business-critical processes, from finance to supply chain, making these systems prime targets for cybercriminals. Failing to apply the latest SAP Security Notes or patches can leave vulnerabilities exposed, leading to data breaches, unauthorized access, and service disruptions. This not only results in financial losses and reputational damage, but also potential non-compliance with regulatory standards, which could lead to additional penalties.
Unpatched vulnerabilities can lead to attacks such as Denial-of-Service (DoS) or information disclosure, and are frequently exploited due to delays in addressing them. Furthermore, vulnerabilities such as missing authorization checks and cross-site scripting (XSS) remain prevalent in unpatched systems. Automated solutions like SecurityBridge Patch Management streamline the process, ensuring that relevant patches are applied promptly and reducing manual workload, thus improving the overall security posture of SAP landscapes. It’s now always possible to implement patches immediately, which is why virtual patching and threat detection of exploitation attempts is crucial.
Insights from Security Researchers
The SAP threat environment constantly evolves, with advanced threat actors, including state-sponsored groups, increasingly focusing on financial gain and espionage through unpatched vulnerabilities. The community is pivotal in identifying and disclosing vulnerabilities in SAP systems. Their insights help organizations understand risks and implement necessary measures to mitigate them.
Resources for Further Information
SecurityBridge Cloud is invaluable for those seeking further information on SAP advisories. Users can access a complete list of SAP Security Notes, ensuring they are always up-to-date with the latest security updates.
Frequently Asked Questions
SAP Security Patch Day is a monthly event during which SAP releases patches to ensure protection against new vulnerabilities. Staying informed about these patches is essential for maintaining robust security.
Timely patching is crucial for SAP systems. It helps mitigate vulnerabilities, thereby hardening SAP systems.
We recommend you look at our Advisory page
A platform such as SecurityBridge is essential for effectively managing SAP security notes and identifying, selecting, and implementing a critical patch.
You should report the vulnerability to SAP via the SAP Trust Center’s Security Issue Management to ensure coordinated vulnerability disclosure.
The SNOTE transaction is a critical tool for applying patches specifically for S/4HANA and SAP NetWeaver ABAP/4. Other Products require different update procedures.
